The Common Weakness Enumeration (CWE), a community-developed list of software and hardware weakness types, has released its annual “Top 25 Most Dangerous Software Weaknesses” for 2023 for application security and vulnerability management teams. This list is a critical resource for organizations seeking to prioritize their defensive strategies against potential cybersecurity threats.

The top 25 CWEs represent a broad range of software vulnerabilities and are ranked based on their prevalence and the severity of their potential impact; this can help in identifying the risk-based vulnerability. Here is a summary of the top weaknesses identified for 2023, which reveal a concerning landscape of software vulnerabilities in the digital age.
Notable Climbers and Descenders

Other notable trends in the list include the rise of CWE-862: Missing Authorization, which climbed five spots from the previous year. Conversely, CWE-502: Deserialization of Untrusted Data fell three spots, reflecting changes in the prevalence and impact of these vulnerabilities.
The Top Five
- CWE-787: Out-of-bounds Write: Retaining its top spot from the previous year, this vulnerability refers to software writing data past the end of the intended buffer. It remains a critical weakness due to the potential for an attacker to execute arbitrary code, cause a system crash, or corrupt useful data.
- CWE-79: Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’): Also maintaining its position from last year, Cross-Site Scripting (XSS) vulnerabilities are a significant concern due to the potential for attackers to inject malicious scripts into web pages viewed by other users.
- CWE-89: Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’): SQL Injection vulnerabilities provide a means for attackers to manipulate the logic of SQL queries executed by an application. They can lead to unauthorized data access, corruption, or even loss.
- CWE-416: Use After Free: Climbing up three positions this year, this vulnerability refers to a situation where software continues to use a pointer after it has been freed, leading to a range of security consequences, including the execution of arbitrary code and unexpected software behaviours.
- CWE-78: Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’): This weakness, which has moved up one spot, can allow an attacker to execute arbitrary commands on an operating system, potentially leading to a total system compromise.
CWE over time
The trends in CWE vulnerabilities over the years show some interesting patterns. In the early years, from 2010 to 2011, CWE-79 (Improper Neutralization of Input During Web Page Generation) and CWE-89 (Improper Neutralization of Special Elements used in an SQL Command) were dominant, highlighting the prevalence of web-related security issues. These vulnerabilities continued to be significant concerns in subsequent years, although their scores fluctuated.
As we move towards more recent years, other CWEs gained prominence. CWE-20 (Improper Input Validation) became more prevalent in 2020 and 2021, reflecting the importance of proper input handling to prevent security breaches. CWE-416 (Use After Free) and CWE-78 (Improper Neutralization of Special Elements used in an OS Command) also demonstrated consistent scores, indicating persistent weaknesses in memory management and command execution.
Notably, some CWEs experienced fluctuations in their rankings and scores. CWE-125 (Out-of-bounds Read) and CWE-22 (Improper Limitation of a Pathname to a Restricted Directory) saw variations, indicating that these vulnerabilities were being addressed but remained significant concerns.
Overall, the data suggest that while certain CWE vulnerabilities have remained prevalent over the years, there is also a dynamic landscape where new vulnerabilities arise and gain attention. It highlights the need for ongoing efforts to address common vulnerabilities while staying vigilant to emerging threats and adopting robust security practices to mitigate risks effectively.
CWE 25 and visible patterns
Understanding Common Weakness Enumeration (CWE) vulnerabilities trends is crucial for organizations and security professionals to address and mitigate potential risks. By analyzing historical data from 2010 to 2023, we can identify patterns and emerging trends in the CWE landscape. This blog post aims to shed light on the key vulnerabilities, their fluctuating scores, and the vulnerabilities that have gained prominence in recent years.
Identifying Dominant CWEs: Among the CWEs that have consistently ranked high over the years are CWE-79 (Improper Neutralization of Input During Web Page Generation), CWE-89 (Improper Neutralization of Special Elements used in an SQL Command), and CWE-78 (Improper Neutralization of Special Elements used in an OS Command). These vulnerabilities highlight the continued prevalence of web-related security issues and emphasize the critical need for proper input validation and neutralization techniques.
Fluctuations and Variations: While some vulnerabilities have maintained their positions, others have experienced fluctuations in their scores and rankings. CWE-125 (Out-of-bounds Read) and CWE-22 (Improper Limitation of a Pathname to a Restricted Directory) have witnessed variations, indicating ongoing efforts to address these vulnerabilities. However, despite progress, they remain significant concerns, necessitating sustained attention and mitigation strategies.
Emerging Vulnerabilities: The analysis also reveals emerging vulnerabilities that have gained prominence in recent years. CWE-416 (Use After Free) and CWE-20 (Improper Input Validation) have shown consistent scores, highlighting the persistent weaknesses in memory management and input handling. Additionally, CWE-862 (Missing Authorization) saw a significant increase in score, signaling the importance of proper authorization mechanisms.
Noteworthy Shifts: Several CWEs have witnessed shifts in their rankings, indicating changing priorities in the security landscape. CWE-434 (Unrestricted Upload of File with Dangerous Type) and CWE-306 (Missing Authentication for Critical Function) have moved up in the rankings, underlining the growing awareness of the associated risks. Moreover, CWE-798 (Use of Hard-coded Credentials) and CWE-918 (Server-Side Request Forgery) have gained attention, reflecting the increased focus on credential management and server-side security.
Differences between OWASP top 10 and CWE top 25
The Open Web Application Security Project (OWASP) Top 10 and the Common Weakness Enumeration (CWE) Top 25 are highly respected cybersecurity resources, providing insights into the most critical security vulnerabilities. However, they have distinct focuses and methodologies. The OWASP Top 10 primarily focuses on web application security and identifies the most critical security risks to web applications based on data from numerous organizations. Its main goal is to raise awareness about application security by identifying some of the organisations’ most critical risks. On the other hand, the CWE Top 25 is a broader list that includes the most dangerous software weaknesses across various applications and systems, not limited to the web. It is compiled by scoring each CWE based on its prevalence and severity in real-world applications and the potential for damage if the weakness is exploited. Therefore, while there can be overlapped in the specific vulnerabilities identified by OWASP and CWE, they serve slightly different purposes and can be seen as complementary resources for organizations aiming to improve their cybersecurity posture.
Conclusion
While the CWE top 25 list underscores the importance of addressing these specific vulnerabilities, it also serves as a reminder of the evolving nature of the cybersecurity landscape. Organizations must adopt a proactive stance towards their cybersecurity posture, continuously updating and refining their strategies to account for new threats and vulnerabilities.
Understanding and mitigating the risks associated with the most prevalent software weaknesses is crucial. By doing so, organizations can significantly reduce the likelihood of falling victim to a cybersecurity incident, thereby ensuring their systems’ and data’s security and integrity.
Conclusion: Analyzing the CWE vulnerability data from 2010 to 2023 reveals persistent challenges and emerging trends. While some vulnerabilities remain prevalent, a dynamic landscape is characterized by evolving risks. Security professionals must stay updated on emerging vulnerabilities, adopt robust security practices, and prioritize mitigating common weaknesses. By addressing these vulnerabilities and adapting to changing threat landscapes, organizations can bolster their security posture and minimize the risks associated with CWE vulnerabilities.
Further analysis might include epss data even though this data has proven challenging to associate to CWE.
How can Phoenix Security Help
Phoenix traces CVE and CWE dynamically, offering you an overview of the top CWE in your organization.
Phoenix also trace the top CVE and CWE that teams introduce
Phoenix security cutting-edge contextual risk-based algorithms enable organisations to prioritise application security vulnerabilities based on context and probability of exploitation and present a unified impact analysis.
The cutting-edge vulnerability selection engine enables organisations to set risk-based targets that translate into specific actions for engineers.
Get in control of your Application Security posture and Vulnerability management
Moreover, Phoenix Security’s correlation capabilities can help organizations link the activities in the code with the context in the shift-right part, ensuring that issues are identified and addressed proactively. Using Phoenix Security’s scorecard, organizations can create a common language between the security, development, and business teams, ensuring everyone is aligned and focused on achieving the same goals.
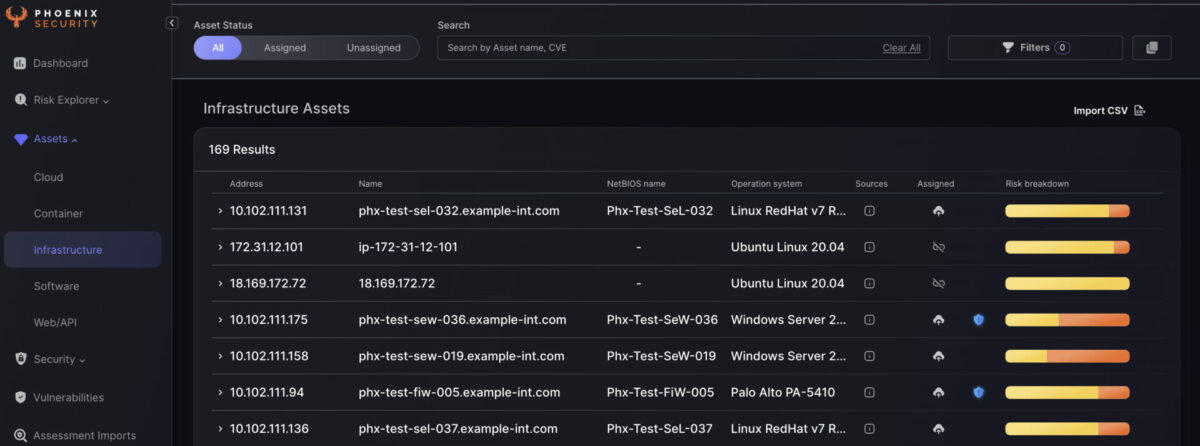
Finally, Phoenix Security’s ability to create risk-based profiles can help organizations translate their security goals into dynamic and smart targets for engineers. By using risk-based profiles, engineers can prioritize their work and focus on the most critical issues, ensuring they effectively use their time and resources.
Overall, by leveraging Phoenix Security’s powerful capabilities, organizations can implement a smart, risk-based approach to software development that ensures the success of their initiatives while minimizing risk and improving overall efficiency. With Phoenix Security as their partner, organizations can feel confident they are taking a proactive approach to software development aligned with their business objectives and goals.



















