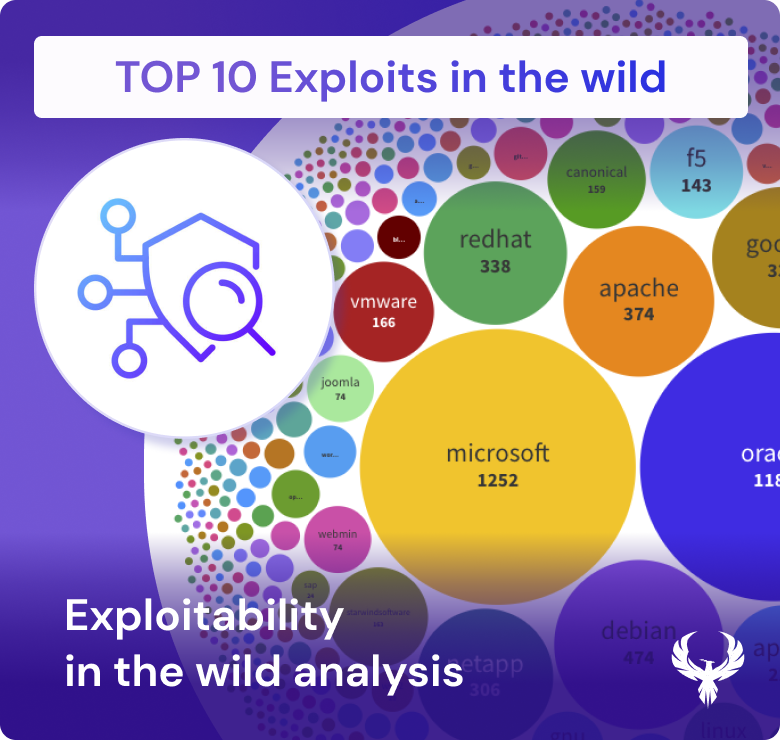
Exploits are the mechanisms that transform vulnerabilities into tangible security breaches, making them a critical focus in the prioritization of cybersecurity efforts. In the intricate landscape of vulnerability management, the key to effective defense lies in understanding not just the existence of vulnerabilities but their potential to be exploited. Threat actors meticulously analyze vulnerabilities, identifying those that offer exploitable entry points into systems. This process often begins with the discovery and documentation of a vulnerability, but what escalates its risk profile is the availability of published exploits, which can be found in widely used tools like ExploitDB, MetaSploit, and Nuclei.
The prioritization of vulnerabilities is heavily influenced by their exploitability, particularly when these exploits are highlighted in tools like the Exploit Prediction Scoring System (EPSS). An EPSS score above a certain threshold—such as 0.5 or 0.6—signals a “high exploited” vulnerability, serving as a critical warning for cybersecurity professionals. This score reflects the likelihood that a vulnerability will be exploited in the wild, guiding teams to prioritize patches and defenses against the most imminent threats.
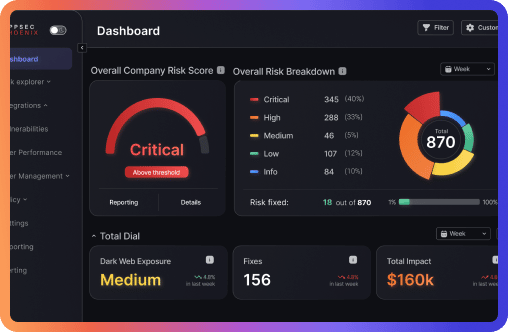
In this ecosystem, the categorization of vulnerabilities by their potential impact and exploitability is crucial. By analyzing vulnerability categories—such as Memory Corruption, SQL Injection, or Remote Code Execution—alongside their exploit data, organizations can better understand which threats are most likely to be leveraged by attackers. This understanding helps in prioritizing mitigation efforts, ensuring that the most dangerous vulnerabilities are addressed first, thereby maintaining a robust and resilient security posture.
In essence, the interplay between exploitability, available exploits, and vulnerability management is at the core of effective cybersecurity. Recognizing which vulnerabilities are most likely to be exploited, and responding accordingly, is vital for safeguarding digital assets against the ever-evolving threat landscape.