Background & Introduction
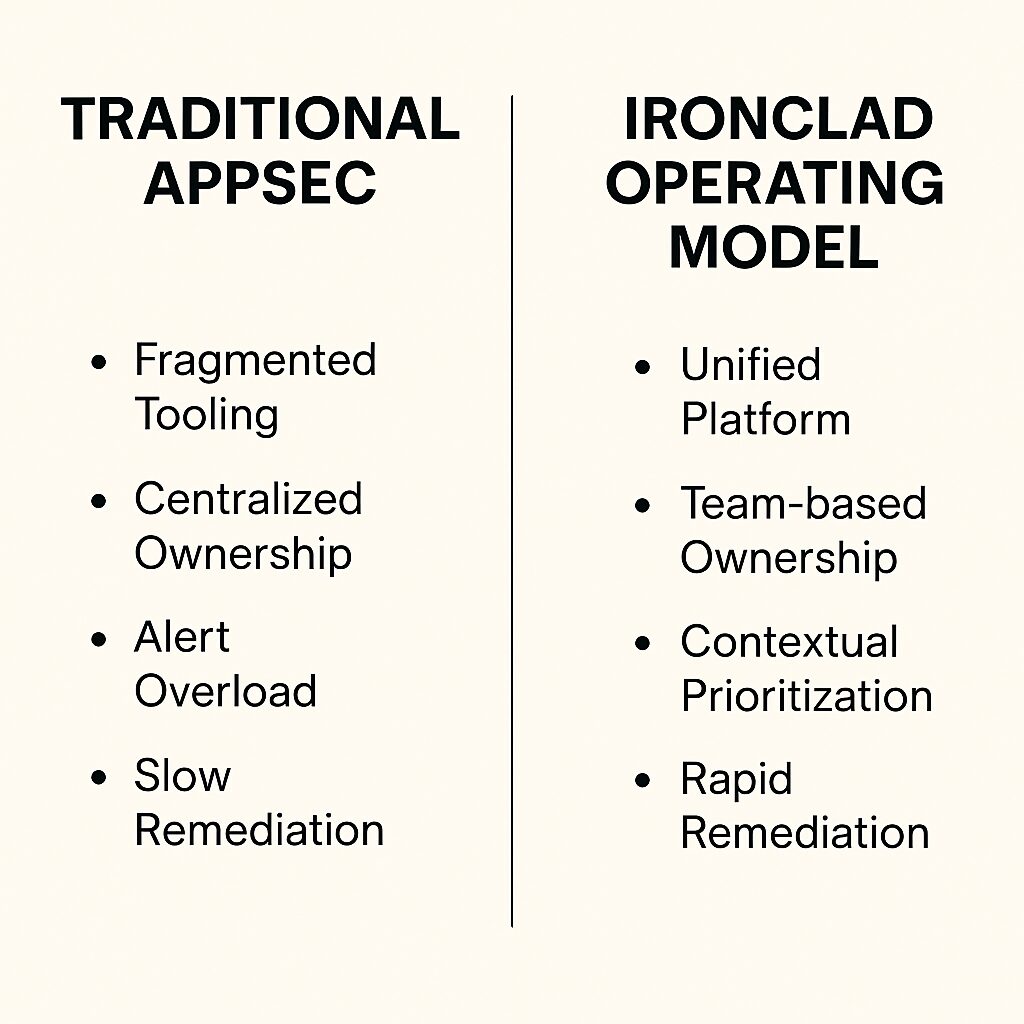
Application Security Posture Management (ASPM) has become a buzzword in the cybersecurity space over the last few years, and for good reason. ASPM promises to unify fragmented AppSec tooling, visibility from code to cloud, reduce alert fatigue, provide context from operation to security and development teams, and give enterprises real-time visibility into software risk. But here’s the truth, most vendors in the space won’t tell you:
ASPM won’t work if your operating model is broken.
That’s why it’s time for something more profound, deeper, simpler, and a new way of thinking. This post explores a modern security framework I’m calling IronClad™ – a hybrid fusion of philosophies combining ASPM with two battle-tested operating models:
- Brutalist Cybersecurity – clarity over complexity. Function and form over extravagance and polish.
- Team of Teams – decentralized, empowered execution. Decision-making pushed to the edge.
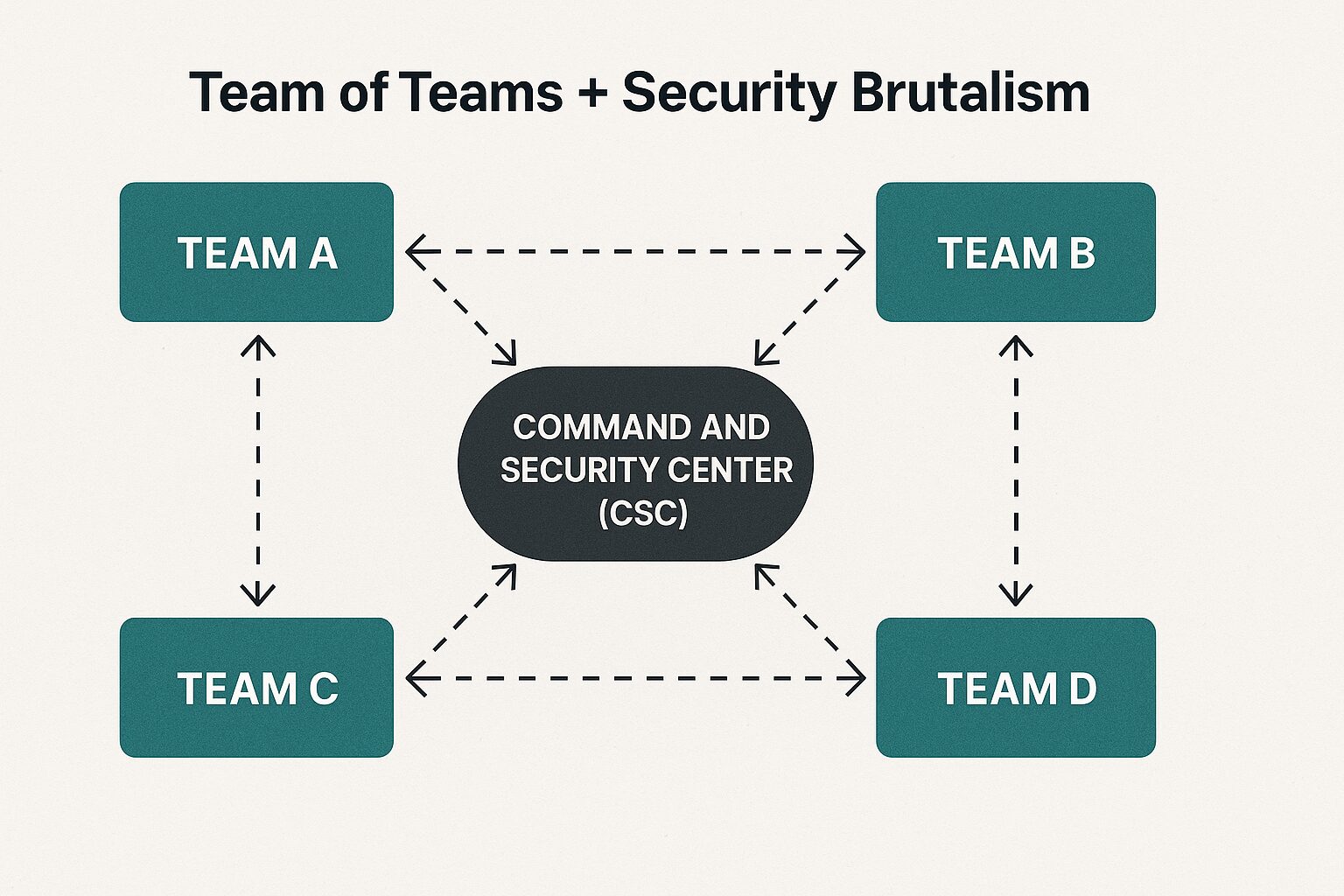
By combining these philosophies with ASPM, we’re not just securing code. We’re rewiring how organizations build, ship, and protect digital products of all kinds.
I owe a huge shoutout to a CISO I recently interacted with from a major Fortune 500 company. This post diving into these two topics is what prompted me to start down this journey of operating models and what the “why” is behind all of this.
Contents
ToggleWhat is Application Security Posture Management (ASPM)?
At its core, ASPM is a platform category designed to aggregate, normalize, and prioritize security findings across the software development lifecycle (SDLC). It’s a human-centric phrase that I believe is more important than the other “SPM”-based acronyms (DSPM, CSPM, etc.…).
It integrates with:
- SAST, DAST, SCA, IaC, and other scanning tools
- CI/CD pipelines
- Asset inventories and code repositories
- Ticketing systems and remediation workflows
The goal? To correlate vulnerabilities to business risk, route them to the right teams, and measure remediation effectiveness in a quicker, more real-time fashion.
But, even the best ASPM solution can’t succeed in an enterprise plagued by:
- Tool sprawl
- Siloed teams
- Unclear ownership
- Missing context
- Bureaucratic remediation loops
Sound familiar? This is where IronClad™ comes in.
What is IronClad™? A Framework for Modern Application Security
IronClad™ is a term I’m using to describe a return to the fundamentals of cybersecurity and building an operating model based on common sense. It’s a blend of:
- Brutalist Security: A security approach that focuses on raw functionality, minimalism, and durability.
- Team of Teams (inspired by Gen. Stanley McChrystal): Small, empowered squads operating with shared consciousness and decentralized decision-making.
Why “Iron” and “Clad”?
- Iron represents structure, accountability, and immovable clarity.
- Clad, meaning covered or encased, represents adaptability, real-time information flow, and interconnectedness.
IronClad™ turns traditional security programs into agile, mission-driven ecosystems. When paired with ASPM, it creates the infrastructure for real change, not just in tooling, but in behavior.
The Problem with Traditional Application Security
Modern applications break because security isn’t built in from day zero: Ideation, design, and architecture all matter but, it’s bolted on later, if at all. That delay creates friction, blind spots, and structural weaknesses:
- Security tools send alerts – nobody truly knows who owns what and where things really reside.
- Vulnerabilities are tracked in spreadsheets or disconnected ticketing systems and legacy methods.
- Devs are overwhelmed with false positives, causing them to not care, not innovate, and not fix what needs to be fixed.
- Remediation efforts stall because context is missing in a business-related way to give priority to the fix.
Most people think they have a vulnerability problem when the average organization I’ve seen actually has large set coordination problems. You may have thousands of criticals and highs. But how do you know which ones to solve to give you the biggest bang for your buck and reduce your risk the fastest and best?
ASPM + IronClad™: A New Operating Model for Application Security
Let’s talk implementation for a second. Here’s what I believe can happen when ASPM (The Tech System of Truth) and IronClad™ (The Management Philosophy) come together:
1. Unified Visibility and Ownership
- ASPM ingests all signals and maps them to applications, environments, business units, and teams.
- IronClad™ creates small security squads (“teams”) responsible for specific digital missions (e.g., Payments, Mobile App, Internal APIs).
Key elements: Secure design and architecture, application risk visibility, asset ownership, DevSecOps teams
2. Context-Aware Prioritization
- ASPM correlates vulnerabilities to business context: CVSS score, exploitability, data sensitivity, asset value, etc…
- IronClad™ ensures these insights go to the right teams with the authority to act.
Key elements: contextual vulnerability management based on risk and the ability to recover promptly.
3. Decentralized, Risk-based SLA-Second Remediation
- ASPM automates ticket creation, progress tracking, and feedback loops across Jira, GitHub, or ServiceNow.
- IronClad™ teams own remediation and mitigation workflows and empower devs to work with speed.
Key elements: application vulnerability remediation, security workflow automation, SLA tracking
4. Real-Time Reporting for Executives
- ASPM will serve as the record system for AppSec performance and digital risk exposure.
- IronClad™ promotes radical transparency – so everyone from engineers to CISO sees the same metrics (here’s an example of Brutalist Security metrics). It creates a unified language for everyone.
Key elements: AppSec KPIs, software risk dashboards, executive risk reporting
Real-World Impact: What This Looks Like in Action
I’m making an attempt to explain something that I’ve never explained before…Imagine a zero-day vulnerability hits your open-source dependency tree:
- This method requires acknowledgement that there is simply no silver bullet to achieve this outcome; technology and asset ownership with continuous automation are key to making this work. If the asset/systems are not owned, remediation can’t be addressed by the right team.
- ASPM can, if deployed correctly, slam visibility across repos and workloads, ranked by risk, not guesswork. It is critical to keep the owners up to date.
- IronClad™ squads/teams activate on impact. Ownership and asset tier dictate who moves. No ambiguity – just direct links between critical systems and those accountable.
- Remediation isn’t a ticket, it’s a mission. Patches hit target systems within hours based on criticality. No drift. No delay.
- Security leadership doesn’t wait for reports. Real-time information shows where the gaps are, and who’s closing them. Accountability is visible. So is progress.
I believe that this is not a future-state fantasy. This is an achievable reality if you align people, tooling, and operating models respectively and lead with trust. It fundamentally changes how we build things.
Common Pitfalls in ASPM & IronClad™ Adoption
When it comes to pitfalls we have to rethink this whole thing. You’re not just installing software – you’re building muscle with people who use tools to inspect software. Here’s what trips people up typically when they’re trying to do this, if they’re mature in their practices. Common issues that stall out this transformation include:
- Lack of executive sponsorship: You need top-down support to redesign the operating model, not just bottom-up implementation from a rogue AppSec team member.
- No clear asset inventory, no developer-friendly ownershipry: ASPM can’t prioritize risk if your CMDB is broken… How’s yours looking?
- Poor tagging discipline: Without tags for ownership and environment, IronClad™ collapses.
- Over-reliance on silver bullet thinking: Tools can’t fix broken accountability structures. It’s human work that yes, AI can help you document better but shouldn’t be left for AI alone as the cure-all.
These are all big themes in digital transformation in general, but you really need to chart a course with discourse before trying to radically shift. Decide on standards, naming conventions, and organizational structure. Then, evaluate and consolidate your tools and processes with the guidance of your teams and people.
Throughout my career, it’s been clear to me that businesses and organizations are reactive in this whole situation. We need to stop trying to band-aid the problem and rethink the entire approach and include leaders at every level in the shaping of the new way of thinking.
Why This Matters Now
Enterprise software is under siege:
- AI is accelerating code velocity and risk; traditional tools won’t keep up with millions of lines of code automatically generated by AI. Blocking code in pipeline levels will not be possible anymore, blocking release would be the gating of the future.
- Attack surfaces are expanding through microservices, APIs, and third-party code.
- Traditional AppSec programs are being left behind to sift through noisy alerts with legacy tools and processes.
- The number of CVEs keeps increasing by over 40K a year, with threats to the success of that program at a bureaucratic level.
ASPM gives you the visibility and prioritization layer you need to make decisions faster and more intelligently.
IronClad™ gives you the agility and accountability framework to act on it at scale.
Together, they offer something every security leader craves: Clarity in complexity. A center point for deriving insight and making informed decisions.
Final Thoughts: You Don’t Need Another Tool. You Need a New Model.
CISOs and security architects today are drowning in dashboards, alerts, pointless meetings, and general wastes of time. They’re focused on fixing rather than innovating. The future of application security isn’t more signal noise. Rather, it’s an intelligent, orchestrated response aligned with your org structure and business priorities.
If your current AppSec strategy feels like it’s held together with duct tape, consider this your invitation to rethink the operating model.
Start at the top. Leadership must treat security as structural, not optional. It’s not about uptime anymore – it’s about survivability. Without security embedded from the start, the foundation cracks. When it fails, it hits the business hard. And who suffers? The people.
Then, figure out whether ASPM is a good solution at the point in time you are in. Think of your business in terms of digital assets that are constantly going to be under threat and likely growing/changing.
If it is time for you to look at ASPM, invest in creating and deploying an IronClad™ based solution. Or at least read up on these books and interpret how you will. Make new teams and get people excited about the minimalist and direct nature of this philosophy. Upskill them to learn new technologies. Encourage open communication and dialogue top to bottom, left to right.
Build security that works, and overhaul what it means to have security in the board room, presenting around digital risk.
With that, I leave you to ponder these ideas and consider how they could be game-changing for you, your life, your team, your work fam, and your business.
More to come as this unfolds. If you have questions, comments, or just want to engage in healthy human to human dialogue, let’s talk and have coffee.
Until then, stay physically and digitally safe my friends!
Phil
Appendix
| Term | Definition |
| IronClad™ | A hybrid model combining Team of Teams and Security Brutalism for adaptive, decentralized, composable security operations. |
| CSC (Composable Security Cell) | Embedded, autonomous team(s) with risk accountability and remediation capabilities. |
| SIM (Security Intelligence Mesh) | Real-time visibility layer connecting vulnerability, context, and posture across teams. |
| IronDefaults | Mandatory, hardened configuration rules and baselines. |
| Iron Agents | Developers, Engineers, and People working on fixing vulnerabilities. |
















