Contents
ToggleThe Problem with Ownership and Attribution in Vulnerability Management

Security visibility without ownership is noise. Organizations spend millions on scanning tools but still fail to fix what matters because ownership remains ambiguous. Attribution — knowing who owns what and who fixes what — dictates remediation speed. Yet most teams still rely on manual, outdated CMDBs that are disconnected from modern development workflows.
Developers live in code, YAML, and pipelines — not in legacy databases. Forcing them into static asset inventories breaks velocity and engagement. Security must align with developer reality, not the other way around.
Attribution as the Engine of Speed in ASPM and DevSecOps
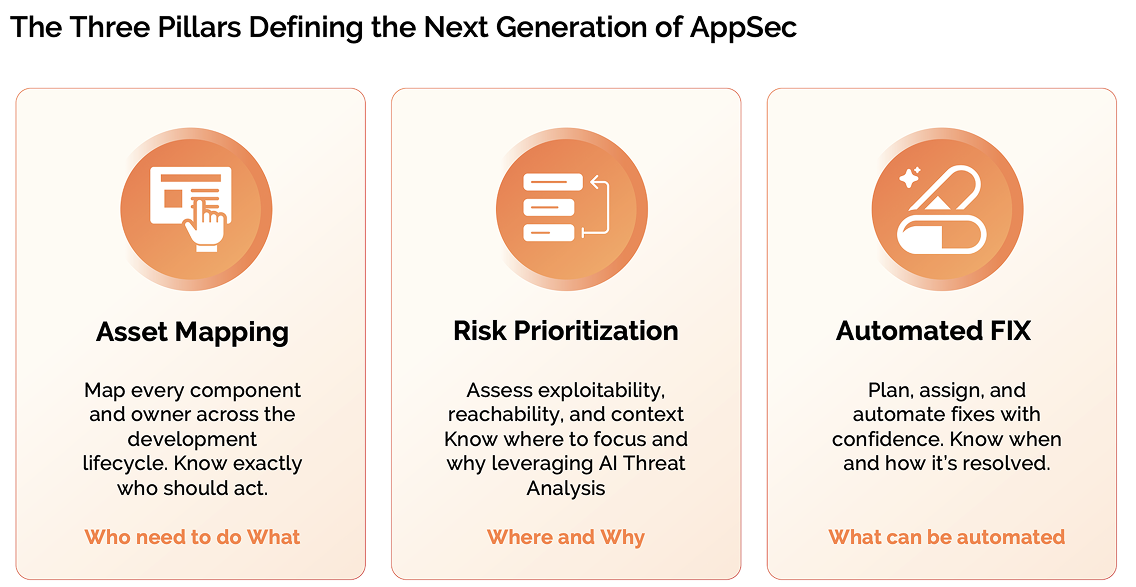
Attribution sits at the heart of Application Security Posture Management (ASPM) and Attack Surface Management (ASM). Without it, prioritization and remediation grind to a halt.
Each vulnerability must have a clear owner and business context — instantly and automatically. When ownership is encoded in the same language engineers use to define infrastructure, remediation becomes native to their workflow.
That’s where PYRUS (Phoenix YAML Resource Unified Sync) comes in — the YAML-native automation layer that unifies business, security, and engineering through metadata.
Redefining the CMDB Through YAML-Driven Automation
Legacy CMDBs were designed for static infrastructure, not cloud-native, multi-repo ecosystems. PYRUS redefines the CMDB using YAML as the declarative source of truth.
Developers declare what they own — applications, services, environments — directly in YAML. The system automatically interprets and syncs those definitions, grouping assets, assigning ownership, and mapping vulnerabilities without manual entry.
This approach transforms the CMDB from a bureaucratic record into a living, data-driven asset map that reflects the reality of DevSecOps delivery.
Why Grouping Assets by Owner and Business Unit Matters in a Cloud-Native World
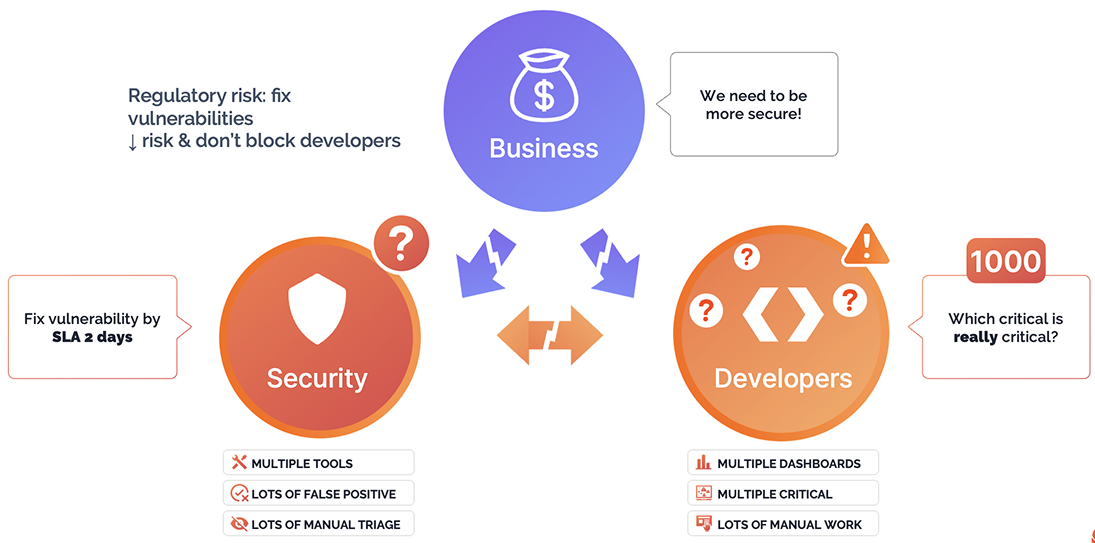
Cloud-native environments change faster than any static CMDB can track. Applications don’t live in one place anymore — they exist across branches, ephemeral containers, distributed registries, and multi-cloud environments that scale and vanish by the minute. Forcing engineers to document ownership in a traditional CMDB built for static servers is a guaranteed failure. The result is an endless disconnect: security teams can’t assign risk, and business leaders can’t see who owns what.
In this reality, Phoenix PYRUS becomes essential. PYRUS uses YAML-native automation and metadata correlation to continuously group assets by owner, service, and business unit — across any environment. Instead of relying on manual data entry, it reads from the truth already present in the enterprise: repository maintainers, ServiceNow records, Backstage ownership files, Okta team structures, and cloud-native tags. This dynamic organization automatically assigns every container, microservice, and environment to its rightful team, no matter where it’s deployed.
Trying to explain to business stakeholders why ownership is fragmented across clusters, registries, and pipelines is a losing battle. The answer isn’t more meetings — it’s automation. By relying on metadata-driven logic, PYRUS builds logical, business-aligned groupings that evolve as code and infrastructure evolve. This creates a shared, living map between engineering and the business — a system where ownership is not just known, but continuously updated, actionable, and measurable.
When teams know exactly what they own, security can finally assign vulnerabilities with precision, remediation becomes an operational flow rather than an escalation maze, and risk reduction becomes an aspiration rather than a challenge.
Measurable Impact — Real Case Studies
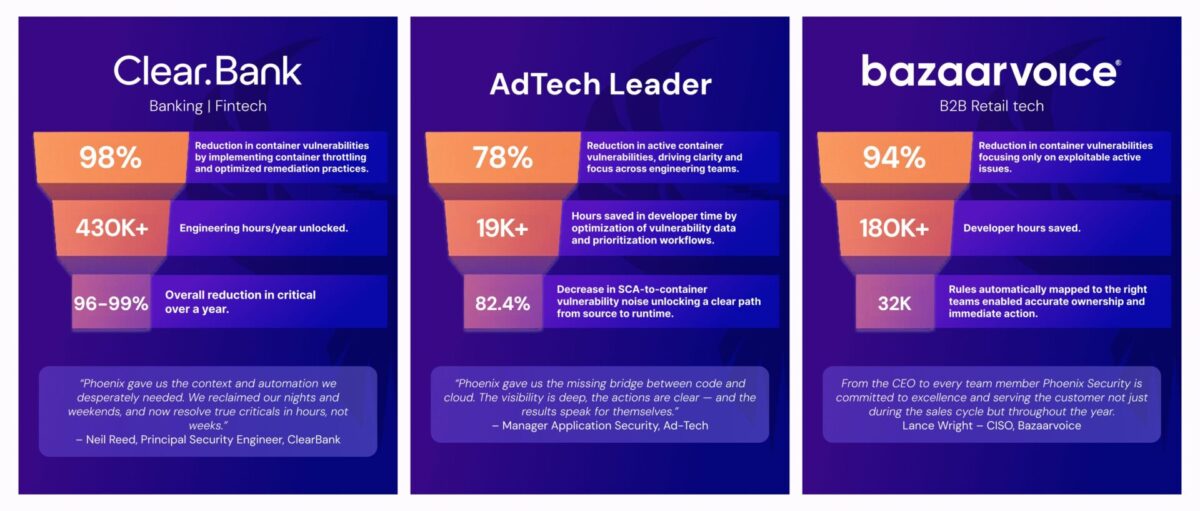
Automation without measurable outcomes is noise. PYRUS delivers proof:
- ClearBank automates the organization of every cloud and software asset, achieving 0 unassigned assets. Through this, they identify noise in containers, and Phoenix security helps eliminate 98% of false-positive, redundant noise. Phoenix also helps get single-digit criticals to the teams and the attribution leads to the removal of 99% critical vulnerabilities, saving $2.6M in analyst time annually – equivalent to four hours per security engineer every week.
- Bazaarvoice automated connection to the identity provider and the developer database to automate the configuration of Phoenix, leveraging Phoenix PYROUS. This led to the eradication of 99% of critical vulnerabilities in two weeks and reduced high-risk findings by 40%, creating immediate alignment between security and engineering.
- An Ad-tech enterprise connected its identity providers and leveraged CI/CD-generated metadata to identify the container lineage and which team generated which service/container. This attribution helped remove 78% of container vulnerabilities while unifying code-to-cloud security visibility.
Every success shared one principle: automated attribution turns visibility into action.
Integrating with ServiceNow, Backstage, and Okta for Unified Ownership
PYRUS integrates seamlessly with both enterprise and developer ecosystems:
- ServiceNow CMDB → Enriches existing records with YAML-based ownership and live engineering data. Keeps ServiceNow accurate without manual reconciliation.
- Backstage → Reads maintainers and system catalog data to map vulnerabilities to the right owners instantly.
- Okta → Aligns identities and access with asset ownership to maintain end-to-end accountability.
- GitHub / GitLab / Bitbucket → Leverages CODEOWNERS, repo metadata, and commit activity to connect vulnerabilities to maintainers.
- Cloud and IaC Systems → Ingests AWS, Azure, and GCP tags and Kubernetes metadata for automated asset grouping.
This integration layer ensures the Phoenix Security platform operates as the connective tissue between enterprise governance (ServiceNow) and developer reality (YAML, code, and pipelines).
Examples of configuration
The following provides an overview of how the team leveraged metadata from different sources to group, attribute and provide business context in a programmatic way.
Application Grouping and attribution leveraging Phoenix Security PYRUS CMDB
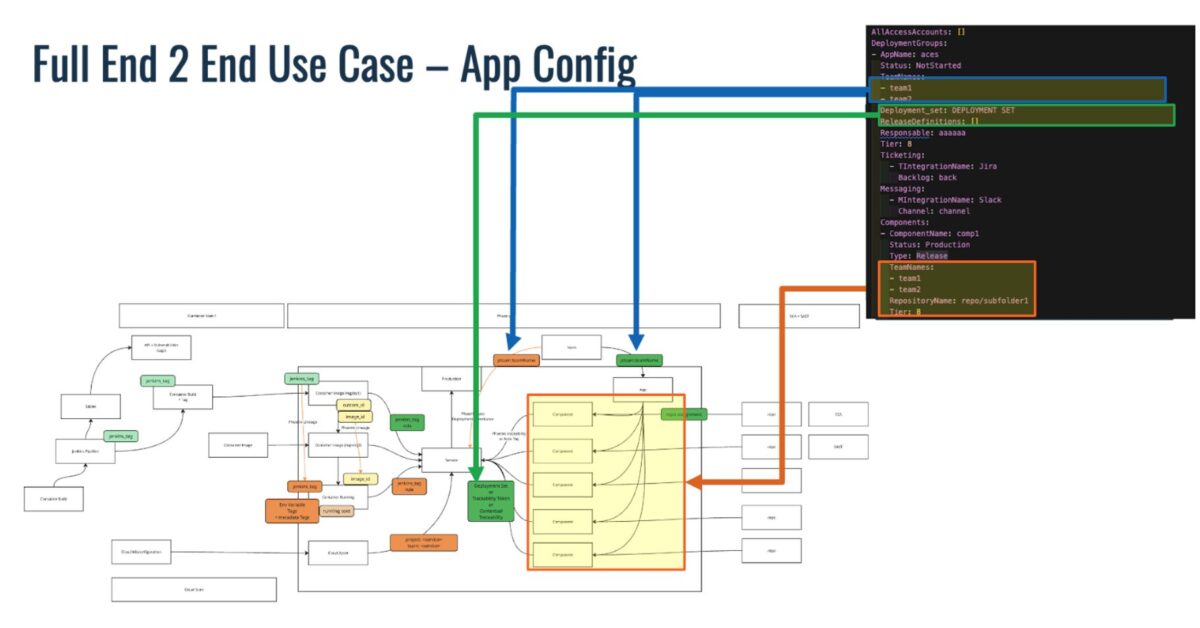
In this scenario, applications are defined and organized using YAML configurations that capture service names, team ownership, tier levels, and deployment groupings.
- Metadata sources: Repository paths, CODEOWNERS, and tags such as SearchName, TeamName, or Tier.
- Automation logic: PYRUS reads the YAML config to dynamically map services and their components across repositories.
- Outcome: Every app and sub-component is automatically linked to its owning team and tier, with the business-criticality reflected through tags like Tier: 8 or Tier: 10.
This removes the need for manual CMDB entries and ensures continuous synchronization between what’s defined in YAML and what’s deployed.
Cloud Service Grouping and attribution leveraging Phoenix Security PYRUS CMDB
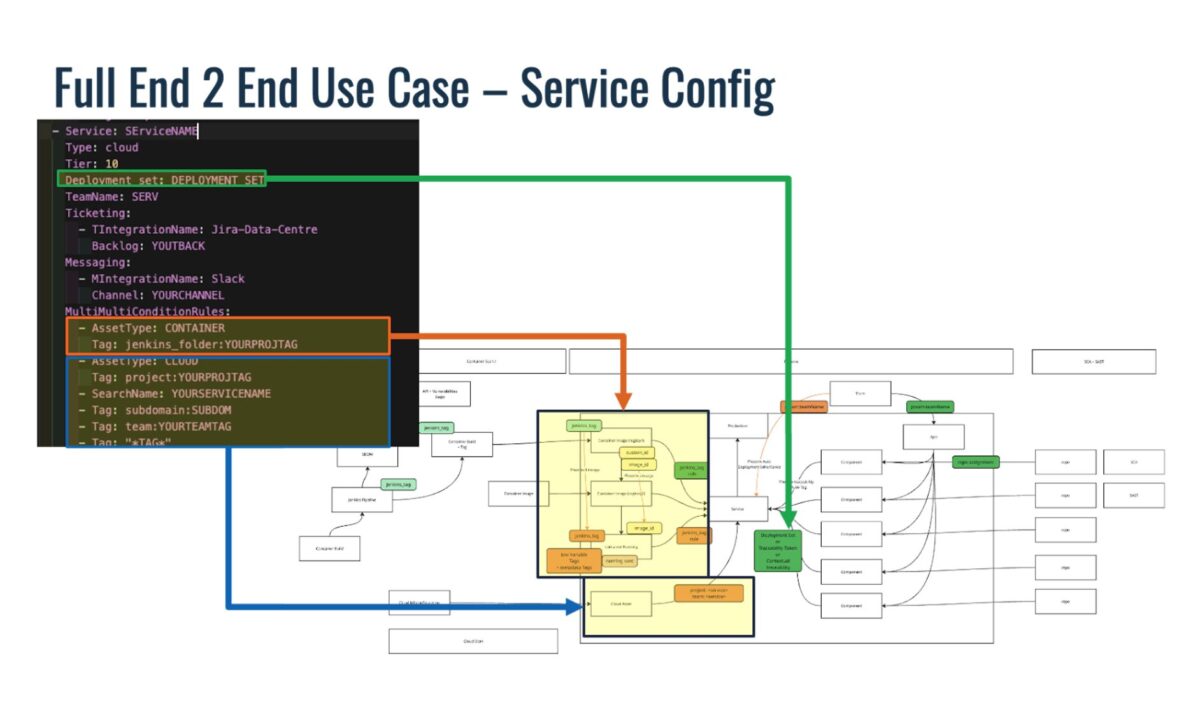
For services, the system leverages CI/CD integration and cloud tagging to associate deployments and infrastructure assets with their logical service group.
- Metadata sources: Jenkins folders, deployment sets, and tags such as project, subdomain, and team.
- Configuration logic: In YAML, fields like AssetType: CLOUD, Deployment_set, and Tag: project:YOURPROJTAG define how services are correlated to their runtime environments.
- Outcome: PYRUS automatically groups cloud assets under the correct service context — even when deployments span multiple environments or pipelines.
This enables security and DevOps teams to see a unified service-level view of risk, ownership, and posture, regardless of how many pipelines or environments exist underneath.
Cloud Service Attributing and organizing containers based on CI/CD build-ID leveraging Phoenix Security PYRUS CMDB
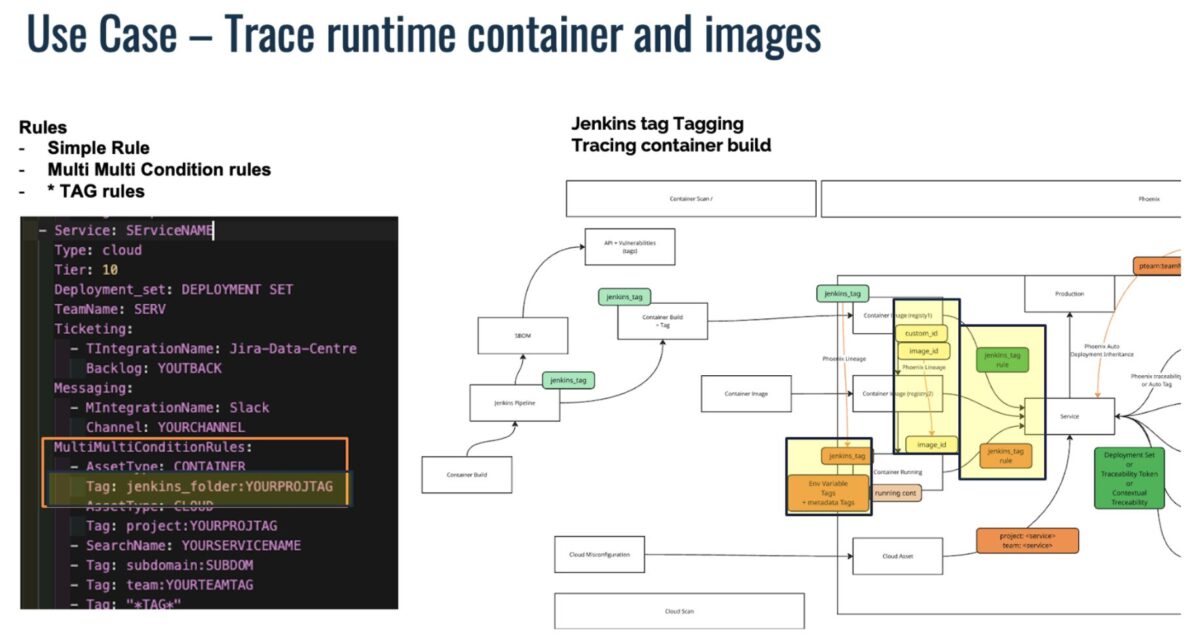
In the container lineage use case, containers and images are tracked across build, registry, and runtime phases using CI/CD-generated metadata.
- Metadata sources: Jenkins pipeline variables, environment tags, and image identifiers (jenkins_tag, image_id, custom_id).
- Configuration logic: YAML definitions include AssetType: CONTAINER and tagging logic like Tag: jenkins_folder:YOURPROJTAG, connecting container images from build to production.
- Outcome: PYRUS automatically links vulnerabilities detected in running containers back to the original repository, build, and team.
This provides end-to-end traceability — from container scan to runtime to remediation — without relying on static mappings or manual CMDB updates.
These three models demonstrate how Phoenix PYRUS replaces static asset management with continuous, metadata-driven attribution, keeping ownership aligned even across distributed cloud-native architectures.
Metadata as the Language of Accountability
Every asset carries metadata — tags, owners, repo names, business units.
PYRUS reads and normalizes that data, creating a real-time ownership map that powers risk attribution and automated routing.
When vulnerabilities emerge, they’re assigned instantly to the correct team based on metadata logic. No manual triage. No guesswork.
The result: mean-time-to-remediation (MTTR) plummets while accountability increases.
Declarative Ownership and Self-Healing Configuration
Ownership drift destroys accuracy. PYRUS prevents it.
Through declarative ownership — ownership defined in YAML and synced automatically — Phoenix Security enables self-healing configurations. When teams change, infrastructure shifts, or metadata evolves, ownership updates propagate automatically across systems.
This powers Phoenix Security’s self-healing and auto-configuration engine, ensuring every vulnerability remains mapped to an active team with the right context and permissions to act.
Extensibility That Matches the Speed of Modern Engineering
PYRUS is config-driven and extensible by design.
Organizations can define their own logic for grouping, ownership, and risk correlation — using YAML or API integrations. Custom translators can connect proprietary developer portals, asset registries, or internal metadata stores without breaking the model.
As architectures evolve, PYRUS evolves with them — staying in sync with pipelines, codebases, and infrastructure definitions.
From YAML to Execution — The Future of CMDB Automation
PYRUS represents a shift from record-keeping to execution.
It transforms static CMDBs into living, YAML-native systems that continuously align business, engineering, and security.
Developers define what’s theirs, security inherits the context, and the business gains clarity on ownership and accountability.
It’s not another tool — it’s the connective layer between ASPM and DevSecOps, where automation meets intent.
Key Takeaways
- Attribution = Speed. You can’t fix what you can’t assign.
- YAML = Truth. Ownership must live where developers work.
- Integration = Scale. ServiceNow, Backstage, and Okta bridge enterprise data with developer context.
- Automation = Trust. Continuous sync keeps teams and systems aligned.
- Outcome = Execution. Faster remediation, measurable risk reduction, and lasting accountability.
Ready to simplify ownership and accelerate remediation?
Explore Phoenix Security’s PYRUS — where YAML meets CMDB automation, and attribution finally matches the speed of delivery.👉 Learn more about Phoenix Security ASPM
















