New research by the CWE group of Mitre on CISA Kev and common vulnerabilities Application security and vulnerability management programs can leverage that information to enhance the detection of patterns; ASPM technology is especially helpful in this space as they cross-correlate Application and deployment environments. This correlation is critical as CISA KEV vulnerabilities mostly affect infrastructure and hardware type of assets (see article application security and KEV)
CWE: A Foundation for Application Security:
Common Weakness Enumeration is a standardised list of common software and hardware weaknesses. It’s an invaluable tool in Application Security, offering a universal language for understanding and discussing software vulnerabilities. They categorise each vulnerability, aiding developers and security professionals identify potential application flaws. This proactive approach is essential for a robust Application Security Posture Management strategy, ensuring that applications are fortified against known vulnerabilities from the development phase. Understanding weaknesses and their categories can help teams leverage better ASPM technologies and craft tailored training for developers and engineers.
CISA KEV: Prioritizing Threats in Cybersecurity:

THE CISA KEV catalogue is a resource highlighting vulnerabilities that are actively exploited and can help detect patterns in vulnerability management and application. It is a real-time guide for cybersecurity teams to prioritise threats that pose an immediate risk. By focusing on these vulnerabilities, organisations can optimise their resources and efforts in addressing the most critical and impactful threats first, enhancing their overall Vulnerability Management process.
The analysis has highlighted Memory Safety, Improper Input Validation and injection as the top 3 typical vulnerability types.
While from a deeper analysis in 2023 alone, the top trending categories are:
- CWE-79 (Cross-site Scripting): A high score and rank indicate its prevalence and impact.
- CWE-89 (SQL Injection): Another high scorer, highlighting its continued relevance.
- CWE-20 (Improper Input Validation): Common and critical, affecting various applications.
Methodology of Attack and Systemic Issue Identification:
Both those two datasets follow methodologies that help identify systemic issues in cybersecurity; this is one of the top techniques used by ASPM technologies to cross-correlate different types of technologies
- Categorisation and Severity Assessment: CWE categorises vulnerabilities, while CISA KEV highlights their exploitability. This combined information provides a comprehensive view of potential attack vectors, enabling organisations to assess the severity and impact of each vulnerability.
- Trend Analysis and Predictive Insights: Analyzing the trends of both datasets can offer predictive insights into potential future threats. This foresight is crucial for proactive Application Security and Vulnerability Management.
- Resource Optimization: By understanding the most prevalent and severe vulnerabilities, organisations can allocate their resources more effectively, focusing on the areas needing the most attention to mitigate risks.
The CWE in CISA KEV data analysis
The dataset analysed seems to be slightly antiquated and dates around May. Moreover, several (164) vulnerabilities were unclassified over the two years analysed. ASPM Technologies heavily leverages Weakness to understand patterns of vulnerabilities. Refer to the CWE CISA KEV data explorer for more and detailed insights
Overlaying exploitability analysis of the exploits verified in Nuclei and Metasploit modules shows a significant presence of verified exploitable vulnerabilities in Kev as one of the requirements to be in CISA KEV.
Analysing 2022 and 2023, where CISA KEV has the richest dataset and is more mature, we can see a pattern of vulnerability.
Interestingly, not all the CWE top 25 appear in CISA KEV, highlighting the bias of KEV towards a certain set of vulnerability types (infrastructure, IoT, Hardware)

- Prominent CWE Types, based on the Top25 Rank and Score, are:
- CWE-79 (Cross-site Scripting): A high score and rank indicate its prevalence and impact.
- CWE-89 (SQL Injection): Another high scorer, highlighting its continued relevance.
- CWE-20 (Improper Input Validation): Common and critical, affecting various applications.
- CWE-119 and CWE-787: Related to memory safety, indicating ongoing issues in software memory management.
- Severity and Exploitability:
- Highest Severity: Several CWEs, like CWE-78, CWE-416, and CWE-94, have vulnerabilities rated at the highest severity (10), indicating potential for significant impact.
- Exploit Verified and PoC/ExploitDB: CWEs like CWE-20, CWE-416, and CWE-502 have verified exploits or PoC available, suggesting they are actively or at high risk of exploitation.
- Vulnerability Spread:
- A number of Vulnerabilities and Products: CWE-78, CWE-416, and CWE-94 show more vulnerabilities and affected products, indicating widespread issues.
- Number of Vendors: A high number of vendors affected by certain CWEs like CWE-20 and CWE-787 suggests industry-wide challenges.
- EPSS (Exploit Prediction Scoring System):
- High EPSS scores in CWEs like CWE-79, CWE-502, and CWE-284 imply a higher likelihood of these vulnerabilities being exploited in the wild.
- Temporal Aspects:
- Average Time to KEV: This metric varies significantly across CWEs, with CWE-78 and CWE-200 having a notably longer average time, suggesting slower detection or reporting.
- Popularity Data and Bug Bounty: Popularity data and the presence of bug bounties, as seen in CWEs like CWE-269 and CWE-502, can indicate community and industry focus on these vulnerabilities
When Taken into consideration, classified Vulnerabilities dwarf the other datasets (see rightmost bars)
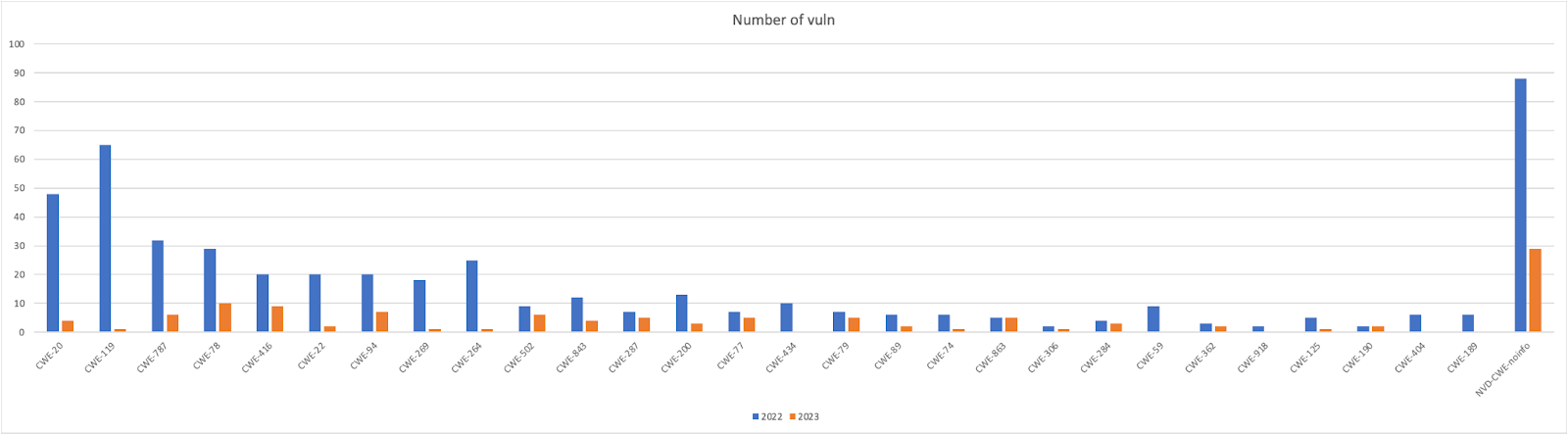
Trending Across 2022 and 2023 vs full dataset
The top vulnerabilities across 2022 and 2023 remain confirmed by the overall analysis (going back to 2020), with CWE 20, 119, and 787 having the biggest presence.
There is a general decrease in the number of reported vulnerabilities from 2022 to 2023 for many CWE types, such as CWE-20 (Improper Input Validation) and CWE-119 (Improper Restriction of Operations within the Bounds of a Memory Buffer). This could indicate improved security practices or a shift in the types of discovered vulnerabilities.

Complexity of CWE – Nesting
So why the two pies are different? Because the CWE have a nested structure an example of the mapping will lead to a better understanding of the methodologies of attacks
| CWE | Description | Category |
| NVD-CWE-noinfo | Unknown CWE | Not Applicable |
| CWE-20 | Improper Input Validation | Software and Data Integrity Failures |
| CWE-119 | Improper Restriction of Operations within the Bounds of a Memory Buffer | Memory Buffer Errors |
| CWE-787 | Out-of-bounds Write | Memory Buffer Errors |
| CWE-78 | Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) | Injection |
| CWE-416 | Use After Free | Resource Management Errors |
| CWE-22 | Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) | Pathname Traversal and Equivalence Errors |
| CWE-94 | Improper Control of Generation of Code (‘Code Injection’) | Injection |

This overview summarizes and highlights different trends between years
- Software and Data Integrity Failures: With a notable decrease from 48 in 2022 to 4 in 2023, this category suggests a significant improvement in software and data integrity practices, potentially indicating more robust coding practices or effective vulnerability remediation.
- Memory Buffer Errors: Remaining a prevalent issue, memory buffer errors show a slight decrease. This type of error remains consistently high, indicating the continuing challenge of managing memory safely in software development.
- Injection: The substantial rise from 62 to 23 suggests an increasing trend in exploitation techniques like SQL, Command, and Cross-Site Scripting (XSS) attacks, which remain the favourite vectors for attackers.
- Resource Management Errors: With a minor increase, these errors, which often lead to leaks or exhaustion of system resources, indicate a persistent challenge in handling system resources correctly.
- Pathname Traversal and Equivalence Errors: The minimal change from 29 to 2 suggests that while these issues are less frequent, they remain a consistent threat, often leading to unauthorized file access.
- Permissions, Privileges, and Access Controls: With an almost unchanged count, issues in this category remain a constant threat, emphasizing the need for strict access control measures.
- Serialization Issues: The increase from 9 to 6 could reflect a rise in the complexity of applications and the utilization of serialization/deserialization processes, leading to more vulnerabilities being identified.
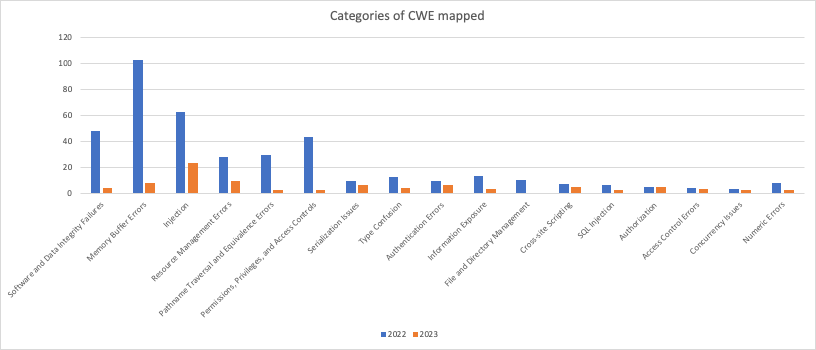
- Type Confusion: A slight increase in type confusion errors points to ongoing issues with type safety in programming languages, which can lead to severe security implications.
- Authentication Errors: Doubling in count from 2022, these errors suggest that improper authentication mechanisms continue to be a significant vector for security breaches.
- Information Exposure: The small increase indicates a continued risk of sensitive information being exposed due to various vulnerabilities.
- File and Directory Management: With no change year over year, this suggests a steady state of challenges associated with file and directory management vulnerabilities.
- Cross-site Scripting: The rise in XSS issues points to the persistent relevance of client-side security and the need for web applications to better sanitize user input.
- SQL Injection: A slight increase from 2022 to 2023 in SQL injection attacks underlines their continued use by attackers to exploit databases.
- Authorization: Doubling in frequency, authorization issues are increasingly exploited, potentially allowing attackers unauthorized access to system functions.
- Access Control Errors: A slight increase in access control errors highlights ongoing challenges in ensuring proper restrictions on system access.
- Concurrency Issues: A small increase in concurrency issues underscores the complexities of multi-threaded and concurrent processing in secure applications.
- Numeric Errors: A slight increase in numeric errors, such as integer overflows, suggests that fundamental programming pitfalls continue to be a source of vulnerabilities.
- Not Applicable: The significant number of unclassified or ‘Not Applicable’ entries, especially increasing in 2023, may indicate a set of vulnerabilities that are yet to be categorized or are outside the scope of existing classifications, reflecting either emerging threats or a lag in vulnerability identification and categorization.
Optimising ASPM with CWE and CISA KEV:
Integrating CWE and CISA KEV into Application Security Posture Management enables organisations to build a more resilient cybersecurity framework. This integration helps in:
- Early Detection and Prevention: Identifying vulnerabilities early in the software development lifecycle through CWE can prevent the exploitation of these weaknesses.
- Prioritisation of Patching and Updates: Utilizing CISA KEV, organisations can prioritise patching the most critical vulnerabilities first, an essential aspect of effective Vulnerability Management. Leveraging the detection of CWE enables the identification of patterns for vulnerabilities.
- Comprehensive Security Strategy: Combining the insights from both CWE and CISA KEV allows for a more comprehensive and informed security strategy, addressing both potential and active threats.
Conclusion:
The synergy between CWE and CISA KEV is indispensable for a robust Application Security Posture Management strategy. By leveraging these resources, organizations can enhance their understanding of vulnerabilities, prioritize their response to threats, and optimize their overall cybersecurity framework. In the dynamic landscape of Application Security and Vulnerability Management, staying informed and proactive is key to safeguarding against evolving cyber threats.
How Can Phoenix Security Help with CWE and prioritization
Phoenix Security helps organisations identify and trace which systems have vulnerabilities, understanding the relation between code and the cloud. One of the significant challenges in securing applications is knowing where and how frameworks like Struts are used. ASPM tools like Phoenix can cross-correlate CISA KEV and provide early notification when an asset or a vulnerability is subject to ransomware or the break of a federal government contract.
The CISA KEV and CWE analysis provided by Phoenix can help organisations better train the developers and engineers and identify issues and patterns.
This information is crucial for targeted security measures and efficient patch management. Phoenix Security’s robust Application Security Posture Management (ASPM) system is adept at managing and preempting the exploitation of vulnerabilities through its automated identification system. This system prioritises critical vulnerabilities, ensuring teams can address the most pressing threats first, optimising resource allocation and remediation efforts.

The Role of Application Security Posture Management (ASPM):
ASPM is vital in managing and securing applications like those built with Apache Struts. It involves continuous assessment, monitoring, and improvement of the security posture of applications. ASPM tools can:
- Identify and Track Assets and CWE: Locate where Struts is implemented within the application infrastructure.
- Vulnerability Management: Detect known vulnerabilities in Struts and prioritize them for remediation.
- Configuration Monitoring: Ensure Struts configurations adhere to best security practices.
- Compliance: Check if the usage of Struts aligns with relevant cybersecurity regulations and standards.
By leveraging Phoenix Security, you not only unravel the potential threats but also take a significant stride in vulnerability management, ensuring your application security remains up to date and focuses on the key vulnerabilities.