Successful defenses need the best tools. But depending on the size of your operation and the type of work you do, finding the best tools specifically for your needs is difficult. Small-to-medium businesses need very different security solutions from enterprises. But how can you pick the correct tool if you’re not sure what your needs are?
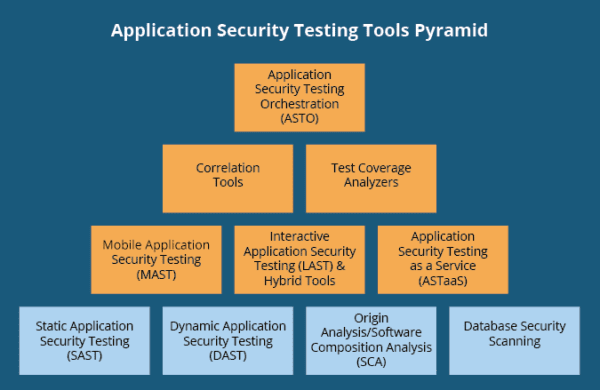
Here are 10 categories of common security tools. Each of them has specific use cases and they are organized into a rough hierarchy.
While some operations implement these tools separately, using centralized, unified security tools such as AppSec Phoenix lets you focus on the main aspects of your job. Let us worry about your cyber-security and you do what you do best.
Security Testing Tools
Table of Contents
- 10 Tools To Empower Your Security
- Tier 1: Foundational Tools
- Tier 2: Intermediary Tools
- Tier 3: Advanced Tools
- Tier 4: ASTO
- Which Application Security Tools Are Necessary For My Needs?
10 Tools To Empower Your Security
These 10 types of tools are separated into 4 tiers. Depending on the software that you develop or use, you may not need a tool from every category. Understanding how they defend applications and code is necessary for understanding how you can manage threats to your organization.
Tier 1: Foundational Tools
- DAST
Dynamic application security testing tools are the black hat’s weapon of choice in the foundational tier. By analyzing a piece of software while it is working, DAST tools work much like a pentester trying to illegally gain access.
They are limited in what they offer, but the two-part crawler/detection processes give an excellent insight into how your software could be exposed by hackers in real-time.
Used under the assumption of no prior knowledge about a piece of software, they identifying vulnerabilities by:
- Scanning for authentication issues
- Identifying areas where data injection could happen
- Presenting issues in the user interface which could be exploited
- Spotting opportunities for session-jacking (or cookie-jacking) in web applications
- Finding scripting errors that could expose
- DSA
Database security analysis tools automate the updating process. Instead of searching manually for patches or hoping that your software providers aggressively push for updates, a DSA checking your current software for vulnerabilities that have known, published fixes.
Although a very basic tool, it saves a huge amount of time for security professionals. Using a DSA effectively could have stopped thousands of companies from being affected by the WannaCry ransomware – Microsoft had already released the update to patch the vulnerability, but a staggering number of organizations had failed to implement it.
- OA/SCA
It’s not enough to know where your software came from. Because programmers often reuse sections of code to save on development time, poorly constructed and exploitable sections may make it into otherwise secure applications.
Origin analysis (as the name suggests) analyzes software and web applications for the origins of all included code. These tools are sometimes also called software composition analysis tools. This is especially useful for identifying reused components and potentially vulnerable libraries and signposting out-of-date or vulnerable code.
Using the NIST Vulnerability Database, OA/SCA tools draw on a centralized database to keep one step ahead of hackers.
- SAST
DAST’s white brother, static application security testing tools analyze software and web applications when all relevant information is available. Used to identify errors in the code in libraries and binaries, SASTs are necessary after a breach to understand how DDoS attacks or data leaks occurred.
Used under the assumption of no prior knowledge about a piece of software, they identifying vulnerabilities by:
- Detecting numerical errors, such as accumulated errors or single-step relative errors
- Identifying race conditions that expose paths to data
- Searching for numerical errors when the software is at risk
Tier 2: Intermediary Tools
- ASTaaS
With the x-as-a-Service market exploding in the post-Covid world, application security testing companies are quickly getting in on the action. Application Security Testing as a Service isn’t so much a singular tool as an expert team working to assist you.
With the $6.2 billion ASTaaS market expected to rise in value to $13.2 billion by 2025, these tools cover the technically demanding areas of application security. These include:
- API testing to stop hackers from accessing sensitive back-end details
- Penetration testing to identify ways in which malicious actors would gain access to a system
- Risk assessments, preferably quantified to identify urgent security risks
- Static/dynamic analysis to identify weaknesses in the code
ASTaaS tools are most commonly used with traditional applications, so they are necessary for companies producing and using mobile and web applications. As these are common in pretty much all industries today, the utility of ASTaaS tools is only going to increase.
- IAST & Hybrid Tools
Interactive application testing tools are sometimes known as hybrid tools because they mix the best of DASTs and SASTs. As a halfway house between black hat and white hat techniques, they are necessary for teams that need to identify issues in real-life use cases as well as pinpointing how they are exploitable on the back-end.
The main difference between deploying both a DAST and a SAST in favor of an IAST is that hybrid tools are interactive. They work within the application, allowing for a better understanding of how the application reacts when stressed, overloaded, or under attack.
- MAST
Mobile application security testing tools take aim at mobile threats, both from internal and external threat actors. Securing mobile devices in a business environment has become more difficult thanks to jailbreaking, rooting, and other tactics to circumvent restrictions in the software.
Using MAST tools can stop your workforce from:
- Jailbreaking to side-load blacklisted applications
- Gaining root access to gain full control over the device, possibly exposing the mobile device to fatal malware
- Spoofing Wi-Fi to launch an attack on other devices
- Manipulating certificates to escape restrictions
- Accidentally leaking data through poor security settings
In the age of BYOD, managing mobile devices can be extremely challenging for security professionals. MAST tools save time on ensuring compliance, allowing InfoSec teams to focus on the bigger challenges.
Tier 3: Advanced Tools
- Correlation Tools
Any security professional knows that managing and analyzing the number of false positives can take an entire day. Reducing the white noise of false positives is essential to identifying genuine security threats. For that purpose, correlation tools are necessary for large-scale organizations that potentially face real threats every day.
Using the data collected by DAST, SAST, or IAST tools, correlation tools identify patterns and links between the threats that an organization faces. Although they are sometimes built with code scanners, importing data from other tools is necessary for most correlation tools.
When they understand the patterns of threats at the security perimeter, security professionals can act decisively.
- Test Coverage Analyzers
Before organization-wide software rollouts are possible, analysis is necessary to ensure that malware does not make it into the system. For large-scale enterprises, it can be difficult to keep a track of exactly how much of the infrastructure has been scanned.
Using a test coverage analyzer shows security professionals exactly how much an application has been scanned, allowing for easier logging and auditing.
The functionality of the best test coverage analyzers should include:
- Identifying potential vulnerabilities not covered by existing test cases
- Providing an objective measure for how much testing has been completed
- Removing unnecessary test cases in redundant situations
- Running appropriate test cases on all software
- Cloud Configuration Checker
The cloud brings opportunities for businesses to quickly expand and change the way they work to react to an ever-quickening world. But with those opportunities comes increased risk. Cloud computing becomes a compliance and information security nightmare when it isn’t closely managed.
Cloud configuration checkers analyze the way that a company’s cloud solution is secured. Because management of a cloud is very difficult when handled manually, these pieces of software automatically identify, diagnose, and solve security issues that are found before reporting back to the central hub.
Misconfigurations and security risks in cutting-edge cloud technology like AWS and GCP sites are quickly identified, allowing security professionals to quickly handle the problems and make vital corrections.
Tier 4: ASTO
- ASTO
For organizations that need the highest level of security testing, application security testing orchestration tools are often necessary. Integrating tooling across all areas of the software development lifecycle (SDLC), ASTO tools help turn a DevOps team and an InfoSec team into a singular, unified DevSecOps department.
Identified as a separate tool by Gartner in 2017, ASTOs are becoming more common every year. With the widening attack surface and growing risk of threat actors, integrated, real-time security tools are necessary for defending increasingly complex technologies. Differentiating themselves from other tools with runtime protection, they are perfect for emerging technologies that can’t solely be managed on the server-side.
DevOps practices push cutting-edge technology such as client-side software and microservices into the nether zone – traditional DAST and SAST tools can’t manage these services safely, so integrating an ASTO is the only option. Web Application Firewalls (WAFs), bot management (including scoping out malicious bots), and runtime application self-protection RASP) are all necessary components of successful ASTOs.
For large-scale enterprises that specialize in applications that mostly function outside of the traditional perimeter, ASTOs are key. Failing to implement back-end and front-end security measures with runtime protection is asking for malicious threat actors to damage your company.
Which Application Security Tools Are Necessary For My Needs?
Although a general overview of the 10 most common types of security tools may have given you a broader knowledge of what you may need, looking at your infrastructure as a unique entity is important too. When you understand your particular needs and review them concerning your budget, you understand what tools are necessary to onboard.
Alternatively, unified tools like AppSec Phoenix allow small-to-medium-sized businesses to instantly onboard and deploy a variety of security tools at the same time. Unified tools give you all the options of expansive tier four toolkits while also allowing you access to everything useful from tiers one, two, and three.
No matter the tools you are using, we always need to focus on the business context and how threats are prioritized and aggregated. Security tools are only successful when risk trends are analyzed and threat intelligence is effectively implemented. By using AppSec Phoenix, security tools and threat intelligence are augmented in real-time to prioritize vulnerabilities in a risk-based hierarchy.
Danger can be stamped out before it even poses a problem to the security posture – get AppSec Phoenix today to unify your security response.