DevSecOps is mature. The discipline has moved beyond buzzwords and now sits at the core of how modern organizations approach software delivery. But one reality keeps derailing its potential: measurement.
Everyone’s measuring something. Few are measuring the right things. And no two teams seem to agree on what “good” looks like.
Engineering wants sprint velocity and fix rate. Security focuses on open criticals and MTTD/MTTR. Leadership expects risk reduction, compliance alignment, and a clean board slide. Meanwhile, the tools—SAST, DAST, SCA, CNAPP, and more—keep pouring in telemetry without context.
The result? A metrics mess. And in that chaos, proper security posture gets lost.
Contents
ToggleThe Problem with Metrics in DevSecOps
DevSecOps promised alignment. It was supposed to break silos and bring shared accountability. But without shared measurement frameworks, it often does the opposite.
- Security leads chase triage accuracy and coverage, often drowning in false positives.
- Developers care about productivity and speed, pushing fixes only when blockers are clear.
- Executives expect evidence of control—quantified and visualized.
Each group is right in their own context, however the metrics don’t speak the same language. What one team considers as a win (reduced backlog), another views as noise (non-exploitable flaws).
This dissonance leaves organizations vulnerable, not from lack of effort, but from misaligned intent.
Gartner’s 2025 Hype Cycle: A Wake-Up Call for Application Security
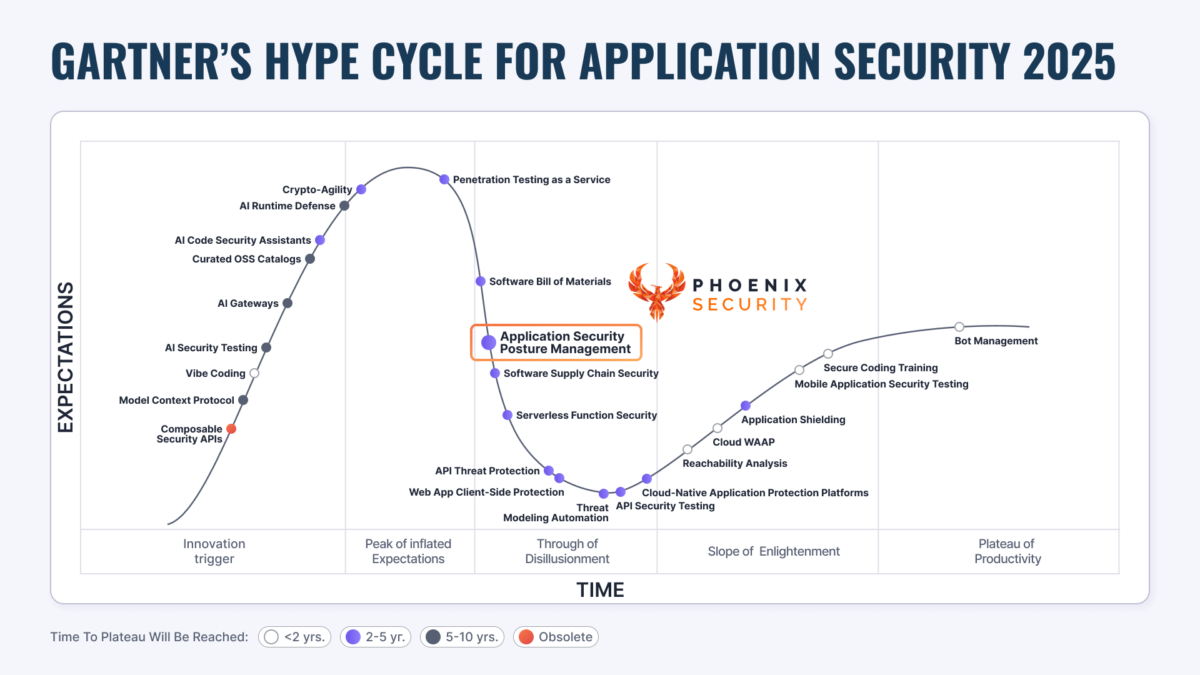
The 2025 Gartner Hype Cycle on Application Security surfaces a concerning truth: application security isn’t just evolving—it’s also fragmenting. AI-driven development, code-to-cloud complexity and tooling sprawl, are creating a tangled mesh of exposure.
Key takeaways:
- By 2026, 40% of organizations will rely on vendors for AI-driven auto-remediation.
- By 2027, 30% of security exposures will stem from vibe coding practices.
- Reachability analysis and ASPM are climbing the maturity curve but need context to deliver real value.
The market is shifting from generic posture management to contextual, actionable risk management. Visibility is no longer enough. Consolidation, correlation, and prioritization are the new imperatives.
Phoenix Security leads this evolution.
European heritage and international outreach the only one ASPM Vendor on the 2025 Hype Cycle
Phoenix Security isn’t just on the Gartner Hype Cycle. It’s redefining what application security means in a world driven by velocity, containers, and AI-assisted development.
1. Embedded Attribution and Ownership Through Enterprise Fabric
Phoenix delivers native ownership by integrating security data where engineering already works. Its autoconfig framework and SDK (see GitHub) bind application identity, service metadata, and team structures into the pipeline.
As per Gartner, security no longer needs to ask: “Who owns this vulnerability?”
Attribution flows through source, CI/CD, runtime, and backlog—automatically.
No guesswork. No triage overhead. Just direct remediation paths aligned with the enterprise structure.
2. Code-to-Cloud Lineage with Reachability Analysis
Phoenix doesn’t stop at just discovering vulnerabilities like Gartner mentions. It tells you if they matter.
With a code-to-cloud model enriched by network-based knowledge graphs and container lineage, the platform:
- Maps external exposure and lateral movement potential
- Highlights runtime reachability for libraries and services
- Shows business-critical impact in plain terms
This is not just risk visibility—it’s remediation clarity in line with the comment from Gartner. Engineers don’t get dumped with scan results; they get a roadmap to fix what’s actually exploitable and impactful.
3. Threat-Centric AI and Agentic Remediation

AI without context is noise. Phoenix Security adds precision.
Its threat-centric AI engine doesn’t hallucinate solutions. It correlates exploitability, exposure, and ownership to recommend targeted fixes—faster than human triage, and often with more accuracy.
What sets it apart:
- Remediation insights enriched with threat intelligence
- Reachability-informed fix suggestions
- Agentic remediation that integrates directly into developer workflows
The result: time-to-remediation drops without inflating cognitive load. Teams fix what matters. Fast.
Real-World Results: From Visibility to Measurable Risk Reduction
Phoenix Security isn’t just theorizing about better metrics. It’s enabling security teams to drive change at scale — across industries, architectures, and application stacks.
💼 ClearBank | Fintech
Outcome: Reduced critical vulnerabilities to single digits.
Impact: Shifted from reactive scanning to measurable remediation velocity across CI/CD and cloud-native environments.
“Phoenix helped us move from noise to precision. We now focus on what truly matters — and fix faster than ever before.”
— Neil Reed, Principal AppSec Engineer, ClearBank
🛍 Bazaarvoice | Retail
Outcome: Dropped critical vulnerabilities to zero and achieved 40% reduction in high-risk issues in just two weeks.
Impact: Container security and engineering workflows are now tightly aligned with risk-based prioritization.
“We didn’t just improve visibility — we eliminated criticals. Phoenix made that operationally possible in days, not months.”
— Nate Sanders, Head of Vulnerability Management, Bazaarvoice
📊 Integral Ad Science (IAS) | Ad-Tech
Outcome: Reduced 78% of container vulnerabilities and 82% of SCA issues, bridging cloud and code into a unified remediation model.
Impact: Achieved full integration of AppSec tooling with cloud posture, aligning engineering, DevOps, and security.
“Phoenix gave us the missing bridge between code and cloud. The visibility is deep, the actions are clear — and the results speak for themselves.”
— Director of Application Security, IAS
DevSecOps Needs a New Language for Risk
“Posture” doesn’t tell you if you’re safe. “Surface” does.
While ASPM platforms delivered much-needed visibility into AppSec operations, the future requires measuring exposure, beyond simply monitoring misconfigurations or vulnerabilities.
This is why Phoenix Security champions a shift — from Application Security Posture Management to Application Surface Exposure Management, or Application Risk Management.
Risk is the currency stakeholders understand. Exposure is the lens engineers need. Metrics that map one to the other unlock the true power of DevSecOps.
DevSecOps Metrics That Actually Matter
The future isn’t about one set of KPIs. It’s about correlated, role-specific metrics drawn from unified truth.
With the Phoenix Security platform, organizations can pivot to metrics that drive outcomes:
| Role | Metrics That Matter |
| Developer | Reachable vulnerabilities by sprint, remediation rate, fix PR velocity |
| Security | True exploitable backlog, SLA breach risk, threat coverage |
| Leadership | App risk score per BU/product, time-to-fix for high risk, ROI of fixes vs exposure cost |
The platform connects telemetry with remediation, context with action, and posture with business priority.
Why Gartner’s View Aligns with Phoenix Security’s Direction
Gartner tracks ASPM, ACSAs, AI runtime defense, and reachability as distinct trends. Phoenix Security sees them as vital components of the same system:
- Unified ownership through enterprise integration
- Runtime-aware reachability as a default filter
- Threat-driven, AI-accelerated remediation as the final delivery layer
Phoenix Security consolidates these innovations, not as point solutions, but as a platform built for application risk management at scale.
Where other tools isolate findings, Phoenix creates decisions.
Rethinking ASPM: From Visibility to Impact
Security can’t be measured in dashboards alone. The value lies in preventing breaches, enabling developers, and preserving velocity while managing risk.
Phoenix Security’s evolution beyond ASPM turns this aspiration into reality.
From attribution to exposure modeling, from AI to agentic automation, from silos to surfaces — the platform brings a unified, measurable and actionable approach to DevSecOps.
It’s time to measure what matters. And fix what hurts.
Let’s stop talking about posture. Let’s start managing risk. Learn how Phoenix Security helps teams reduce noise and accelerate remediation: https://phoenix.security
How Phoenix Security Can Help with Container Vulnerability Sprawl

Application Security and Vulnerability Management teams are tired of alert fatigue. Engineers are buried in vulnerability lists that say everything is critical. And leadership? They want to know what actually matters.
Phoenix Security changes the game.

With our AI Second Application Security Posture Management (ASPM), powered by container lineage, contextual deduplication, and container throttling, we help organizations reduce container false positives up to 98% and remove up to 78% of false positives in container open source libraries, pointing the team to the right remediation

Why Container Lineage Matters:
Most platforms tell you there’s a problem. Phoenix Security tells you:
- Where it lives (code, build, container, cloud)
- Who owns it
- If it’s running
- If it’s exploitable
- How to fix it
All of this is delivered in one dynamic, prioritized list, mapped to the real attack paths and business impact of your applications.
Here’s What You Get:
- Contextual Intelligence from Code to Runtime: Understand which vulnerable components are actually deployed and reachable in production, not just listed in a manifest.
- Noise Reduction with Automated Throttling: Disable inactive container alerts and slash duplicate findings by over 90%, letting your team focus on the vulnerabilities that matter.
- 4D Risk Scoring That Maps to Real-World Threats: Built-in exploit intelligence, Probability of exploitation, EPSS, exposure level, and business impact baked into a customizable formula. No more CVSS-only pipelines.

Vulnerability overload isn’t a badge of diligence—it’s a liability.
Container lineage in Phoenix Security helps you shut down false positives, stop chasing ghosts, and start solving the right problems.
Or learn how Phoenix Security slashed millions in wasted dev time for fintech, retail, and adtech leaders.
















