Contents
ToggleWhy we believe the future of ASPM is Agentic Remediation
Application Security Posture Management (ASPM) is no longer an emerging trend; it is a must if you want to react in less than a few days and the cornerstone of modern application security programs. The IDC MarketScape: Worldwide ASPM 2025 Vendor Assessment highlights ASPM as the category born out of necessity — where traditional scanners and orchestration tools have failed, ASPM now delivers unified visibility, contextual prioritization, and remediation at scale.
The report covers legacy vendors with acquired capabilities, scanners with partial ASPM features, and AI-native vendors like Phoenix Security driving the code-to-cloud revolution.
Phoenix Security, recognized as a Major Player in the IDC report, has carved out a distinctive position by tackling what most vendors ignore: ownership attribution, noise reduction, and actionable remediation.
Francesco Cipollone, Co-Founder and CEO of Phoenix Security, expresses the sentiment:
“With organizations struggling to remediate, it is fundamental to automate attribution and help teams focus on the remediation that has the most impact and align this with business objectives.”
The Escalating Challenge: Vulnerabilities Outpace Teams and Why ASPM Is Part of the Solution
From Thousands to Hundreds of Thousands
In 2000, the National Vulnerability Database logged just over 1,000 CVEs. Fast-forward to 2024: more than 220,000 CVEs were recorded, representing a 35% year-over-year surge.
By 2026, projections place the annual number of vulnerabilities near one million – a staggering burden for any security team.
Budgets and Headcount Can’t Keep Up
Despite exponential growth in vulnerabilities, most security teams remain static. Budgets tick upward at 6% while vulnerability volumes explode by 35%. Security-to-developer ratios are stretched thin, often 1:40 or worse.
Only 1–10% of Issues Truly Matter
Research shows that just a fraction of these vulnerabilities are exploitable or business-critical. Yet legacy tools treat them all equally, burying teams under irrelevant alerts.
This imbalance – more noise, less context – is exactly what Phoenix Security set out to solve.
Phoenix Security’s Core Differentiator
The 4D Risk Model
Phoenix transforms vulnerability data into actionable intelligence with its 4D Risk Model, which evaluates:
- Ownership – assigning issues directly to accountable teams.
- Exposure – distinguishing internet-facing assets from internal ones.
- Business Impact – tying risks to critical services and revenue streams.
- Threat Intelligence – incorporating exploitability signals, KEV, and EPSS.
This approach collapses thousands of noisy findings into surgical task lists routed to the right owners.
Ownership: The Missing Link
Where many platforms stop at detection, Phoenix Security delivers “who does what, where, and why”. Vulnerabilities are not just discovered; they are mapped to applications, teams, and environments. This closes the accountability gap between security and engineering.
AI That Works With You, Not Against You
AI Agents That Work for Your Philosophy
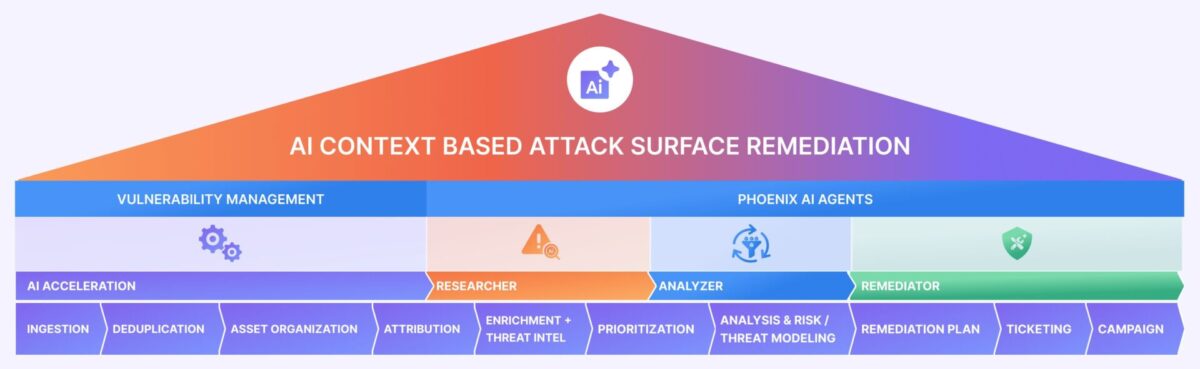
While competitors hype “AI-only” approaches, Phoenix Security follows an AI-enabling philosophy:
- Step 1: Clean, contextualize, deduplicate, and attribute vulnerability data.
- Step 2: Apply AI agents to accelerate prioritization and remediation.
The result: precision, not amplified noise.
The Three AI Agents

- The Researcher – evaluates vulnerability reports and dynamically calculates exploitability and ransomware likelihood using CTI, EPSS, and vulnerability intelligence feeds.
- The Analyzer – runs attack path simulations and enriches findings with threat models.
- The Remediator – automates routing, generates tailored playbooks, and consolidates related issues (e.g., multiple Log4J instances into one ticket) and proposes PR changes and fixes for developers to approve.
This trio transforms triage into an automated process, reducing the mean time to remediate (MTTR) by up to 90%.
Rethinking Metrics: Beyond SLA Compliance
Why SLAs Fall Short
Traditional vulnerability management measures success against SLA deadlines — 30 days for criticals, 90 for highs. But speed without context is misleading. Teams end up chasing deadlines rather than reducing meaningful risk.
Phoenix’s Approach
Phoenix equips CISOs with metrics that connect security work to business outcomes:
- MTTR by severity – real performance, tracked once the right team is informed.
- SLA/SLO non-compliance trends – identifying bottlenecks and resource gaps.
- Guardrail coverage – measuring how many vulnerabilities are structurally prevented.
- Risk reduction targets – focusing on outcomes, not ticket counts.
By aligning remediation progress with revenue, uptime, or compliance impact, Phoenix Security enables security leaders to defend budgets and priorities at the board level.
Case Studies: Proof at Scale
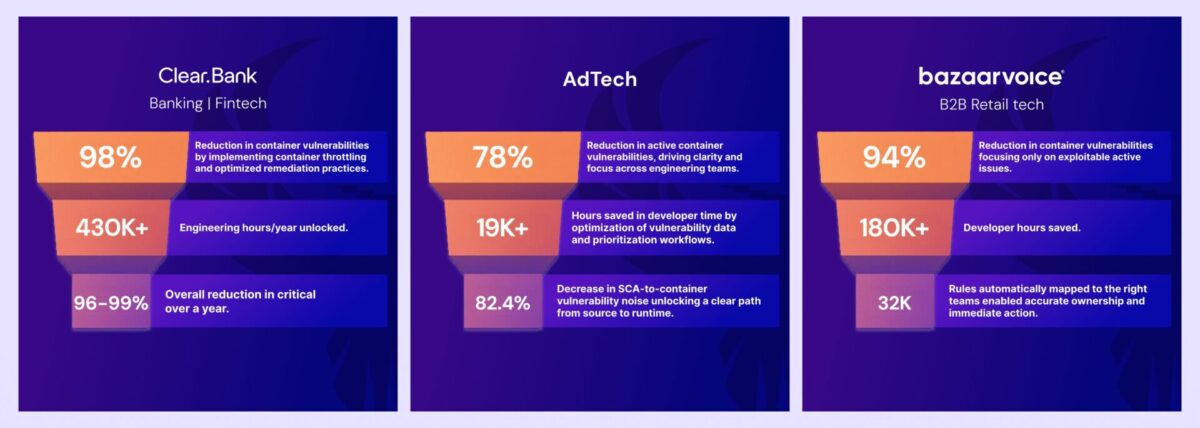
ClearBank: Container Noise Cut by 98%
ClearBank, the UK’s first clearing bank in two centuries, faced exploding vulnerability volumes from containerized workloads. Traditional tools buried them in duplicate findings and stale images.
With Phoenix Security, ClearBank achieved:
- 98% reduction in container vulnerabilities.
- >95% drop in critical risk, achieving 0 critical risk.
- Developer time saved, reclaiming 2-4 hours per engineer per week, with teams achieving 0 critical risk focusing on the remediation that matters most.
ClearBank scaled security operations without scaling headcount – the essence of risk-based DevSecOps.
Bazaarvoice: cut 94% container noise and improve Developer-security communication and precision
Bazaarvoice, a global leader in user-generated content, struggled with container sprawl and manual team attribution. Phoenix Security enabled aggressive container throttling and automatic ownership mapping.
Results included:
- 94% reduction in container vulnerabilities.
- 32K rules auto-mapped from Backstage for ownership clarity.
- Teams remediated all critical risks within the first month of adoption.
Bazaarvoice shifted from reactive triage to proactive DevSecOps, integrating vulnerability management directly into developer workflows.
Ad-Tech: Noise Reduction from Container to Code Without Burnout
A major AD-Tech needed to cut vulnerability noise across sprawling pipelines without hiring more analysts.
Phoenix Security delivered:
- 78% reduction in active container vulnerabilities.
- 82.4% reduction in SCA-to-container noise.
- Improved communication security – developers with teams registering clarity of actions and precise direction from security.
Phoenix’s contextual deduplication and container lineage ensured that engineers fixed what truly mattered – not every theoretical risk.
The recognition of IDC strengthens ASPM belief
As Phoenix Security, we are honoured by this high recognition as a major player with one of the highest capabilities and at the border with Leadership
We believe in those principles that have provided us the recognition from names like Clearbank, Bazaarvoice, and more retail and finance sector clients
● Remediation focus: going beyond dashboards and SLAs to measurable business outcomes.
● Threat-centric prioritization: correlating exploitability, reachability, and attacker behavior.
● Customer-driven innovation: rapidly developing features like remediation campaigns and one backlog in response to client needs.
Roadmap: What’s Next for Phoenix Security
The ASPM category is rapidly converging with adjacent markets — CNAPP, exposure management, and vulnerability management. Phoenix is already pushing ahead with:
- Reachability analysis – pinpointing exploitable vulnerabilities in runtime.
- Agentic remediation campaigns – systemic fixes applied across services.
- Ownership as code – embedding attribution in CI/CD pipelines.
- Compliance integrations – aligning with FedRAMP, SOC2, and NIS2 requirements.
These capabilities reinforce Phoenix’s role as a unifying force in DevSecOps, consolidating tools and delivering measurable business impact.
Why Phoenix Security Matters Today
Attackers now exploit vulnerabilities within days; defenders often take months. The gap is widening. Traditional scanners and SLAs cannot close it.
Phoenix Security has built a platform designed for this new reality:
- 98% less noise through contextual deduplication.
- Millions saved in developer and analyst time.
- Ownership is mapped across code, container, and cloud.
- AI agents that accelerate remediation without losing human control.
ClearBank, Bazaarvoice, and a major Ad-Tech giant already know it: Phoenix Security makes DevSecOps scalable, measurable, and effective.
For CISOs and AppSec leaders, the message is clear: if dashboards no longer move the needle, it’s time to embrace precision over volume. Phoenix Security is the Major Player delivering exactly that.
Get on top of your code and container vulnerabilities with Phoenix Security Actionable ASPM powered by AI-based Reachability Analysis

Organizations often face an overwhelming volume of security alerts, including false positives and duplicate vulnerabilities, which can distract from real threats. Traditional tools may overwhelm engineers with lengthy, misaligned lists that fail to reflect business objectives or the risk tolerance of product owners.
Phoenix Security offers a transformative solution through its Actionable Application Security Posture Management (ASPM), powered by AI-based Contextual Quantitative analysis. This innovative approach correlates runtime data with code analysis to deliver a single, prioritized list of vulnerabilities. This list is tailored to the specific needs of engineering teams and aligns with executive goals, reducing noise and focusing efforts on the most critical issues.
Why do people talk about Phoenix?

• Automated Triage: Phoenix streamlines the triage process using a customizable 4D risk formula, ensuring critical vulnerabilities are addressed promptly by the right teams.
• Contextual Deduplication with reachability analysis: Utilizing canary token-based traceability for network reachability and static and dynamic runtime reachability, Phoenix accurately deduplicates and tracks vulnerabilities within application code and deployment environments, allowing teams to concentrate on genuine threats.
• Actionable Threat Intelligence: Phoenix provides real-time insights into vulnerabilities’ exploitability, combining runtime threat intelligence with application security data for precise risk mitigation.

By leveraging Phoenix Security, you not only unravel the potential threats but also take a significant stride in vulnerability management, ensuring your application security remains up to date and focuses on the key vulnerabilities.
















