Abstract
We will discuss with Josh Grossman techniques to start an application security and improve the precision of vulnerability scanning and discuss the vulnerability maturity model and framework https://phoenix.security/vulnerability-management-framework/

Audience recommendation:
- Application Security and Product Security team leaders and members
- Security Engineers with a software focus
- Developers with interest in security
- CISOs interested in Secure SDLC and how to start a programme
Webinar Topics
- Josh’s background and experience and what he has been working on recently
- Trends that Josh sees in the application security industry
- Key challenges which organizations face with application vulnerability scanning tools
- Vulnerability management framework – from detection to measurement to actions
- A four-step action plan to better address challenges with these tools:
- Plan for where to start
- Get buy-in from the business and the development organization.
- Do and Measure – metrics that matter
- Improve – where do we go next
Metrics and measurements are also available and widely discussed in this whitepaper:
Data-driven approach to vulnerability management
We will refer to some of the framework models in the following article: https://phoenix.security/vulnerability-management-framework/
Summary of the webinar (application security with Josh Grossman):
- What is OWASP: OWASP is an open worldwide application security project. It’s a nonprofit organization with chapters around the world. Anyone can get involved and find a way of supporting the organization. One of our commitments with Phoenix is giving back to the community.
- To start a project, what tool do you need to secure your pipeline: either open source or non-open source. The key is how to fine-tune those tooling to get the desired result. Implementing these tools is sort of a project and a process.
- How to use technology and automation: Technology will not save us all, but will help us accelerate processes and procedures. Software security needs to be a function of software development. Engineering leadership needs to accept responsibility of maintaining security within the product.
- Vulnerability management framework: we explore the evolution of an organization leveraging the vulnerability management framework.
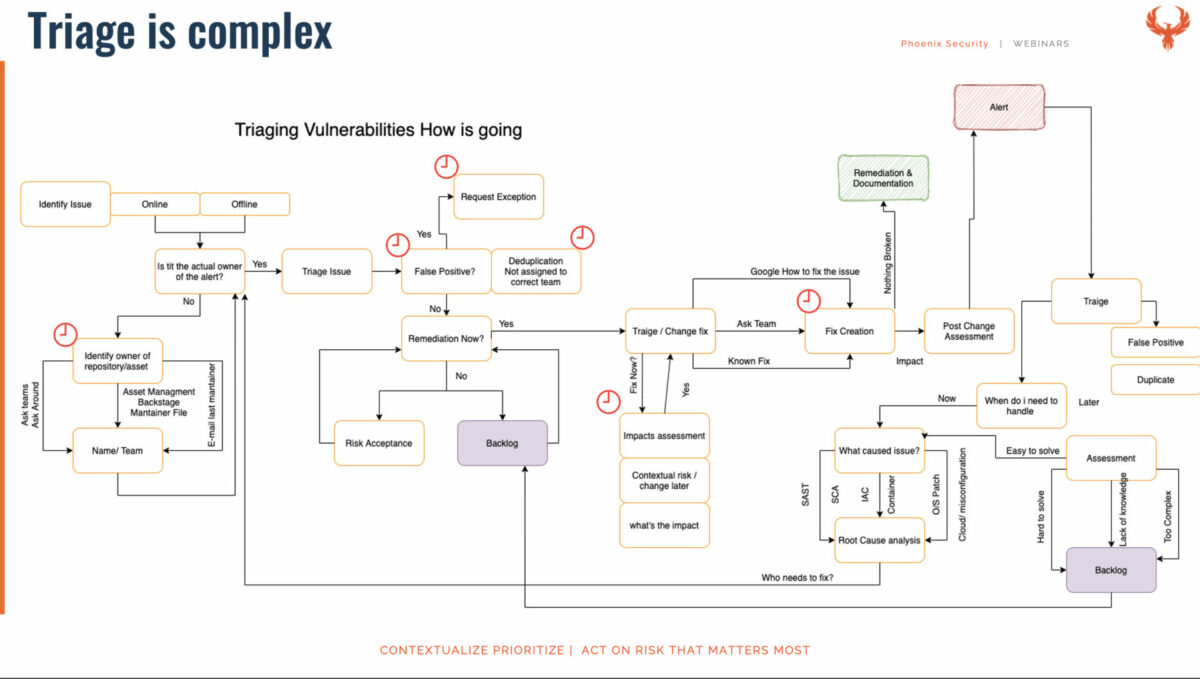
- Vulnerabilities: When we talk about critical vulnerabilities, those are generic ones with no context. Tools that you’re using can provide some of that context. But if you haven’t had that process of saying well, what are we going to do with the output then you’re not going to be ready to carry out that sort of triage.
- – I wanted to maybe take this as a reference point on the complexity of what it is to actually deploy an SDLC in a pipeline. The goal of SSDLC isn’t to do every single item on this diagram. It’s to be in a situation where we can confidently roll out this item and then this item over a period of time.
Transcript
01:00 – Josh Grossman intro & Background
05:00 – How do I start in application security
10:00 – Negative feeling when implementing application security scanners without vulnerability management process and technologies
15:00 – Where do I start with tooling in an SDLC
20:00 – Data about vulnerabilities is not Insights; what do we need to care?
27:00 – Vulnerability scanners in SDLC and triage – Image below
36:00 – Breaking the build – where and when
38:00 – Traige extreme case
41:00 – Tooling consequences
43:00 – vulnerability management framework.
52:00 – Joshua Training and improving toolings
55:00 – Closing Remarks and links
References and additional material
Secure SDLC and what tools to integrate:
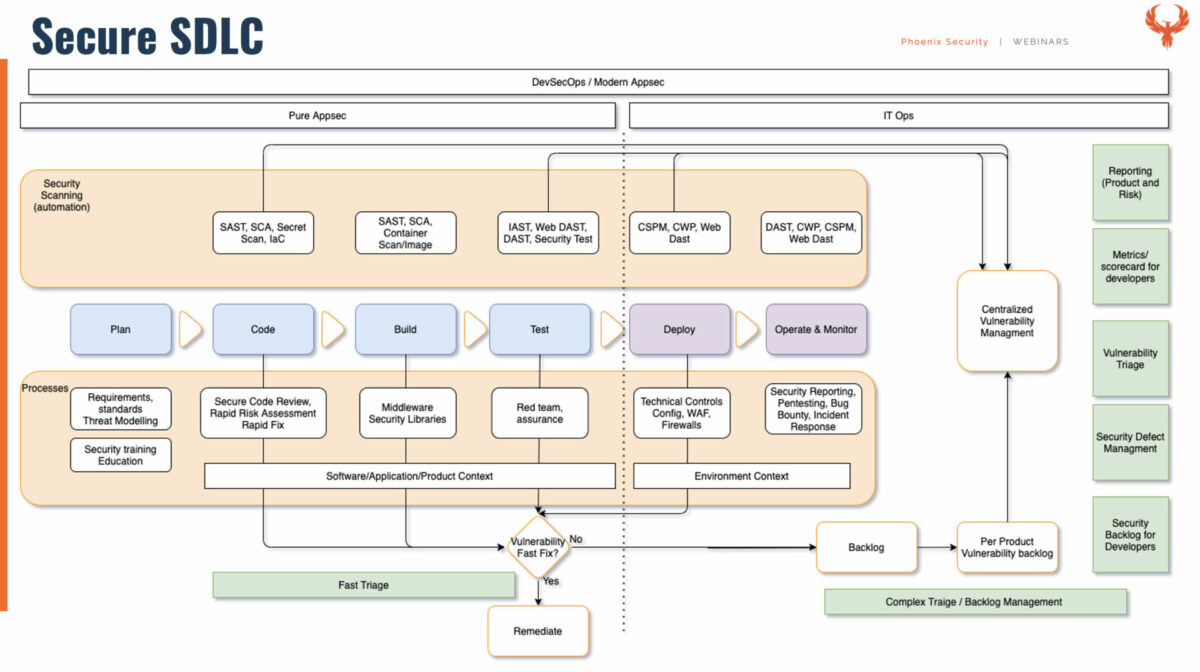
Triage in SDLC and why is it complex:
Josh Grossman Trainings
Josh Grossman is delivering on this topic at Black Hat USA:
Tune your Toolbox – Building a high-value AppSec scanning programme.
Background about the speaker – Josh Grossman, and his application security career
Josh Grossman has worked as a consultant in IT and Application Security and Risk for 15 years now, as well as a Software Developer. This has given him an in-depth understanding of how to manage the balance between business needs, developer needs and security needs, which goes into a successful software security programme.
Josh is currently CTO for Bounce Security, where he helps clients improve and get better value from their application security processes and provides specialist application security advice. His consultancy work has led him to work, speak and deliver training both locally and worldwide including privately for ISACA and Manicode and publicly for OWASP’s Global AppSec conferences.
In his spare time, he co-leads the OWASP Application Security Verification Standard project and is on the OWASP Israel chapter board.
Links:
- https://joshcgrossman.com
- https://BounceSecurity.com
- Social media:
Francesco Cipollone (host) and application security background
Francesco is a seasoned entrepreneur, CEO of the Contextual-based vulnerability management platform from code to cloud Phoenix Security, author of several books, host of multi-award Cyber Security & Cloud Podcast, speaker and known in the cybersecurity industry and recognized for his visionary views. He currently serves as Chapter Chair UK&I of the Cloud Security Alliance. Previously, Francesco headed HSBC’s application and cloud security and was Senior Security Consultant at AWS. Francesco has been keynoting at global conferences and has authored and co-authored several books. Outside of work, you can find me running marathons, snowboarding on the Italian slopes, and enjoying single malt whiskeys in one of my favourite London clubs.
















