
The AppSec Phoenix team is pleased to bring you another batch of functional additions and improvements. We are sure that you’ll find these quite interesting!
New Features
- Auto-create Components and Accounts by matching text
- Select Applications and Environments by tag in Risk Explorer
- Link Teams to Environments and optionally to their Applications
- Use MFA Authenticator App
- Infra Asset screen
- Improved navigation from Environments to their Assets
- Community Licence & OWASP Upgrade Functionality
Auto-create Components and Accounts by matching text
Previously you could select to auto-create Components and Account for all the available scanners targets. Now you can be more specific and only auto-create Components from targets that match a specified text.

Select Applications and Environments by tag in Risk Explorer
We are improving the way you can slice and dice the information displayed in AppSec Phoenix. Apart from selecting to see all Applications or Environments in the Risk Explorer, or choosing one of them individually, now you can select the ones that match a particular set of tags. You will see the Overview and List tabs for that subset, the same as when all of them are selected.
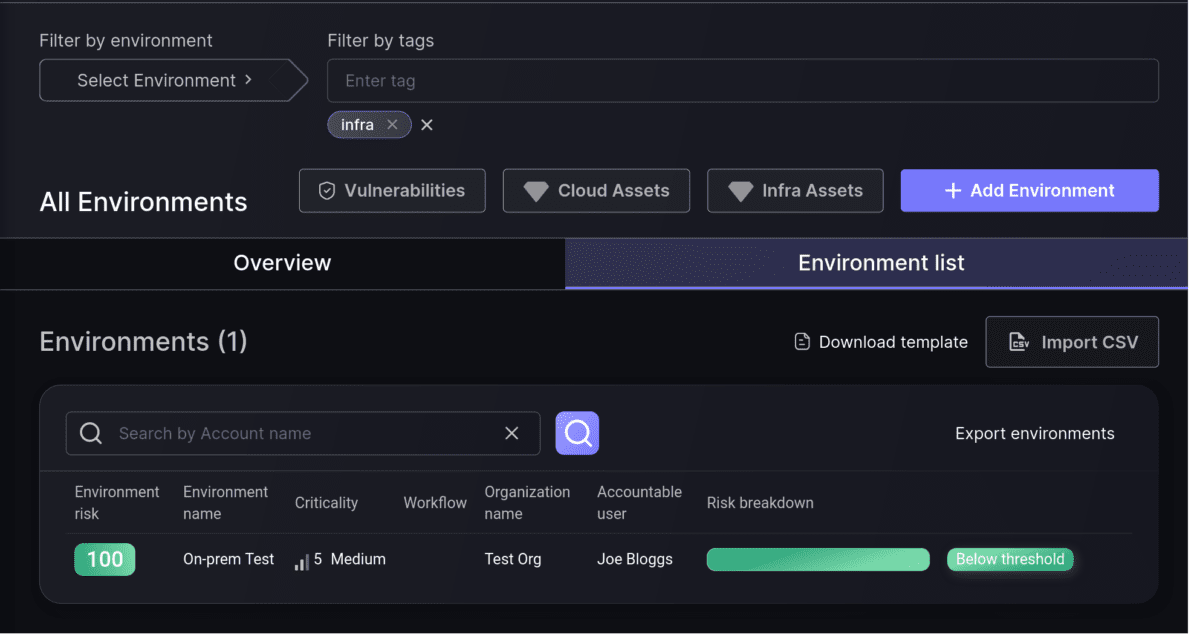
Link Teams to Environments and optionally to their Applications
The best way to control which elements your teams can access is to link them to specific Applications. Now you can link Teams to Environments as well. This will give them access to those environments’ details and, if you choose to extend the access to Applications deployed in that environments, they will see those applications as well.

Use TOTP Authenticator app for MFA
AppSec Phoenix has always strived for robust security when it comes to accessing the platform. Multi-Factor Authentication (MFA) has always been recommended, with SMS as the choice authentication mechanism.
We have added flexibility to the mechanism by allowing you to choose TOTP Authentication apps (e.g. Google Authenticator) as a second authentication factor.

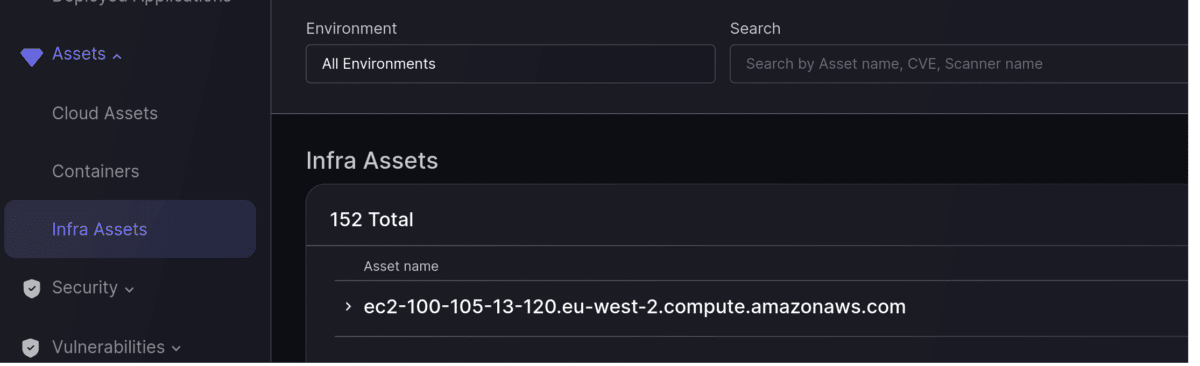
Infra Assets screen
As well as the Cloud and Container asset screens, now you can see all your Infra assets listed in their dedicated Infra Assets screen.
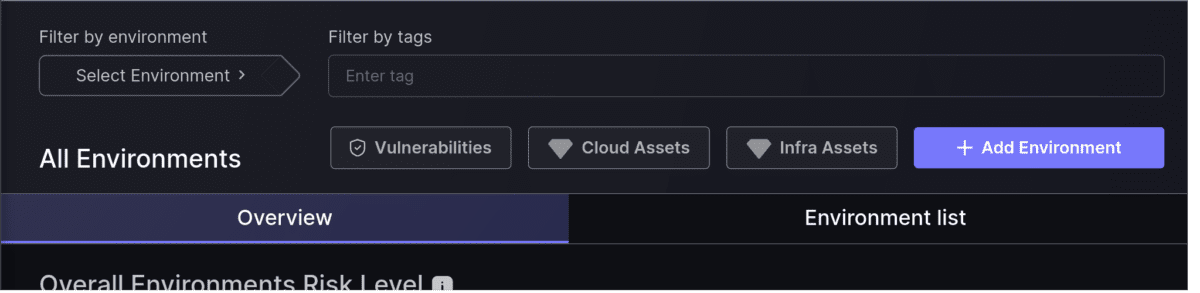
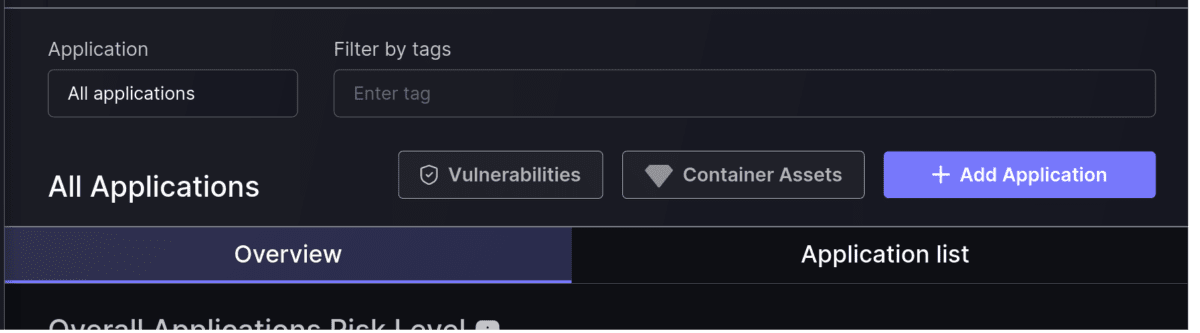
Improved navigation from Environments to their Assets
Now you can easily jump from your Applications or Environments screen to the corresponding Asset screen. This will maintain the selection of applications or environments from Risk Explorer to the Assets screens.
Professional Trial license for OWASP users
From this release, our OWASP License users will be able to access the Professional license Trial when they reach the limit of their license allowance.
If you want to enjoy all these features watch for this new release. You don’t have an AppSec Phoenix account? Just sign-up here and start enjoying all these benefits with our newly announced Community License.
Enjoy!
For any support and question contact support@appsecphoenix.com














