Recognized in Latio Report, Cloud Security Innovator 2025, and Leader in ASPM & CTEM
Application security has entered a new phase defined by Continuous Threat Exposure Management 2026. Scanners alone no longer differentiate vendors. Dashboards alone no longer impress CISOs. Enterprises are not buying tools — they are buying outcomes: reduced attack surface, faster remediation, measurable risk reduction, and developer-aligned execution.
Scanners alone no longer differentiate vendors. Dashboards alone no longer impress CISOs. Enterprises are not buying tools — they are buying outcomes: reduced attack surface, faster remediation, measurable risk reduction, and developer-aligned execution.
Phoenix Security has been named Application Security Management Leader for 2026 in the Latio Report and recognized as Cloud Security Innovator 2025 and Leader in ASPM and CTEM in the Cloud Security Report.
These recognitions validate what our customers already know: application security must move beyond detection and into contextual remediation.
Contents
ToggleWhat Enterprises Are Really Searching For
Large organizations evaluating application security platforms are not asking:
- “How many scanners do you integrate with?”
- “Do you support SAST and SCA?”
- “Can you show me another dashboard?”
They are asking:
- Who owns this vulnerability?
- Where is it deployed?
- Is it reachable?
- Is it exploitable?
- What is the fastest, lowest-impact remediation path?
- How do I prove to the board that risk is decreasing?
The Latio report captured this market transition clearly: the difference between platforms is no longer pure detection capability. It is usability, integration depth, backlog reduction, and time-to-fix.
Phoenix Security has built its platform around exactly that shift.
Overview of the 2026 Application Security Market Report
The 2026 Latio Application Security Market Report captures a discipline in transition. Application security is no longer defined by scanner breadth. It is defined by backlog reduction, developer experience, runtime validation, and measurable remediation velocity.
The report makes several structural observations that directly shape enterprise buying decisions:
- Platform consolidation has shifted focus away from detection depth and toward workflow, integration, and usability
- AI-native detection is changing static analysis, particularly around business logic flaws
- Evaluations should prioritize time-to-fix rather than total findings
- ASPM has evolved into broader CTEM and universal vulnerability management models
- Runtime context is emerging as the truth layer for exploitability and prioritization
The market is moving from vulnerability aggregation to exposure reduction.
That shift aligns tightly with the capabilities outlined earlier in What Makes Phoenix Security Different, particularly around attribution, reachability, AI prioritization, and remediation orchestration.
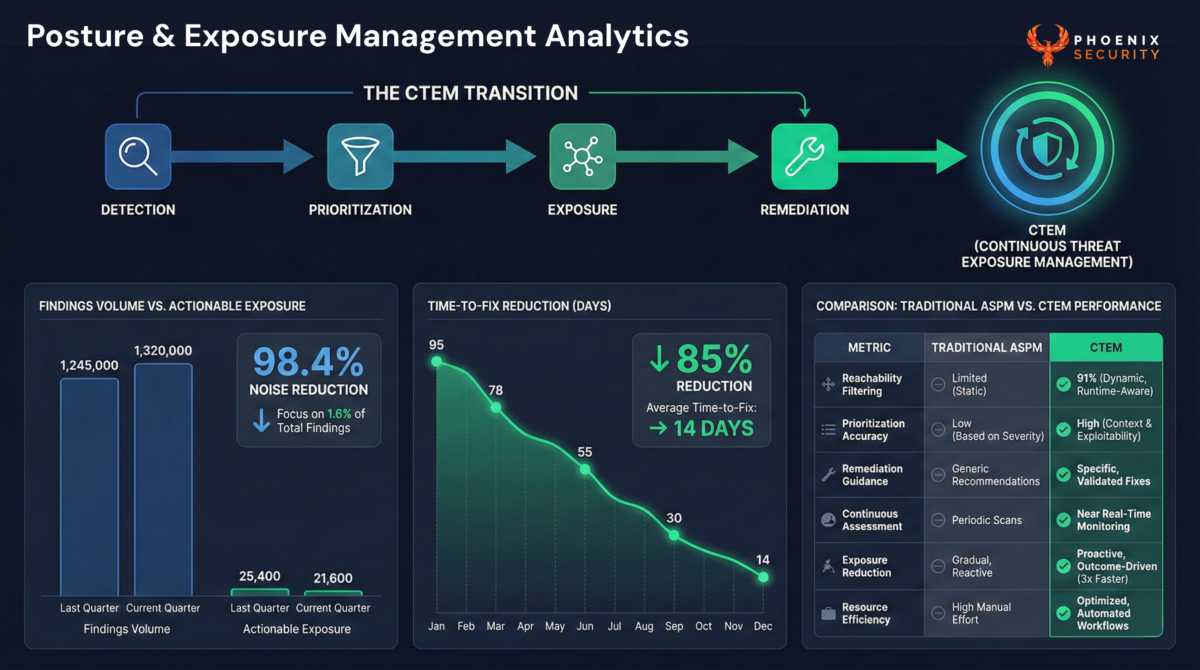
Remediation Is the Real Battleground
The report highlights a painful reality: detection has improved. Backlogs have not.
Enterprises are drowning in:
- SCA findings
- Container duplicates
- Legacy SAST noise
- Compliance-driven vulnerability counts
The bottleneck is not discovery. It is remediation.
Modern remediation requires more than opening pull requests. It requires:
- Function-level reachability to confirm exploitability
- Breaking-change analysis across library upgrades
- Backporting strategies in high-risk enterprise systems
- Consolidation of container and SCA duplication
Consider a real supply chain example.
The following packages and versions contain a vulnerability:
React
- react-server-dom-parcel 19.1.0 to 19.1.1 and 19.2.0
- react-server-dom-turbopack 19.0.0 and 19.1.0 to 19.1.1 and 19.2.0
- react-server-dom-webpack 19.0.0 and 19.1.0 to 19.1.1 and 19.2.0
Any framework bundling the server implementation is potentially vulnerable, notably Next.js.
Next.js
- 14.3.0 and later with App Router
- All 15.x versions
- All 16.x versions
Additional frameworks affected include:
- React Router RSC preview
- Waku
- Parcel RSC plugin
- Vite RSC plugin
- RedwoodJS
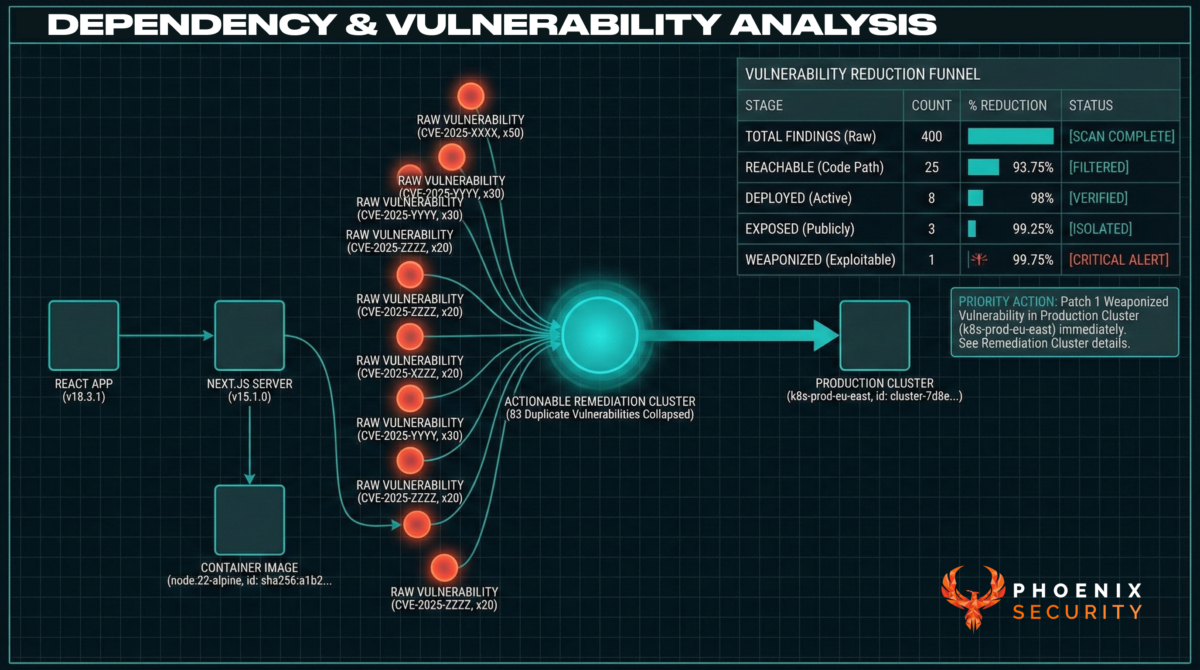
In a typical enterprise, that single vulnerability may appear:
- In source code dependencies
- In container base images
- In multiple services
- Across staging and production clusters
A scanner reports hundreds of findings.
A remediation-driven exposure platform asks:
- Which services actually execute the vulnerable function?
- Which are externally exposed?
- Which are mapped to Tier 1 revenue applications?
- Which container images inherit from the same base layer?
- What is the lowest-impact upgrade path?
That is the difference between vulnerability reporting and vulnerability reduction.
From ASPM to CTEM: The Market Has Evolved
The report highlights a structural transformation:
- Traditional ASPM focused on consolidating scanner output.
- Vulnerability Management focused on severity, patching, and infrastructure vulnerabilities.
- Risk-Based Vulnerability Management tried to reprioritize.
Phoenix was built around the Continuous Threat Exposure Management (CTEM) — a methodology centered on validating exploitability, mapping exposure, and driving remediation.
Phoenix Security did not bolt CTEM onto an existing scanner stack. We engineered the platform around:
- Code-to-cloud correlation
- Reachability analysis
- Container lineage and throttling
- AI-Powered Security research for Threat intelligence enrichment
- AI-powered remediation orchestration
That architectural foundation is why Phoenix is recognized as a leader in both ASPM and CTEM.
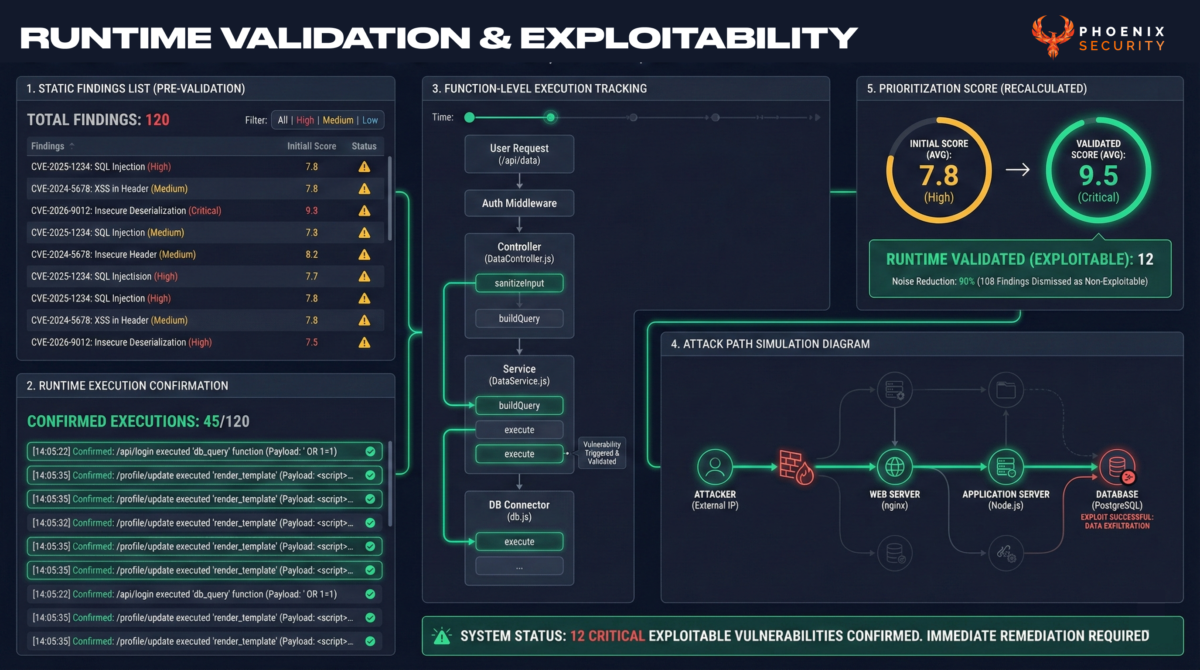
Runtime Is the Source of Truth
The report is explicit: runtime context delivers the strongest prioritization signal.
Static reachability reduces backlog.
Runtime function-level execution validates exploitability.
Runtime technologies now provide:
- Function-level execution tracking
- Attack path simulation
- Application-layer detection and response
- Correlation between static findings and production behavior
When runtime confirms that a vulnerable function is executing in production, prioritization becomes obvious.
When runtime shows that a dependency exists but is never called, triage effort drops immediately.
This runtime correlation is especially critical in containerized environments, where duplication between SCA and container scanners inflates vulnerability counts.
Exposure management programs that ignore runtime context will continue to inflate backlogs rather than shrink them.
Ownership Drives Execution
The report repeatedly emphasizes orchestration challenges in enterprises with thousands of repositories.
Detection without ownership mapping leads to:
- Ticket misrouting
- SLA theater
- Unassigned backlog
- Friction between AppSec and engineering
Ownership must be programmatic.
Modern platforms differentiate on:
- Application-to-team mapping
- CI/CD pipeline coverage visibility
- Deployment mapping
- Code-to-cloud correlation
This is where management-layer capabilities become decisive, especially in distributed environments.
The earlier section on What Makes Phoenix Security Different describes how attribution, reachability, and AI remediation converge. That alignment reflects the broader market direction outlined in the report.
Prioritization Beyond CVSS
Severity alone is no longer defensible.
The report emphasizes:
- AI-driven prioritization
- Static function-level reachability
- Runtime validation
- Cloud context correlation
The most effective false-positive reduction comes from combining runtime function-level reachability with cloud context.
When static findings, runtime telemetry, and cloud exposure signals converge, noise collapses.
That convergence defines modern CTEM.
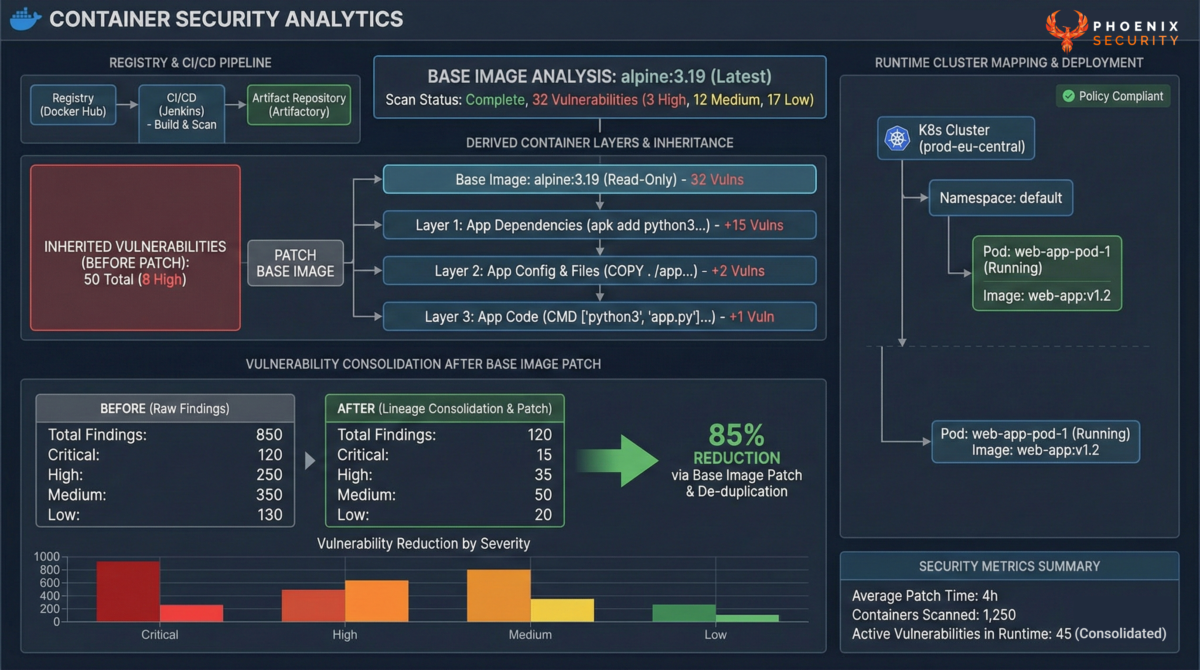
Cloud Runtime and Container Reality
Container scanning introduces duplication and lifecycle complexity.
Scanning a container pulls in:
- OS packages
- Language libraries
- Base image inheritance
- Build layer metadata
- Registry artifacts
- Running workload context
Without lineage awareness, enterprises remediate the same vulnerability repeatedly across derived images.
With lineage mapping, remediation becomes surgical:
- Upgrade the base image once
- Rebuild downstream images
- Eliminate hundreds of inherited findings
Cloud runtime context further enhances prioritization by linking:
- Public endpoints
- API exposure
- Identity permissions
- Network reachability
Exposure management without cloud runtime integration is incomplete.
CTEM Is Not a Dashboard
The report makes it clear that traditional ASPM collapsed because dashboards do not drive remediation.
CTEM requires:
- Continuous discovery
- Exposure validation
- Context-driven prioritization
- Remediation orchestration
- Runtime validation
Platforms that treat management as aggregation fail.
Platforms that treat management as execution win.
The Strategic Alignment
The 2026 Application Security Market Report signals a decisive industry shift:
- From scanning to exposure
- From detection to remediation
- From severity to exploitability
- From code-only to code-to-cloud
- From dashboards to execution
The section above, What Makes Phoenix Security Different, reflects this exact trajectory:
- Enterprise-grade attribution
- Tool-agnostic reachability
- AI prioritization and remediation
- Code-to-cloud correlation
- Runtime-aware exposure reduction
The recognition as Application Security Management Leader 2026 validates that this is no longer a niche view.
It is where the market is going.
And for enterprises managing React supply chain risk, container duplication, AI-generated code, and sprawling runtime exposure, remediation-aware CTEM is no longer optional.
What Makes Phoenix Security Different
1. Enterprise-Grade Attribution at Scale
Enterprise vulnerability programs fail when ownership is unclear.
Phoenix Security solves attribution programmatically:
- Developer first YAML-native CMDB (PYRUS)
- Native Asset inventory and CMDB Integration with connectors to Backstage
- Git metadata correlation
- Cloud and CI/CD tagging
Every vulnerability is mapped to:
- Team
- Service
- Deployment environment
- Business tier
Real-World Proof: Measurable Reduction
Recognition means nothing without results.
ClearBank – Fintech
- 98% reduction in container vulnerabilities
- 96% reduction in critical vulnerabilities
- $15M in developer time saved
- 91–99% weekly critical reduction
“Phoenix helped us move from noise to precision. We now focus on what truly matters — and fix faster than ever before.”
— Neil Reed, Principal AppSec Engineer, ClearBank
2. Tool-Agnostic Reachability and Deduplication
Most enterprises already have scanners.
Replacing them is unrealistic.
Phoenix sits on top of:
- SAST
- SCA – scanning and enriching
- Container scanning – aggregating and enriching
- Cloud security tools – native scanning
- IaC scanning
Then we apply:
- Code-level reachability
- Runtime reachability
- Container lineage analysis
- Contextual deduplication
The result?
Instead of 400 Jackson-Databind CVEs across code and containers, teams see:
- 25 reachable
- 8 deployed in production
- 3 externally exposed
- 1 weaponized
That is exposure management.
That is why enterprises choose Phoenix.
3. AI Agents Built for Remediation, Not Noise
The Latio report emphasizes the shift toward AI-native features — but also warns against AI-wash.
Phoenix Security deploys AI agents only after contextualization.
Three agents power remediation:
The Researcher
- Maps vulnerabilities to threat actors
- Tracks weaponization
- Correlates CTI, EPSS, KEV
- Classifies root causes
The Analyzer
- Simulates attack paths
- Validates reachability
- Scores based on exposure and business impact
- Identifies blast radius
The Remediator
- Clusters vulnerabilities into fixable bundles
- Suggests framework-aware upgrades
- Generates IaC patches
- Routes tickets with full ownership metadata
AI amplifies humans. It does not replace context.
Bazaarvoice – Retail
- Critical vulnerabilities reduced to zero
- 40% reduction in high-risk issues in two weeks
- Container security aligned with engineering workflows
“We didn’t just improve visibility — we eliminated criticals. Phoenix made that operationally possible in days, not months.”
— Nate Sanders, Senior Manager, Security Engineering & Operations
Global Ad-Tech Enterprise
- 78% reduction in container vulnerabilities
- 82% reduction in SCA noise
- Unified remediation across code and cloud
“Phoenix gave us the missing bridge between code and cloud. The visibility is deep, the actions are clear — and the results speak for themselves.”
— Director of Application Security
Why Cloud Security Innovator 2025 Matters
Cloud-native environments break traditional security models.
Containers:
- Multiply vulnerabilities
- Inflate duplicates
- Introduce runtime uncertainty
Phoenix Security’s container throttling and lineage model allows enterprises to:
- Ignore inactive images
- Map container images to repositories
- Trace base image inheritance
- Focus on running workloads
ClearBank alone reduced container noise from hundreds of thousands of findings to a manageable, actionable set.
That is cloud security innovation.
Key Question Raised by the Report
Built for Distributed, Regulated, Global Enterprises
Large enterprises operate across:
- Multi-cloud and hybrid environments
- Thousands of repositories
- Ephemeral containers
- Distributed engineering teams
- Complex regulatory obligations
Phoenix Security was engineered for that reality.
What Global Enterprises Require
1. Consistent Ownership Across Regions
Automated attribution via YAML-native CMDB (PYRUS), ServiceNow, Backstage, and identity provider integrations ensures every asset has a clear owner — across continents.
2. Unified Code-to-Cloud Visibility
Trace vulnerabilities from repository to container to runtime. No silos between AppSec and CloudSec.
3. Regulatory Alignment Without SLA Theater
Support for PCI DSS, NIST, FFIEC, HIPAA, and financial sector controls — driven by risk-based prioritization rather than severity-only patching.
4. Scalable Backlog Reduction
Deduplicate vulnerabilities across SAST, SCA, container, and cloud scanners. Focus only on reachable, exploitable, exposed risks.
5. Board-Ready Exposure Metrics
Translate vulnerability data into measurable exposure reduction and business risk impact.
Phoenix Security enables global organizations to operate securely at scale — without increasing headcount or slowing delivery velocity.
















