CISA KEV has been a handy tool for vulnerability exploitability information for traditional patching and vulnerability management. But does it work with Application security? Let’s analyse the data leveraging EPSS threat intelligence data
What are the most vulnerable product in CISA KEV Database
In this analysis, I wanted to explore what elements of Application security (libraries and similar) are usable from application security. The research also shows that amongst the number of highly exploitable vulnerabilities in the list, only 42% are highly exploited in the wild, according to EPSS data cross references with CISA Exploitable List.

As cybersecurity experts, we are constantly bombarded with vulnerable data. It is essential to keep on top of the latest available data.
For this research, we have used.
- CVE/MITRE data: https://cve.report/, https://cve.mitre.org/
- CISA KEV Data: https://www.cisa.gov/sites/default/files/feeds/known_exploited_vulnerabilities.json
- Enrichment data from http://cve.circl.lu/
- EPSS Data from: https://api.first.org/data/v1/
One such tool recently gaining popularity is the Common Vulnerabilities and Exposures (CVE) program from the Cybersecurity and Infrastructure Security Agency (CISA). However, more than relying on the CISA Known Exploitable Vulnerability program as a decision point is required regarding application security.
Can you use CISA KEV for Application Security?

The CISA program is an excellent tool for traditional vulnerability management but falls short regarding application security. According to research data, only 3% of CVEs in the database are related to application security libraries and other application security issues. This means that the program provides limited information on the vulnerabilities present in the application code and fails to address the root cause of many potential security breaches.
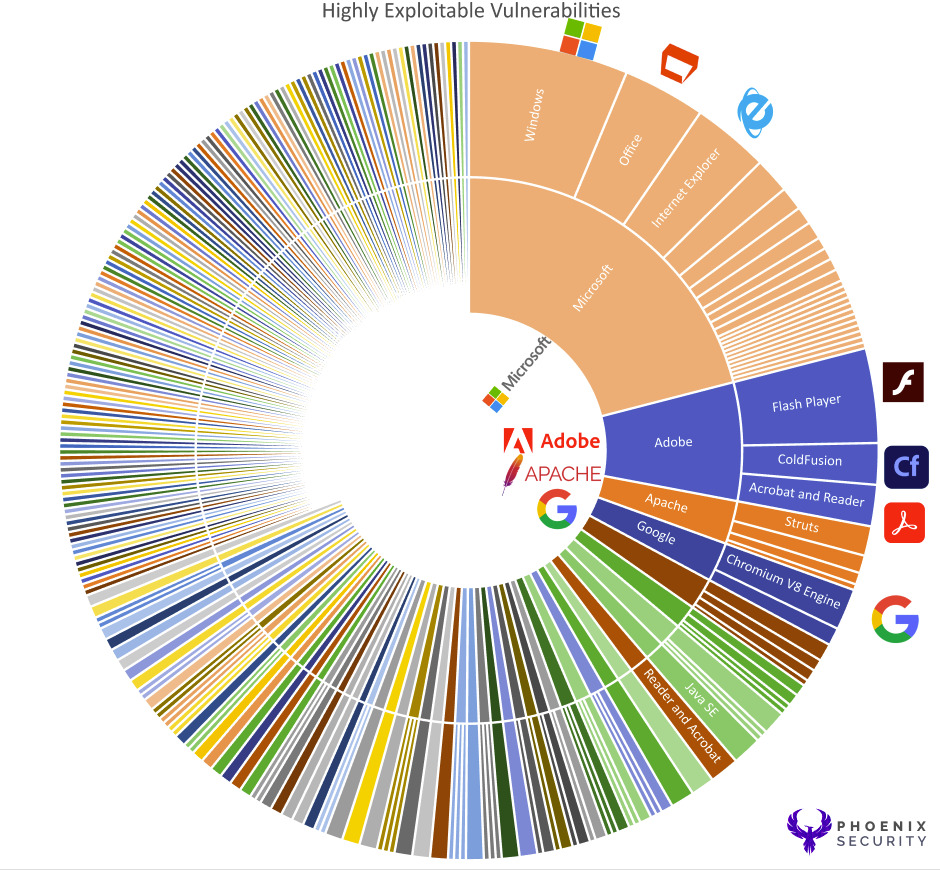
The top vulnerable products remain off-the-shelf even filtering out the top vulnerability data using EPSS and prioritisation based on EPSS. In contrast, Microsoft, Adobe and others are the top vulnerable.

According to recent cross-reference data between EPSS and CISA KEV, 58% of CVEs inKEVdatabase have a low exploitability score from EPSS, meaning they are less likely to be exploited in the wild. Only 42% of CVEs have a high exploitability score, indicating that they are more likely to be exploited in the wild. The EPSS system measures the likelihood of a vulnerability being exploited in the wild.
Note for this analysis, we referenced Vulnerabilities with EPSS value > 0.8
Regulation is linked to KEV, and exploitability vs EPSS data is not mutually exclusive. Both parameters are essential in deciding whether to prioritize one vulnerability instead of the other.
While this system is helpful, it must provide more information to make informed decisions about application security.
Other elements to consider when evaluating the exploitability data is the local context, the externality of the systems/apps, the age of the vulnerabilities and more.

The image below represents the number of vendors (right) with the number of mentions in the KEV) and the number of CVEs with High Exploitability values on the right. The numbers on the Risght display the total number of high exploitable rates CVE per vendor.
This tool provides more information on the probability of exploitation and the potential impact of a vulnerability. It considers factors such as the prevalence of the vulnerability across the organization, the ease of exploitability, and the potential impact of a breach. Using the EPSS system in combination with the CISA program provides a more comprehensive view of application security vulnerabilities. It allows organizations to make informed decisions about where to focus their resources.
| Vendor | Software | CVE IDs |
| Apache | Struts 2 | CVE-2017-5638, CVE-2018-11776 |
| Eclipse | Jetty | CVE-2019-0193, CVE-2019-0194, CVE-2019-0195 |
| Android | CVE-2019-2215, CVE-2020-0104, CVE-2020-0423 | |
| Microsoft | .NET Framework | CVE-2020-0605, CVE-2020-0606, CVE-2020-1108 |
| Oracle | Java | CVE-2019-2699, CVE-2020-14756, CVE-2021-2163 |
| OpenSSL | OpenSSL | CVE-2018-0739, CVE-2019-1551, CVE-2021-23840 |
| PHP | PHP | CVE-2018-14883, CVE-2019-11043, CVE-2020-7066 |
| Python | Django | CVE-2019-14232, CVE-2019-19844, CVE-2020-24583 |
This table is incomplete, and many more software libraries have known vulnerabilities.
However, it’s important to note that relying on either CISA or EPSS as a decision point should not be isolated. Instead, a multi-faceted approach that considers all aspects of application security is necessary to protect the organisation. This approach should include regular vulnerability scanning, penetration testing, secure coding practices, and continuous application environment monitoring.
In conclusion, while the CISA program is an essential tool for traditional vulnerability management, it must catch up regarding application security. Organizations must look beyond the CISA program and use tools such as EPSS in combination with it to get a more comprehensive view of application security vulnerabilities. Additionally, a multi-faceted approach that includes regular vulnerability scanning, penetration testing, secure coding practices, and continuous monitoring is necessary to protect the organisation from potential security breaches.
Future Work
If your organization is actively using sbom declaration, you could pivot on the product id/CPE id and see if you are using any vulnerable libraries or products in the CISA KEV database.
Conclusions
In conclusion, CISA Kev is a useful tool to prioritize traditional software and O/S vulnerabilities, while only a small percentage has it proven useful to prioritize software products. EPSS data and other Cyber Threat Intel have proven more effective in prioritizing application security vulnerabilities. Product-based view and Impact analysis have also proven to be effective in prioritizing the application security vulnerabilities from a risk-based perspective.
Using Chat GPT for data analsys

I’ve tried using some reference data for chat GPT for this research, and currently, Chat GPT seems to receive incorrect data. Below is some data and correctness vs error rate
When asked the question, the majority of answers were incorrect. Always trust a secondary source of data when looking at Vulnerabilities.
| Vendor | Software | CVE | Exploitability Score |
| Apache | Struts 2 | CVE-2017-5638 | 0.975650 |
| Apache | Tomcat | CVE-2017-12615 | 0.974990 |
| Apache | Tomcat | CVE-2017-12616 | NOT in CISA |
| Apache | Tomcat | CVE-2020-9484 | NOT in CISA |
| Eclipse | Jetty | CVE-2015-2080 | NOT in CISA |
| AngularJS | CVE-2019-7339 | NOT in CISA | |
| AngularJS | CVE-2019-7238 | 0.973960 | |
| AngularJS | CVE-2019-6975 | NOT in CISA | |
| AngularJS | CVE-2018-11360 | NOT in CISA | |
| AngularJS | CVE-2016-6986 | NOT in CISA | |
| Guava | CVE-2018-10237 | NOT in CISA | |
| Guava | CVE-2018-10238 | NOT in CISA | |
| Guava | CVE-2018-10239 | NOT in CISA | |
| Guava | CVE-2018-10240 | NOT in CISA | |
| Guava | CVE-2018-10241 | NOT in CISA | |
| Guava | CVE-2018-10242 | NOT in CISA | |
| Guava | CVE-2018-10243 | NOT in CISA | |
| Guava | CVE-2018-10244 | NOT in CISA | |
| JetBrains | IntelliJ IDEA | CVE-2019-14893 | NOT in CISA |
| JetBrains | IntelliJ IDEA | CVE-2019-14894 | NOT in CISA |
| JetBrains | TeamCity | CVE-2019-15843 | NOT in CISA |
| JetBrains | TeamCity | CVE-2019-16877 | NOT in CISA |
| JetBrains | TeamCity | CVE-2020-14198 | NOT in CISA |
| Microsoft | .NET Framework | CVE-2020-0605 | NOT in CISA |
| Microsoft | .NET Framework | CVE-2020-0606 | NOT in CISA |
| Microsoft | .NET Framework | CVE-2020-0646 | 0.974890 |
| Microsoft | .NET Framework | CVE-2020-0608 | NOT in CISA KEV |
| Microsoft | ASP.NET | CVE-2019-1075 | NOT in CISA KEV |
| Microsoft | ASP.NET | CVE-2019-1076 | NOT in CISA KEV |
| Microsoft | ASP.NET | CVE-2019-1077 | NOT in CISA KEV |
| Microsoft | ASP.NET | CVE-2019-1078 | NOT in CISA KEV |
| Microsoft | ASP.NET | CVE-2019-1079 | NOT in CISA KEV |
| Microsoft | SharePoint | CVE-2020-0615 | NOT in CISA KEV |
| Microsoft | SharePoint | CVE-2020-0616 | NOT in CISA KEV |
| Microsoft | SharePoint | CVE-2020-0617 | NOT in CISA KEV |
| Microsoft | SharePoint | CVE-2020-0618 | NOT in CISA KEV |
| Microsoft | SharePoint | CVE-2020-0619 | NOT in CISA KEV |
| Microsoft | SharePoint | CVE-2020-0620 | NOT in CISA KEV |
| Microsoft | SharePoint | CVE-2020-0621 | NOT in CISA KEV |
| Microsoft | SharePoint | CVE-2020-0622 | NOT in CISA KEV |
| Microsoft | SharePoint | CVE-2020-0623 | NOT in CISA KEV |
| Microsoft | SharePoint | CVE-2020-0624 | NOT in CISA KEV |
| Oracle | WebLogic Server | CVE-2019-2618 | NOT in CISA KEV |
| Oracle | WebLogic Server | CVE-2019-2890 | NOT in CISA KEV |
| Oracle | WebLogic Server | CVE-2019-2891 | NOT in CISA KEV |
| Oracle | WebLogic Server | CVE-2020-2555 | 0.957860 |
| Oracle | WebLogic Server | CVE-2020-14645 | NOT in CISA KEV |
| Red Hat | JBoss Enterprise Application Platform | CVE-2017-12149 | 0.974250 |
| Red Hat | JBoss Enterprise Application Platform | CVE-2017-12150 | NOT in CISA KEV |














