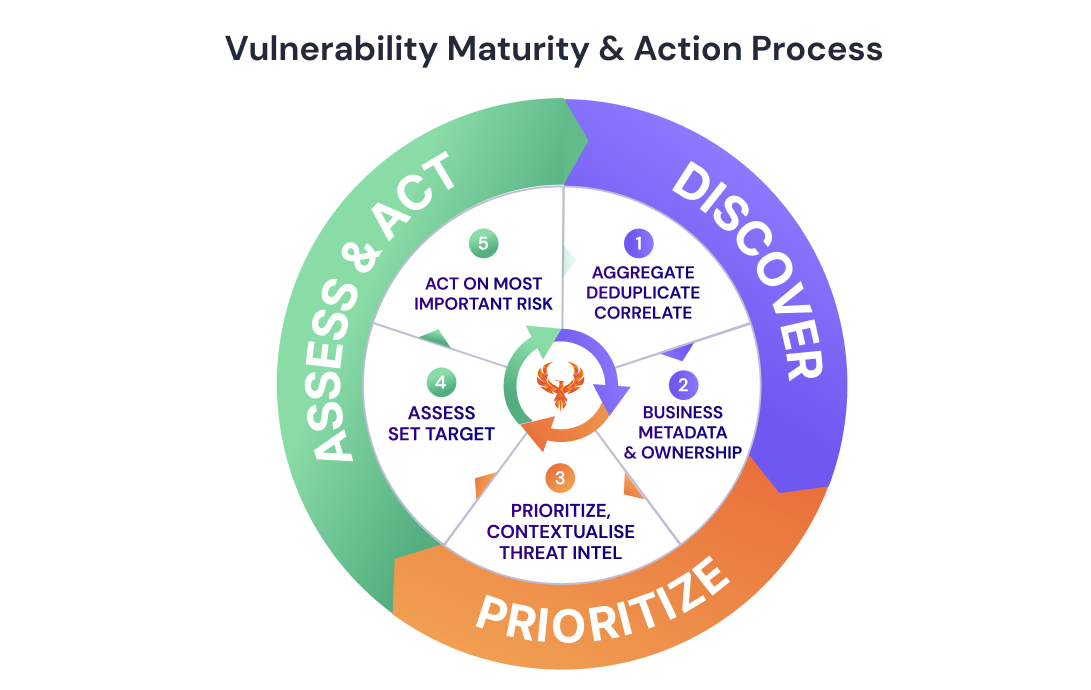
The team at Phoenix Security pleased to bring you another set of new application security (ASPM) features and improvements for vulnerability management across application and cloud security engines. This release builds on top of previous releases with key additions and progress across multiple areas of the platform.
Application Security Posture Management (ASPM) Enhancements
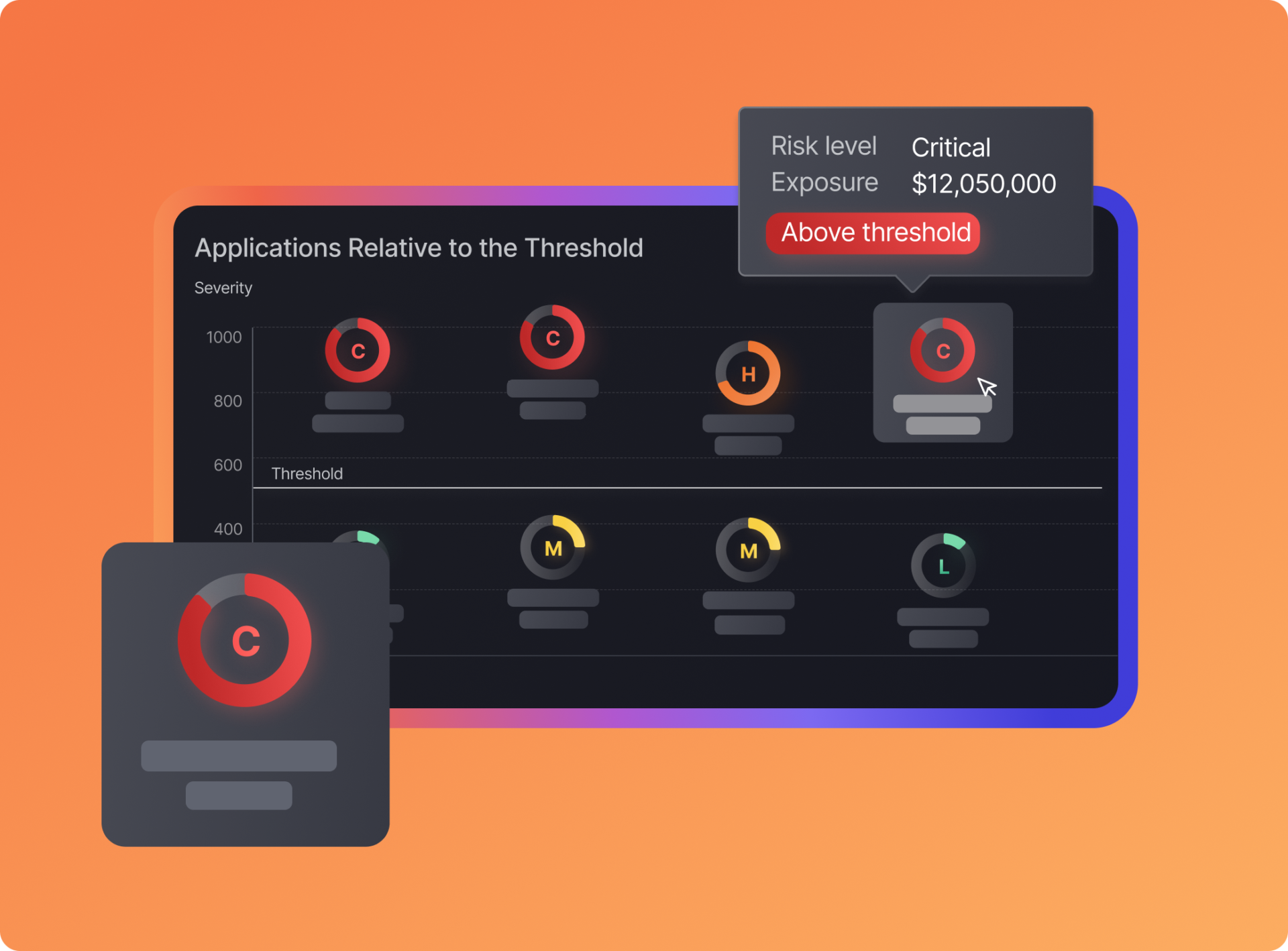
• New Weighted Asset Risk Formula – Refined risk aggregation for tailored vulnerability management.
• Auto-Approval of Risk Exceptions – Accelerate mitigation by automating security approvals.
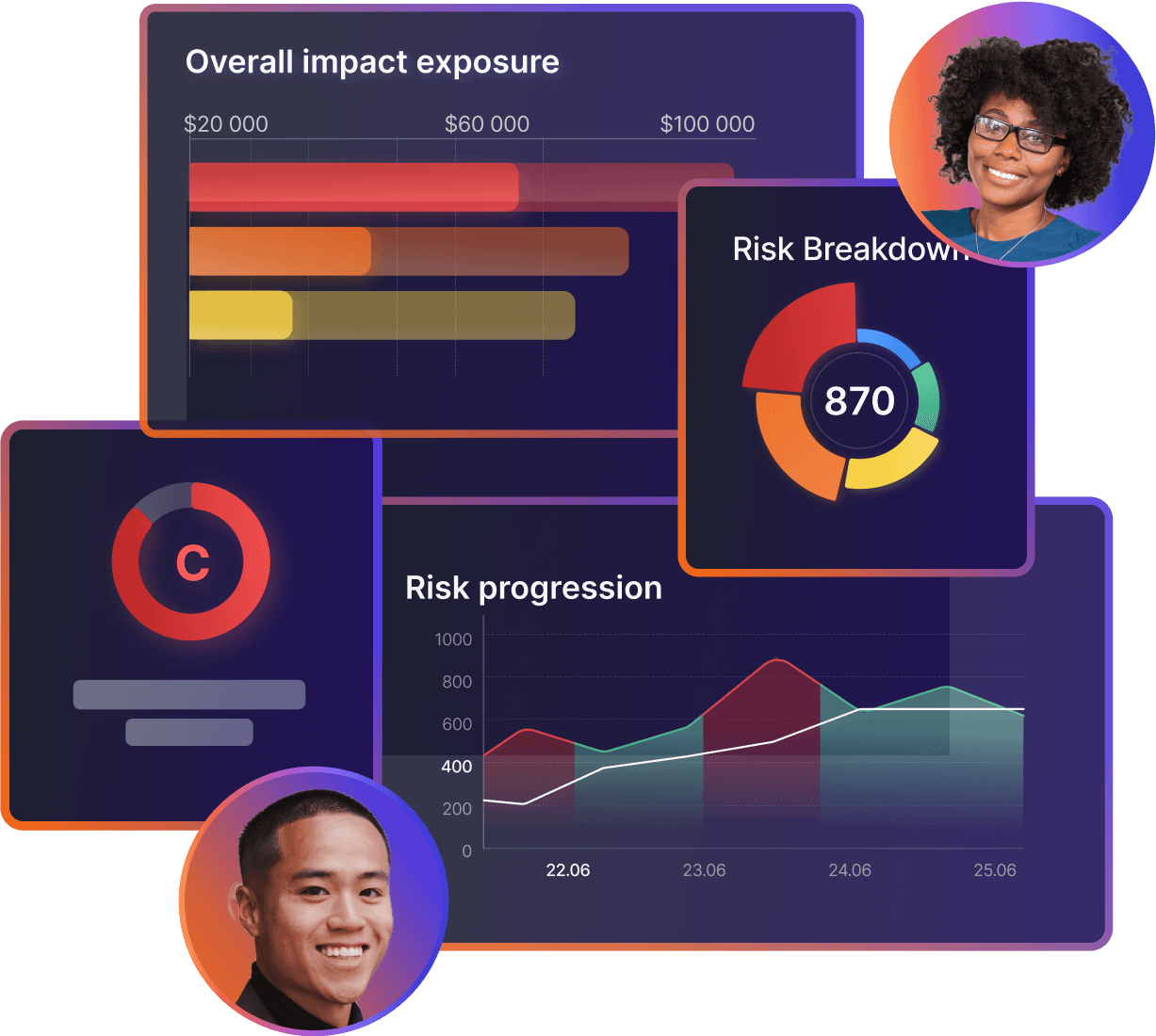
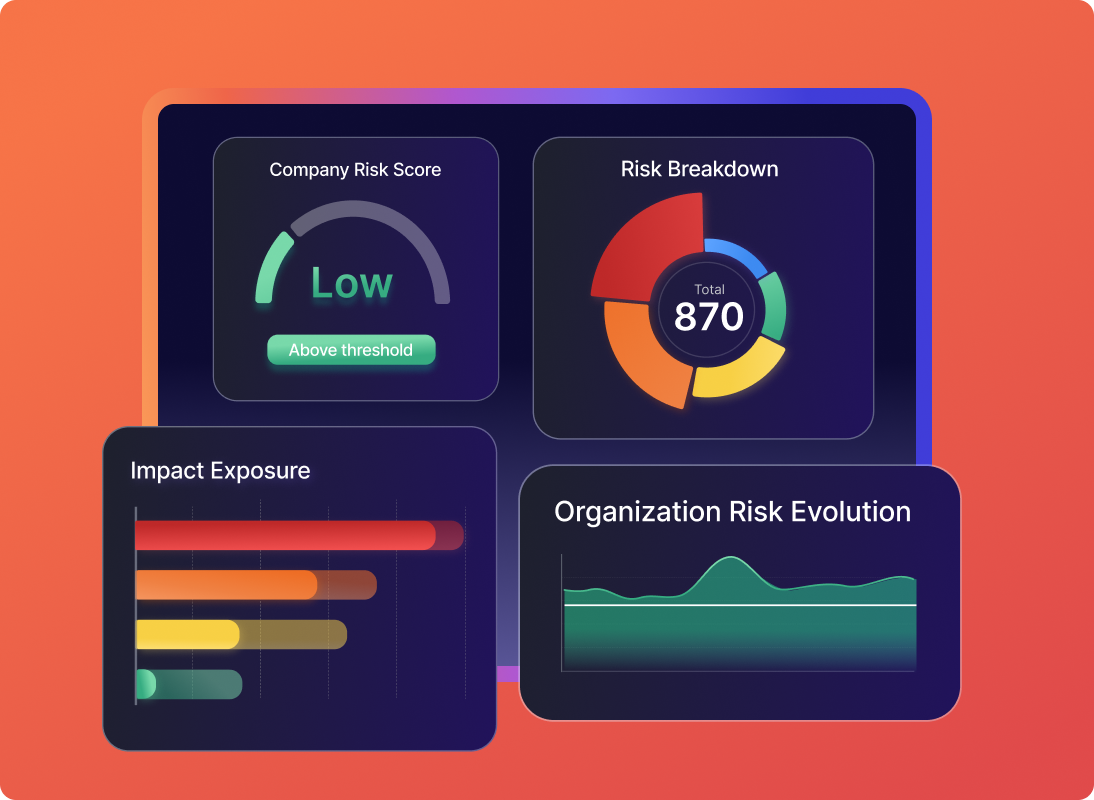
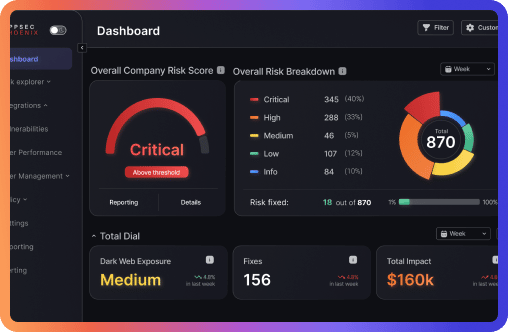
• Enhanced Risk Explorer & Business Unit Insights – Monitor and analyze risk exposure by business units for better prioritization.
Vulnerability & Asset Management
• Link Findings to Existing Tickets – Seamless GitHub, ServiceNow, and Azure DevOps integration.
• Multi-Finding Ticketing for ADO – Group multiple vulnerabilities in a single ticket for better workflow management.
• Filter by Business Unit, CWE, Ownership, and Deployment Environment – Target vulnerabilities with precision using advanced filtering.
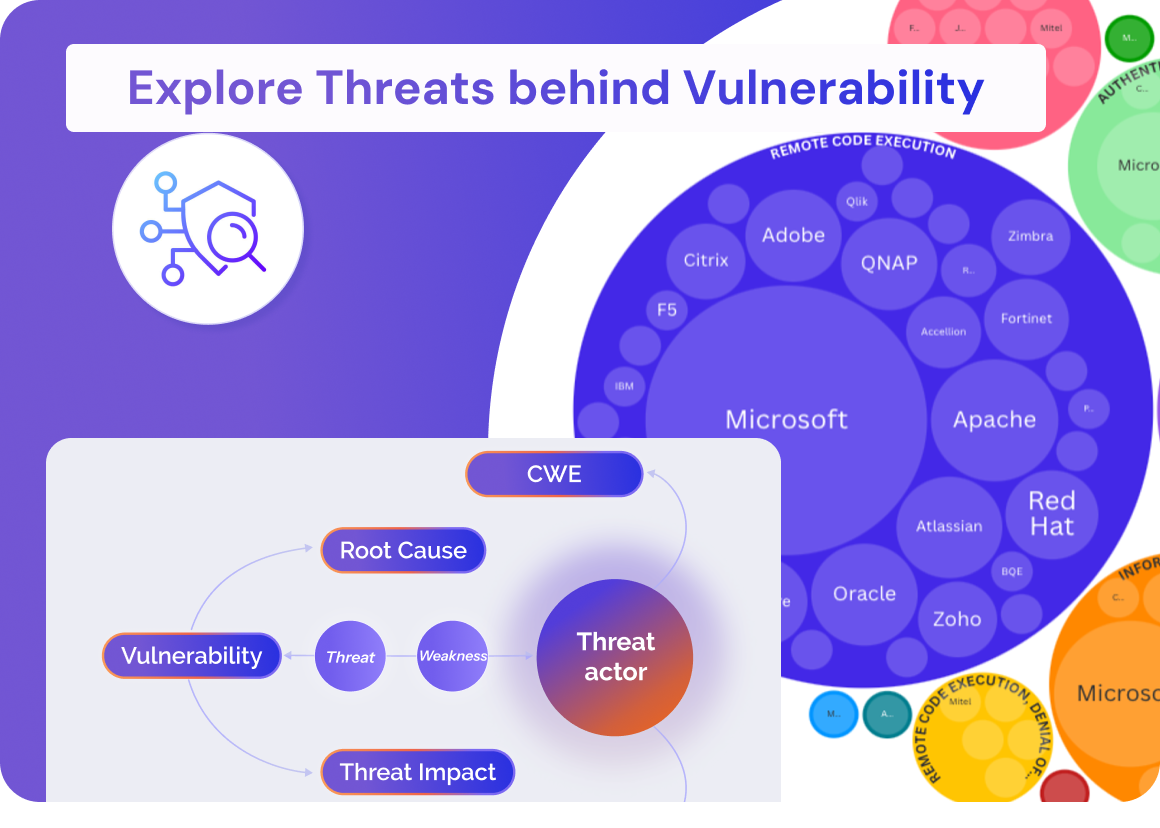
Cyber Threat Intelligence & Security Enhancements
• Cyber Threat Intelligence Premium – Access 128,000+ exploits for better exploitability and fixability metrics.
• SBOM, Container SBOM & Open Source Artifact Analysis – Conduct deep security analysis with reachability insights.
• Enhanced Lacework Container Management – Fetch and analyze running container details for better security reporting.
• REST API Enhancements – Use asset tags for automated deployments and streamline security processes.
Other Key Updates
• CVE & CWE Columns Added – Compare vulnerabilities more effectively.
• Custom Status Management for Findings – Personalize security workflows with custom status configurations.
• Impact & Risk Explorer Side Panel – Gain heatmap-based insights into vulnerability distribution and team risk impact.
🚀 Stay ahead of vulnerabilities, optimize risk assessment, and enhance security efficiency with Phoenix Security’s latest features! 🚀
The team at Phoenix Security pleased to bring you another set of new application security (ASPM) features and improvements for vulnerability management across application and cloud security engines. This release builds on top of previous releases with key additions and progress across multiple areas of the platform.
Application Security Posture Management (ASPM) Enhancements
• New Weighted Asset Risk Formula – Refined risk aggregation for tailored vulnerability management.
• Auto-Approval of Risk Exceptions – Accelerate mitigation by automating security approvals.
• Enhanced Risk Explorer & Business Unit Insights – Monitor and analyze risk exposure by business units for better prioritization.
Vulnerability & Asset Management
• Link Findings to Existing Tickets – Seamless GitHub, ServiceNow, and Azure DevOps integration.
• Multi-Finding Ticketing for ADO – Group multiple vulnerabilities in a single ticket for better workflow management.
• Filter by Business Unit, CWE, Ownership, and Deployment Environment – Target vulnerabilities with precision using advanced filtering.
Cyber Threat Intelligence & Security Enhancements
• Cyber Threat Intelligence Premium – Access 128,000+ exploits for better exploitability and fixability metrics.
• SBOM, Container SBOM & Open Source Artifact Analysis – Conduct deep security analysis with reachability insights.
• Enhanced Lacework Container Management – Fetch and analyze running container details for better security reporting.
• REST API Enhancements – Use asset tags for automated deployments and streamline security processes.
Other Key Updates
• CVE & CWE Columns Added – Compare vulnerabilities more effectively.
• Custom Status Management for Findings – Personalize security workflows with custom status configurations.
• Impact & Risk Explorer Side Panel – Gain heatmap-based insights into vulnerability distribution and team risk impact.
🚀 Stay ahead of vulnerabilities, optimize risk assessment, and enhance security efficiency with Phoenix Security’s latest features! 🚀