Continuous Threat Exposure Management (CTEM) is an evolution of vulnerability management and a five-step program for achieving long-term and sustainable cyber resilience. A CTEM cycle includes the stages of scoping, discovery, prioritizing, validation, and mobilization.
History and evolution of vulnerability management
Vulnerability management is the process of identifying, prioritizing, and mitigating vulnerabilities in computer systems and networks. It involves regularly scanning for vulnerabilities, analyzing their potential impacts, and taking steps to fix or mitigate them. This can include patching software, configuring systems to reduce the attack surface, and implementing other security measures.
The current problem the security team face is having to manage different asset type from code to cloud and equivalent reports.
The vulnerability reports associated with various assets are generally uncontextualized and lead to alert fatigue and exhaustion by the number of vulnerabilities.
Why the evolution from vulnerability management to Continous Threat Exposure Management
One of the major drivers behind this evolution has been the increasing complexity and interconnectedness of modern computer systems and networks. With the proliferation of cloud computing, internet of things (IoT) devices, and other emerging technologies, it has become more difficult to identify and mitigate vulnerabilities in a timely manner. CEM addresses this challenge by continuously scanning for vulnerabilities and taking a proactive approach to mitigating them.
Another factor has been the increasing frequency and sophistication of cyber threats. With the rise of advanced persistent threats (APTs) and other highly targeted attacks, organizations must proactively identify and mitigate vulnerabilities to prevent successful attacks. CEM/CTEM helps organizations do this by continuously monitoring for vulnerabilities and implementing measures to prevent or mitigate them.
What is CEM/CTEM, and how does it differ from vulnerability management?
Vulnerability management identifies, prioritises, and remediates vulnerabilities in an organization’s systems and networks. It involves continuous monitoring and scanning systems to identify vulnerabilities and implement measures to mitigate or eliminate them. The goal of vulnerability management is to reduce the risk of cyber-attacks and other security breaches by ensuring that systems are as secure as possible.
CTEM, or Cyber Threat and Exposure Management, is a related concept that involves identifying, assessing, and managing cyber threats and exposures that could potentially impact an organization. CTEM typically includes various activities, including threat intelligence gathering, risk assessment, and incident response planning. The goal of CTEM is to help organizations anticipate and respond to cyber threats in a timely and effective manner, to minimize the impact of those threats on the organization.
While vulnerability management and CTEM are related concepts, they differ in the specific focus of their activities. Vulnerability management is focused on identifying and mitigating vulnerabilities in systems and networks, while CTEM is focused on identifying and managing cyber threats and exposures.
CEM takes a more proactive approach to vulnerability management. Rather than simply reacting to vulnerabilities as they are discovered, CEM aims to monitor and assess an organization’s exposure to vulnerabilities continuously. This involves continuously scanning for vulnerabilities, analyzing their potential impacts, and implementing measures to prevent or mitigate them. CEM also involves ongoing communication and collaboration between different teams within an organization, such as security, IT, and development, to ensure that vulnerabilities are addressed promptly and effectively.
The key takeaway for Vulnerability Management evolution into CEM/CTEM
- Improved security: By continuously monitoring and assessing an organization’s exposure to vulnerabilities, Continuous Threat Exposure Management can help to identify and mitigate vulnerabilities before attackers can exploit them. This can help to reduce the risk of successful attacks and improve an organization’s overall security posture.
- Increased efficiency: Continuous Threat Exposure Management can help to streamline the process of identifying and mitigating vulnerabilities by continuously scanning for them and implementing measures to prevent or mitigate them. This can help to save time and resources that would otherwise be spent on manual vulnerability assessments and patching processes.
- Enhanced collaboration: Continuous Threat Exposure Management involves ongoing communication and collaboration between different teams within an organization, such as security, IT, and development. This can help ensure that vulnerabilities are addressed promptly and effectively and can also improve overall organizational efficiency.
- Greater visibility: Continuous Threat Exposure Management provides organizations with a continuous view of their exposure to vulnerabilities, which can help to inform decision-making and prioritize resources. To build a case on prioritization you can refer on our latest whitepaper
Which Team Map to CEM
CTEM and CEM interact with threat and incident response for managing incidents and vulnerabilities remediation
CTEM team work with the threat and secure posture optimization team (boots on the ground) to drive remediation and fixes
Threat detection and response will interact with the CTEM team to enrich vulnerability information and provide the latest trends and who is targeting which vulnerabilities.
The areas looked after by CTEM tend to span from code to cloud, including manual red team exercise, and pentest
What are the five steps that form the CEM and CTEM process
In a recent article, Gartner described the process of CTEM and the evolution of traditional vulnerability management.
Scoping Stage – The scope of the attack surface is evolved and exceeds the typical focus of vulnerability management programs and needs to evolve to encompass an extended asset and attack surface, from code and software artefacts to cloud and infrastructure artefacts.
When scoping the software assets, consider the following:
- External attack surface – which assets are external
- Internal attack surface – which assets are deployed where and how they are related to external assets
- Software and deployable assets – software artefacts that are deployed across the infrastructure, cloud, container and more environmental assets
- 3rd party assets – which 3rd party is connected to which asset
Discovery
Once the CTEM team has completed the scoping, it is essential to start analysing and discovering assets consolidating the asset surface in one location. Asset risk posture gets calculated at this stage. The more the assets are contextualized and mapped to the business and environmental contexts, the more the risk posture becomes precise.
Prioritization
The team that manages and drives vulnerabilities has the mission to help narrow down and focus on the 10% of vulnerabilities that are highly probable to be exploited and are internally exposed or interconnected to externally exposed systems. With business criticality context, the organization can narrow down the vulnerabilities that are more likely to get exploited.
Validation and Triage
When validating the security vulnerability, a security team looks at contextual compensating control and triages which vulnerabilities need to be treated first from a list of prioritized vulnerabilities.
Traditionally this process is the most painful and slow, with the team taking up to 9h to triage and select which vulnerabilities to fix when while the average time that a security team can dedicate to various engineering teams varies between 48 min per week to 10 min in larger enterprises.
Traditionally, this results in more time the security team spends on fewer applications to dedicate the required 9h. Automated triage aims to automate and speed up evidence collection and provide the security team with the fastest information.
Mobilization
The last but most important step is to mobilize and involve the various engineering teams to collaborate. In this step, security leaders must communicate and coordinate an approach to remediation with engineering teams. In this particular step is critical that CIO, CTO, and CISO agree on key metrics and remediation collaboration channels. Automate remediation helps speed up the process; nonetheless, the most effective programme uses a mix of communication and self-imposed targets by the various engineering teams. For more details on this, you can reference the latest whitepaper on SLA.
How can Phoenix security help from code to cloud assess and prioritize Cyber Security vulnerabilities?
Scope & Aggregation – In this part of the process, you would map the business functions that are in scope of the asset management and vulnerability management programme.
Diagnostic – aggregate, contextualize and understand who owns what and what’s the risk posture of the various applications and environments.
- Aggregate and contextualize vulnerabilities: aggregate vulnerability from multiple sources, deduplicate, contextualize and consolidate the vulnerabilities and assets in a central place.
- Map the assets into business applications and environments, enabling tracing who is maintaining what asset and tracing ownership.
- Prioritize and Contextualize – In this stage, you would leverage the contextual business elements like business criticality and environmental context like which asset is internal and external and what mitigating controls are being applied to which environment.
With the following information, you would be able to prioritize the vulnerabilities based on contextual elements
Once the process is complete, you will be able to move into the action part, which is composed of
- Triage and set risk target – triaging the vulnerabilities that are contextualized enables the security team to automatically consider
- How exposed are assets
- Who is targeting specific vulnerabilities
- Who needs to act on vulnerability
- What is the probability of exploitation of the vulnerabilities
Setting risk targets – when the assets are contextualized and prioritized is possible to establish the baseline risk profile of the organization and move into setting the desired risk level
- Act on Prioritized vulnerability – the final and most important step is to act on the vulnerability that matters most. Is important to deliver those vulnerabilities to the team that maintains the vulnerability. Phoenix security helps to trace who owns what assets and maintain dynamic asset registers.
Conclusions
Vulnerability management has evolved due to the modern and complex landscape. Vulnerability management teams are suffering from alert fatigue. A mature and effective process involves strategy, coordinating teams and agreeing collectively on objectives.
How can Phoenix Security Platform help?
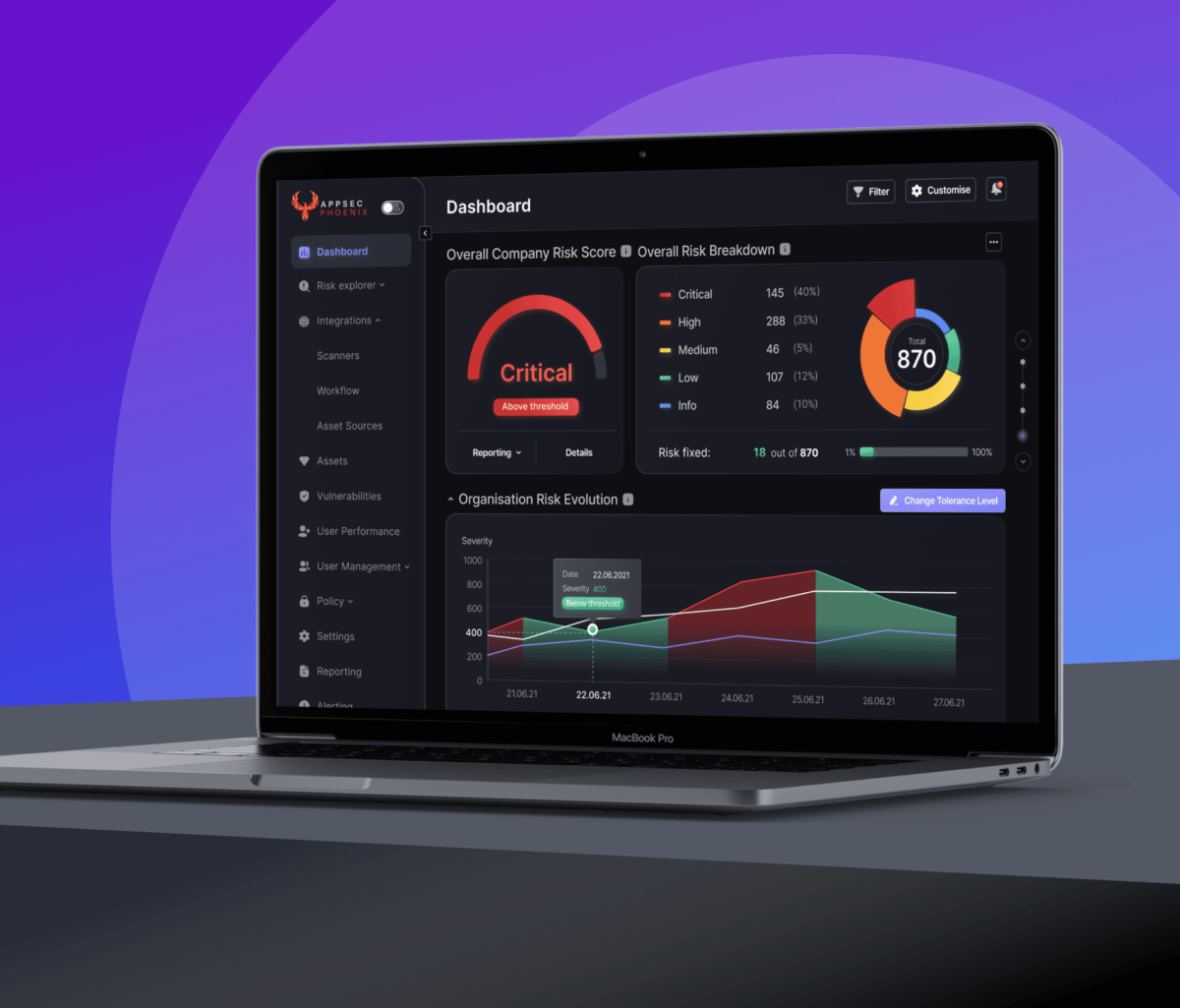
Technology is not the holy grail or answer to all the problems. Vulnerability management remains a people & culture, process, and technology problem.
Phoenix security cloud platform can help automate, correlate and track maturity at scale and facilitate the enforcement of measurements.
Phoenix offers a way to scale triaging and prioritising vulnerabilities, removing the manual part of security analysis and enabling the security team to scale better, from a 1:10 to 1:40 ratio, react faster (from 290 days average resolution time to 30) and be more efficient in the time spent on each vulnerability.
With a proven methodology adopted by more than 1000 Security professionals, Phoenix enables security engineers to communicate more effectively with the business in terms of risk and loss as well as automatically prioritise vulnerabilities for developers.



















