Washington, DC — November 6, 2025 — Phoenix Security expands its ASPM application security platform with PYRUS, a YAML-native engine that connects ownership, context, and configuration across code, cloud, and runtime. The launch strengthens the company’s position in vulnerability management and DevSecOps automation, unifying attribution and remediation at enterprise scale.
Contents
TogglePYRUS in one line
A YAML-native engine that reads metadata from your repos, clouds, identity, and portals; auto-groups assets by service and owner; and feeds Phoenix Security’s ASPM to route the right vulnerability to the right team — with self-healing configuration when people, code, or environments change.
Why this matters for vulnerability management
Ownership is the throttle for remediation velocity. Scanners can enumerate thousands of issues, yet fixes stalls when teams can’t tell who operates an application, who deploys the container, or which business unit carries the risk. PYRUS encodes that truth where engineers already work — YAML and pipelines — and uses it to form living service definitions: applications, environments, tiers, and maintainers. Security inherits a real-time view of who does what, where; business leaders gain traceability and SLA alignment; and remediation lands with accountable owners on day one. When a service moves, a team rotates, or a tag changes, PYRUS updates ownership everywhere and Phoenix re-routes findings automatically. The outcome is simple: fewer handoffs, less triage, measurable risk reduction.
YAML-based CMDB: how it works
- Declarative ownership. Repos hold catalog-info.yaml/service files that define services, teams, contacts, tiers, and environments.
- Metadata correlation. PYRUS ingests code owners, repo/org metadata, commit activity, AWS/Azure/GCP tags, Kubernetes labels, CI/CD build IDs, identity groups, and enterprise CMDB references.
- Automated grouping. Assets are grouped into services and applications using rules the engineering org controls.
- Attribution & routing. Phoenix maps code, container, and cloud findings to the declared owners, creates tickets/PRs, and tracks closure against SLAs.
- Self-healing. Drift in ownership or environment is detected and corrected through continuous sync, powering automated configuration across Phoenix.
Illustrative YAML
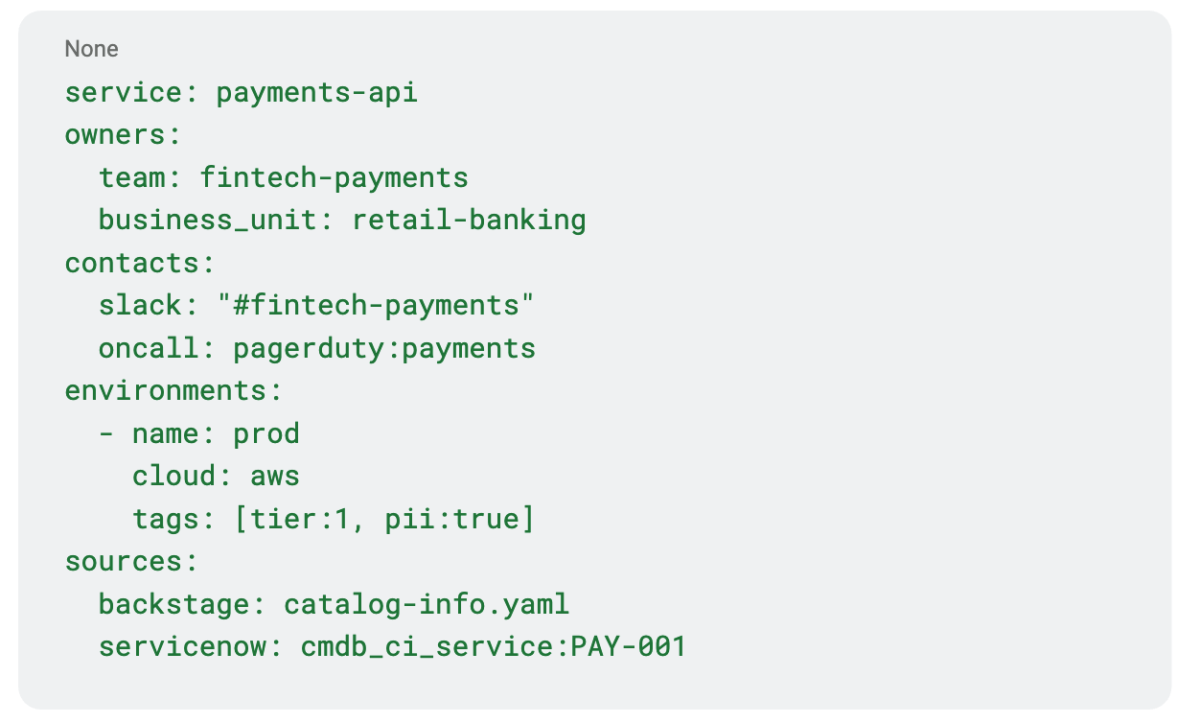
Built for developer reality, not legacy forms
Static CMDB forms and out-of-band spreadsheets drain velocity and fade the moment deployments change. PYRUS meets engineers in PRs and pipelines, not ticket queues. Ownership lives next to the code, and Phoenix reflects that truth back into enterprise systems without manual reconciliation.
Integrations & extensibility
- ServiceNow CMDB — bi-directional enrichment to keep records accurate.
- Backstage — maintainers and system catalog as first-class ownership.
- Okta / Identity — team and role mappings for accountable access.
- GitHub / GitLab / Bitbucket — CODEOWNERS, org metadata, and PR workflows.
- Cloud & IaC — tags/labels from AWS, Azure, GCP, and Kubernetes; Terraform references.
- Open rules & APIs — pluggable translators for internal portals and registries.
Drives Phoenix self-healing and automated configuration
PYRUS is the control plane for Phoenix Security’s self-healing posture: ownership updates propagate through the platform, deduplication and reachability suppress non-actionable findings, container lineage prevents work on images that never ship, and Remediator can open or even propose autofix PRs when policy allows — all tied to the correct owner.
Case-study proof
- ClearBank (Fintech) — Cut container vulnerabilities by 98% (from ~467K to ~8K), reduced contextual duplicates by 90%+, and dropped criticals from 1,470 to 48. Automated team inheritance and code-to-cloud traceability enabled a small security team to support 3× the development community, with multi-million-dollar time savings.
- Bazaarvoice (Retail) — Achieved zero criticals in two weeks and a 40% reduction in high-risk issues by aligning ownership via YAML and developer systems, tightening container security around the teams that ship the code.
- Ad-Tech Enterprise — Removed 78% of active container vulnerabilities and 82% of SCA noise by bridging code and cloud ownership using identity, CI/CD metadata, and container lineage.
Every result shares one principle: automated attribution turns visibility into execution.
Success criteria Phoenix will track with PYRUS
- Ownership coverage — % of assets/services with YAML ownership and synced enterprise records.
- Attribution accuracy — % of findings routed to the right team without reassignment.
- Noise reduction — % decrease via contextual deduplication, reachability, and container version control.
- MTTR — median days to fix for prioritized classes (code, container, cloud).
- Risk delta — quarterly reduction in critical/high risk on business-critical services.
- Workflow adoption — share of PR-based fixes and campaign closures vs. manual tickets.
Executive commentary
“Developers already declare the universe in YAML; PYRUS promotes that truth to the CMDB and keeps it alive,” said Francesco Cipollone, CEO & Co-Founder, Phoenix Security. “When ownership is encoded where work happens, attribution sticks, noise collapses, and teams ship fixes faster — that’s the promise of PYRUS.”
Availability
PYRUS is available today as part of Phoenix Security’s ASPM platform, and the Schema definition is open source available at the following link. Existing customers can enable PYRUS through configuration; new customers can include PYRUS in onboarding alongside integrations for ServiceNow, Backstage, Okta, GitHub, and major clouds.
















