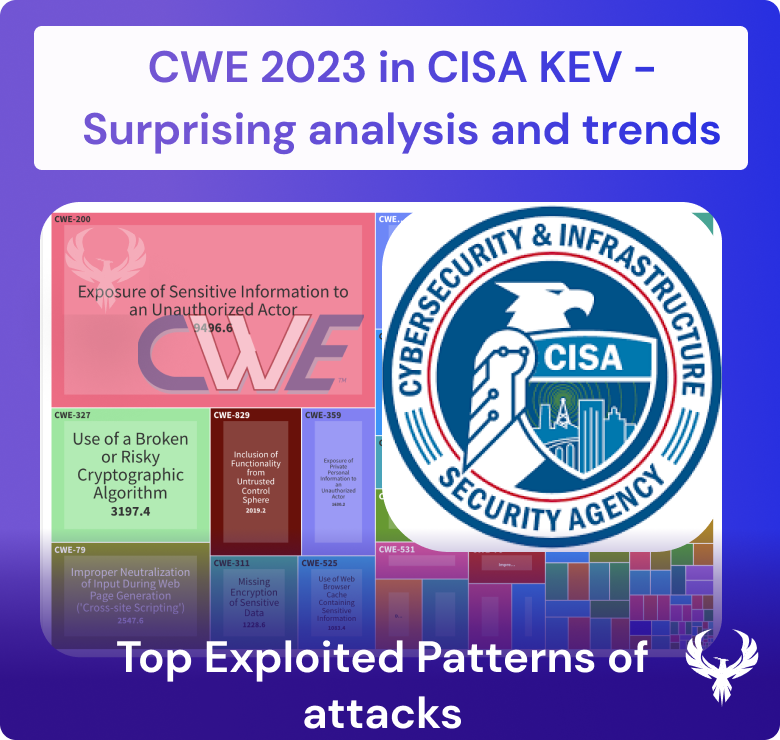
What the heck is ASPM and how modern ASPM address new challenges? In this article we explore Application Security Posture Management (ASPM) and how it has become essential for organizations looking to safeguard their applications throughout the software development lifecycle (SDLC). But what truly defines a modern ASPM solution? In this article, we delve into the typical ASPM vendors, explore edge cases, and outline the fundamental pillars that unite them.
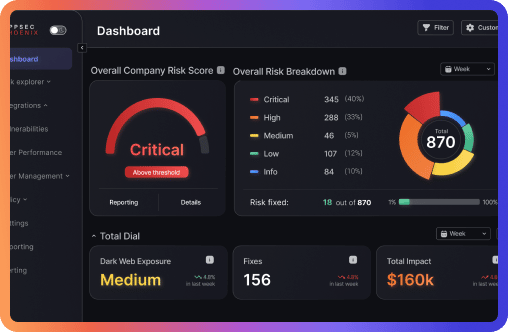
At Phoenix Security, we recognize the challenges posed by diverse organizational structures, making ASPM as much about data and culture as it is about vulnerability management. That’s why we’ve introduced our ONE BACKLOG feature, which merges security champion initiatives with vulnerability workflows into a single, actionable dashboard. This integration empowers security teams to maintain a comprehensive view of vulnerabilities across code, cloud, and other artifacts, streamlining prioritization and remediation efforts.
ASPM is more than just a framework; it’s a proactive strategy that fosters collaboration between development, security, and operations teams. With benefits like unified visibility, risk-based prioritization, and continuous monitoring, organizations can effectively identify and address vulnerabilities, ensuring a robust security posture.
Join us as we explore the future of ASPM, focusing on code-to-cloud native solutions, maximizing existing tools, and nurturing a culture of security that transcends traditional barriers. Learn how ASPM can revolutionize your approach to application security and enhance your organization’s resilience in an ever-evolving threat landscape.