
Overview
Phoenix Security expands ASPM vulnerability management by integrating Semgrep, combining developer-first static analysis with contextual code-to-cloud security insight. This latest extension empowers DevSecOps teams with fast, rule-based scanning that feeds directly into contextual vulnerability management workflows. In turn, static analysis results are now tightly integrated with real-time code-to-cloud posture intelligence, reducing noise, sharpening prioritization, and eliminating friction between development and security.
This release enhances application security posture management (ASPM) by embedding precise, code-aware detection into every stage of the software development lifecycle. Security and engineering teams gain one unified system to detect, contextualize, and triage vulnerabilities — from source to cloud runtime.
Release Date: 3 July 2025
Why Semgrep Now Lives Inside Phoenix Security ASPM
Semgrep delivers speed, flexibility, and developer alignment. In parallel, its pattern-based engine provides high-performance SAST and SCA scanning without slowing down CI pipelines. This integration strengthens DevSecOps coverage in line with the OWASP DevSecOps Maturity Model, enabling consistent security enforcement across development workflows. Findings now inherit Phoenix Security’s risk engine — enriched by runtime metadata, asset criticality, and exposure context.
No duplicated alerts. No blind static signals. Each code vulnerability is evaluated in real time based on whether it runs in production, impacts critical infrastructure, or matches known misconfiguration patterns.
Key Benefits for DevSecOps and Application Security
Unified Static and Dynamic Intelligence
Scan source code across languages using Semgrep’s ruleset. To ensure consistency across environments, Phoenix ingests the output, cross-references it with cloud workloads, and filters it through contextual deduplication across AWS, Azure, and GCP.
Code-to-Cloud Visibility
Track every vulnerability from codebase to container to cloud. Regardless of deployment stage, whether a weak encryption function is committed to a private repo or actively deployed inside a production pod, Phoenix surfaces it with complete ownership mapping and severity scoring.
One Backlog for Development and Security
All findings, including Semgrep-based issues, feed into a single triage queue. Developers receive pre-scored, deduplicated tickets based on their repos, branches, and deployment paths — not a flood of scanner results.
Automation-Driven Exception Management
Custom rules, exception handling, and SLA management now apply across both static analysis and runtime telemetry. Teams can approve low-risk issues or escalate critical flaws that touch high-value infrastructure.

Key Features Now Available
1. SAST & SCA Engine Integration
Semgrep’s deep static analysis detects code-level flaws, insecure APIs, vulnerable dependencies, and policy violations. Phoenix contextualizes these findings across cloud deployments and ownership boundaries.
2. Contextual Deduplication Across Environments
Semgrep alerts are automatically deduplicated against infrastructure scan results, container scans, and other integrated signals. Teams no longer chase redundant tickets or manage scattered vulnerability views.
3. Real-Time Risk Prioritization
Issues are scored dynamically based on runtime exposure, cloud access, and application criticality. An unused piece of legacy code triggers no alert. A vulnerable library in an active production pipeline triggers immediate escalation.
4. Seamless DevSecOps Integration
Semgrep findings enter the Phoenix Security workflow as native objects. GitHub, GitLab, Bitbucket, and CI/CD systems all benefit from clean, deduplicated alerts backed by policy-aware automation.
Built for Application Security and Cloud Misconfiguration Remediation
Phoenix Security continues to lead ASPM by connecting static code analysis, secrets detection, dependency risk, and infrastructure misconfiguration into one security graph. To extend full-stack coverage, this release adds lightweight, developer-first static scanning into the same framework used for runtime risk monitoring and cloud misconfiguration remediation.
Phoenix allows users to track the status of targets through status management features e.g. In Progress, Disabled, etc.
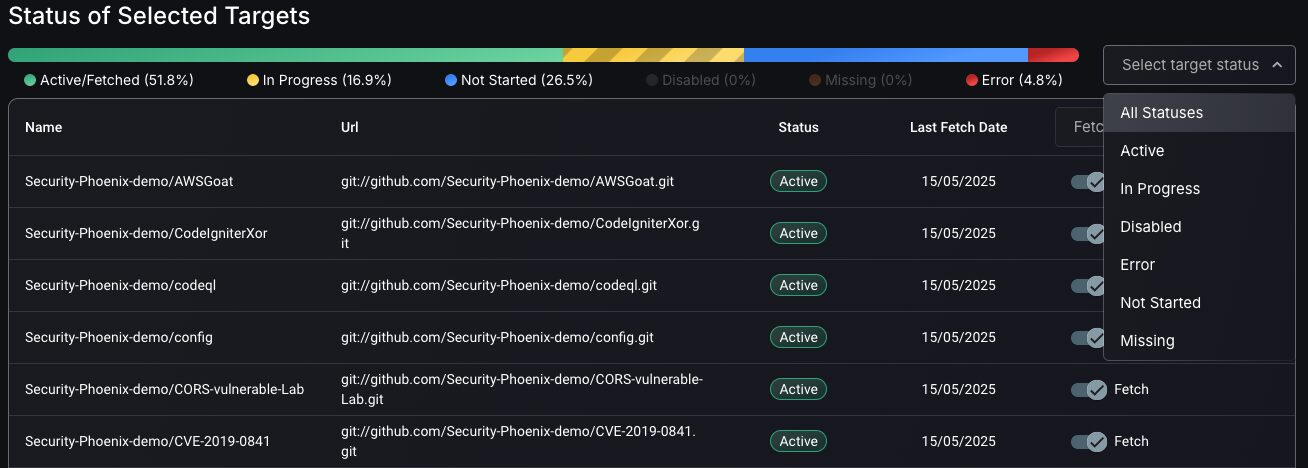
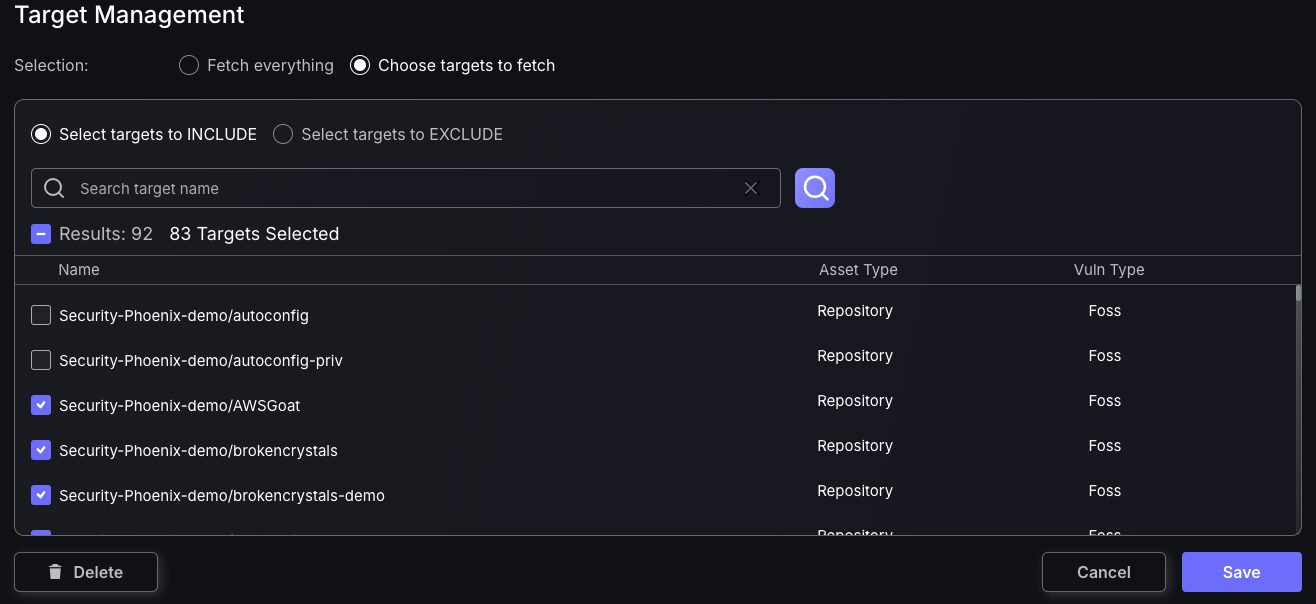
Target management feature enables users to customize assets being fed into Phoenix software by selecting targets to be fetch.
Semgrep joins more than 295 integrated technologies, enabling teams to map their application stack, score risk accurately, and resolve issues faster — all from a single source of truth.
Get Started
Static analysis with Semgrep is available on current version Phoenix Security. Teams can begin ingesting findings immediately through API connection or native CI pipeline hooks.
Learn more in the Phoenix Security Knowledge Base or reach out to your solutions engineer for deployment support.
Get on top of your code and container vulnerabilities with Phoenix Security Actionable ASPM powered by AI-based Reachability Analysis

Organizations often face an overwhelming volume of security alerts, including false positives and duplicate vulnerabilities, which can distract from real threats. Traditional tools may overwhelm engineers with lengthy, misaligned lists that fail to reflect business objectives or the risk tolerance of product owners.
Phoenix Security offers a transformative solution through its Actionable Application Security Posture Management (ASPM), powered by AI-based Contextual Quantitative analysis. This innovative approach correlates runtime data with code analysis to deliver a single, prioritized list of vulnerabilities. This list is tailored to the specific needs of engineering teams and aligns with executive goals, reducing noise and focusing efforts on the most critical issues.
Why do people talk about Phoenix?

• Automated Triage: Phoenix streamlines the triage process using a customizable 4D risk formula, ensuring critical vulnerabilities are addressed promptly by the right teams.
• Contextual Deduplication with reachability analysis: Utilizing canary token-based traceability for network reachability and static and dynamic runtime reachability, Phoenix accurately deduplicates and tracks vulnerabilities within application code and deployment environments, allowing teams to concentrate on genuine threats.
• Actionable Threat Intelligence: Phoenix provides real-time insights into vulnerabilities’ exploitability, combining runtime threat intelligence with application security data for precise risk mitigation.

By leveraging Phoenix Security, you not only unravel the potential threats but also take a significant stride in vulnerability management, ensuring your application security remains up to date and focuses on the key vulnerabilities.















