
Vigilance is more than just practice in an ever-changing cybersecurity arena The cybersecurity community has recently been focusing on three important security vulnerabilities, known as CVE-2023-5043 and CVE-2023-5044, CVE-2022-4886 (the most critical) that are related to the NGINX ingress controller for Kubernetes. Such vulnerabilities are reasoned enough for vigorous vulnerability management as well as comprehensive application security procedures.
Data Visualization of and exploitation in various datasets and in the wild
To discover this and other vulnerabilities exploited in the wild and the data behind it explore
The Crux of the Vulnerabilities CVE-2023-5043 and CVE-2023-5044 and CVE-2022-4886
CVE-2023-5043 and CVE-2023-5044 carry CVSS scores of 7.6, reflecting their high-severity status in the realm of application security. These vulnerabilities are particularly concerning because they can be exploited to execute arbitrary commands and inject code, respectively. Such actions could lead to unauthorized access and potential exfiltration of sensitive data, striking at the heart of an organization’s application security posture (ASPM).
CVE-2022-4886, with a CVSS score of 8.8 (now 6.5) is also part of this triad of concerns, allowing ingress-nginx path sanitization to be bypassed. This could enable an attacker with ingress object access to extract Kubernetes API credentials from the ingress controller—a sobering thought for any application security professional.
“After exploiting the vulnerability, Lace Tempest issued commands via the SysAid software to deliver a malware loader for the Gracewire malware,” Microsoft.
Mitigation and Management for CVE-2023-5043 and CVE-2023-5044 and CVE-2022-4886
In response to these vulnerabilities, mitigation strategies have been swiftly disseminated. For CVE-2023-5043 and CVE-2023-5044, and CVE-2022-4886, the recommended course of action involves updating NGINX to version 1.19 and enabling the “–enable-annotation-validation” command-line configuration. This measure is aimed at fortifying the application security posture against such incursions.
Decoding VE-2023-5043 and CVE-2023-5044, and CVE-2022-4886 and its impact in the wild
Focusing on the most critical vulnerability, CVE-2022-4886
- CVSS (rescored) 8.8 -> 5.5 (addressed)
- CTI – 0 Very low (low use)
- EPSS – 0.00075 (very low)
- Exploit Available remote addressable.
The popularity of the vulnerability has decreased since the publication on the 11 and the initial advisory.
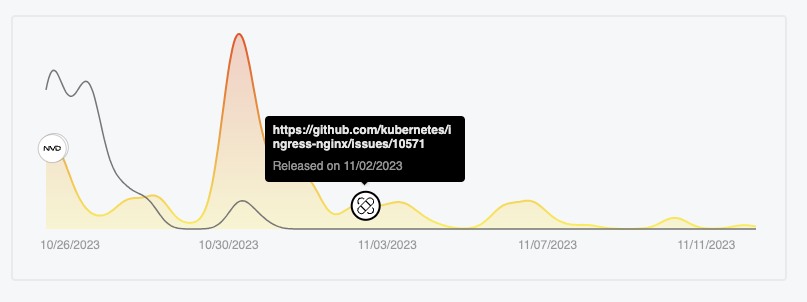
Few mention after the patch and release data
The Bigger Picture in Application Security
The discovery of CVE-2023-5043 and CVE-2023-5044 and CVE-2022-4886 is a stark reminder of the complexities surrounding application security in containerized environments like Kubernetes. As organizations increasingly adopt Kubernetes and NGINX for their operational flexibility and scalability, comprehensive ASPM solutions become paramount. These solutions must be capable of not only identifying and mitigating known vulnerabilities but also providing visibility and control over the entire application stack.
How Phoenix Security Can Help

Phoenix Security helps organizations identify and trace which systems have vulnerabilities, understanding the relation between code and cloud. One of the significant challenges in securing applications is knowing where and how frameworks like Struts are used. ASPM tools can scan the application portfolio to identify instances of Struts, mapping out where it is deployed across the organization. This information is crucial for targeted security measures and efficient patch management. Phoenix Security’s robust Application Security Posture Management (ASPM) system is adept at not just managing, but preempting the exploitation of vulnerabilities through its automated identification system. This system prioritises critical vulnerabilities, ensuring that teams can address the most pressing threats first, optimising resource allocation and remediation efforts.
The Role of Application Security Posture Management (ASPM):
ASPM plays a vital role in managing and securing applications like those built with Apache Struts. It involves continuous assessment, monitoring, and improvement of the security posture of applications. ASPM tools can:
- Identify and Track Struts Components: Locate where Struts is implemented within the application infrastructure.
- Vulnerability Management: Detect known vulnerabilities in Struts and prioritize them for remediation.
- Configuration Monitoring: Ensure Struts configurations adhere to best security practices.
- Compliance: Check if the usage of Struts aligns with relevant cybersecurity regulations and standards.
By leveraging Phoenix Security, you not only unravel the potential threats but also take a significant stride in vulnerability management, ensuring your application security remains up to date and focuses on the key vulnerabilities.
Get in control of your Application Security posture and Vulnerability management
Previous Issues of Vulnerability Weekly
- Apache Active MQ
- Atlassian Critical Vulnerability Exploited by nation-state CVE-2023-22515
- Critical vulnerability F5
- How to update curl and libcurl without panic fixing
- Critical Vulnerabilities in Atlassian Confluence: Zero-Day
- Detect & Mitigate HTTP/2: Rapid Reset Vulnerabilities
- Understanding the libcue Vulnerability CVE-2023
- Understanding and fixing Curl and libcurl
- MOVEit Transfer breach, Zellis compromise CVE-2023-34362
Other Useful resources
Data Visualization of vulnerabilities in the wild
- CISA KEV: https://phoenix.security/what-is-cisa-kev-main/
- Exploit in the wild: https://phoenix.security/what-is-exploitability/
- OWASP/Appsec Vulnerability: https://phoenix.security/what-is-owasp-main/
- CWE/Appsec Vulnerabilities: https://phoenix.security/what-is-cwe-main/
















