Phoenix Security introduces PYRUS, a YAML-native engine connecting code, cloud, and ownership to supercharge ASPM application security vulnerability management. Automate attribution, accelerate remediation, and bring DevSecOps clarity from repository to runtime.

Analyze
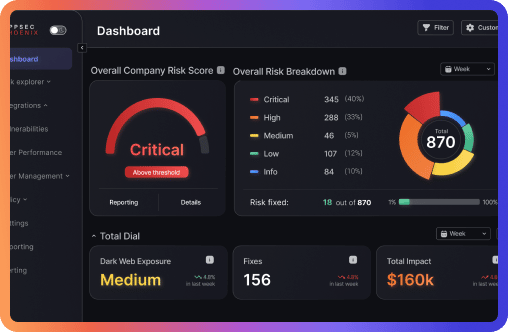
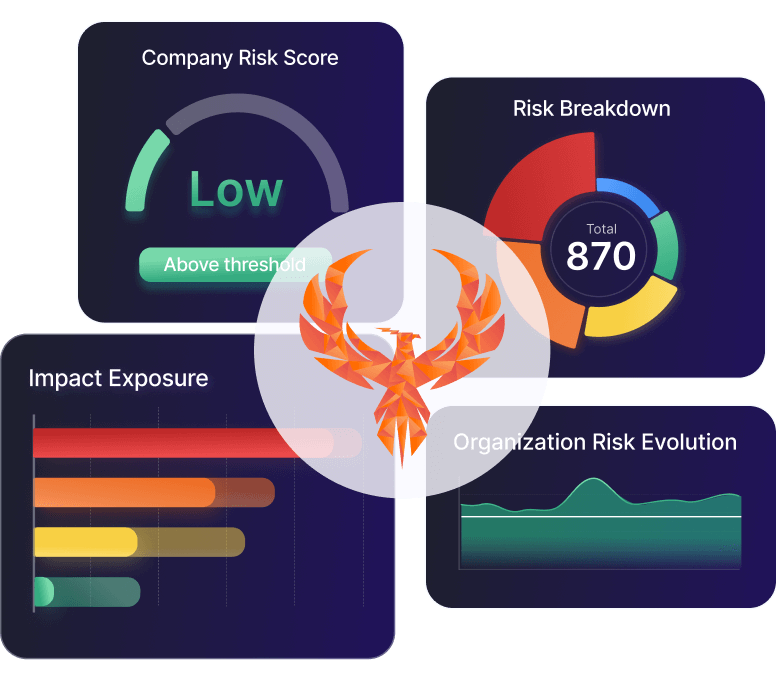
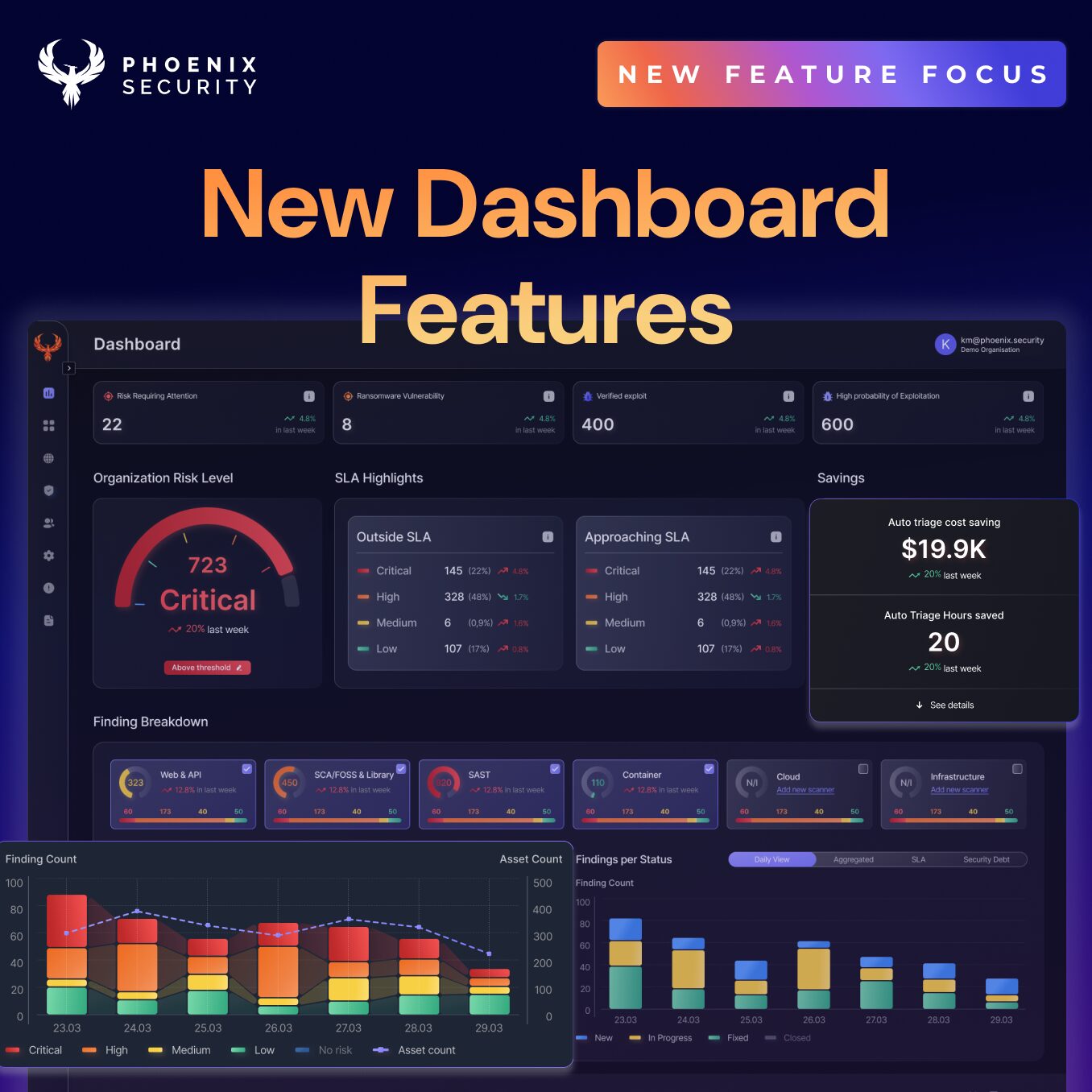
Aggregate, Analyze, Act on Risk
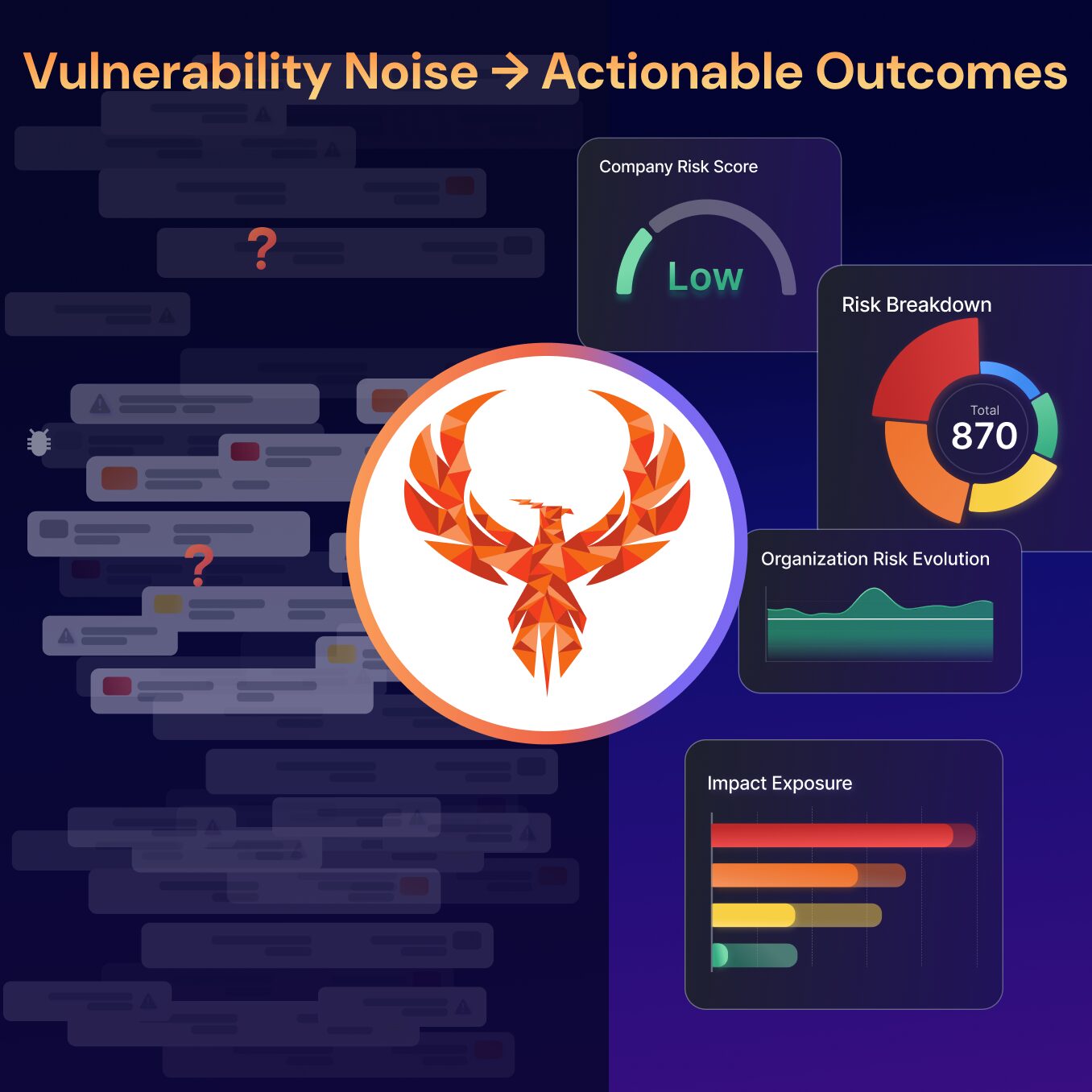
Whilst business executives and the board relates to cybersecurity risk, they don’t understand volumetrics.
Therefore, security teams want to highlight the vulnerabilities that are most important to solve first.
The Phoenix Security platform aggregate appsec and Cloud data, contextualizing, correlating and prioritizing the vulnerabilities and misconfigurations that matter most.
Visualize which software or asset is at the greatest risk, and focus on the vulnerabilities that matter most.
Relationship Appsec and Cloudsec
Correlate, assess and understand the relationship between software and deployment assets in Cloud and on-prem, visualizing how one risk influences another.