If your security program still relies on legacy tools, you’re solving yesterday’s problem. Traditional ASOCs and risk-based vulnerability management (RBVM) buried teams under alerts without context. Even early ASPM platforms lacked true business alignment. What today’s enterprises need is ASPM application security vulnerability management built for DevSecOps and code-to-cloud security—a strategy that cuts noise, ties risk to business impact, and drives remediation engineers can actually deliver.
Fast-forward to a world of cloud-first, container-native infrastructure. The attack surface isn’t just expanding—it’s morphing. Application components shift daily. Containers spin up and down in minutes. Infrastructure is no longer static. And neither is risk.
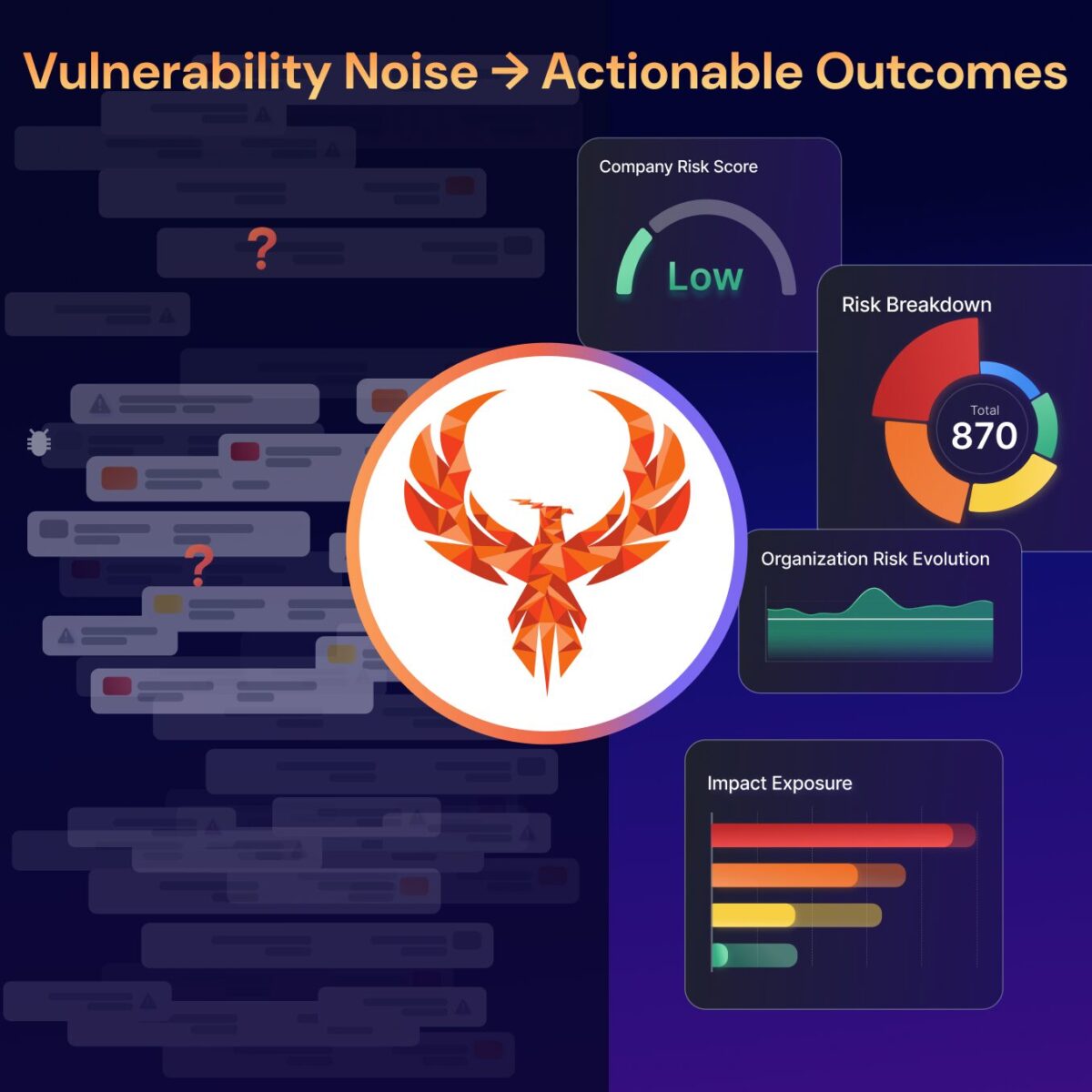
This environment demands a new strategy—AI remediation-aware exposure management that communicates with the board and ownership, and provides quantification, and remediation to the engineers.
From Noise to Navigation: The Shift Beyond RBVM
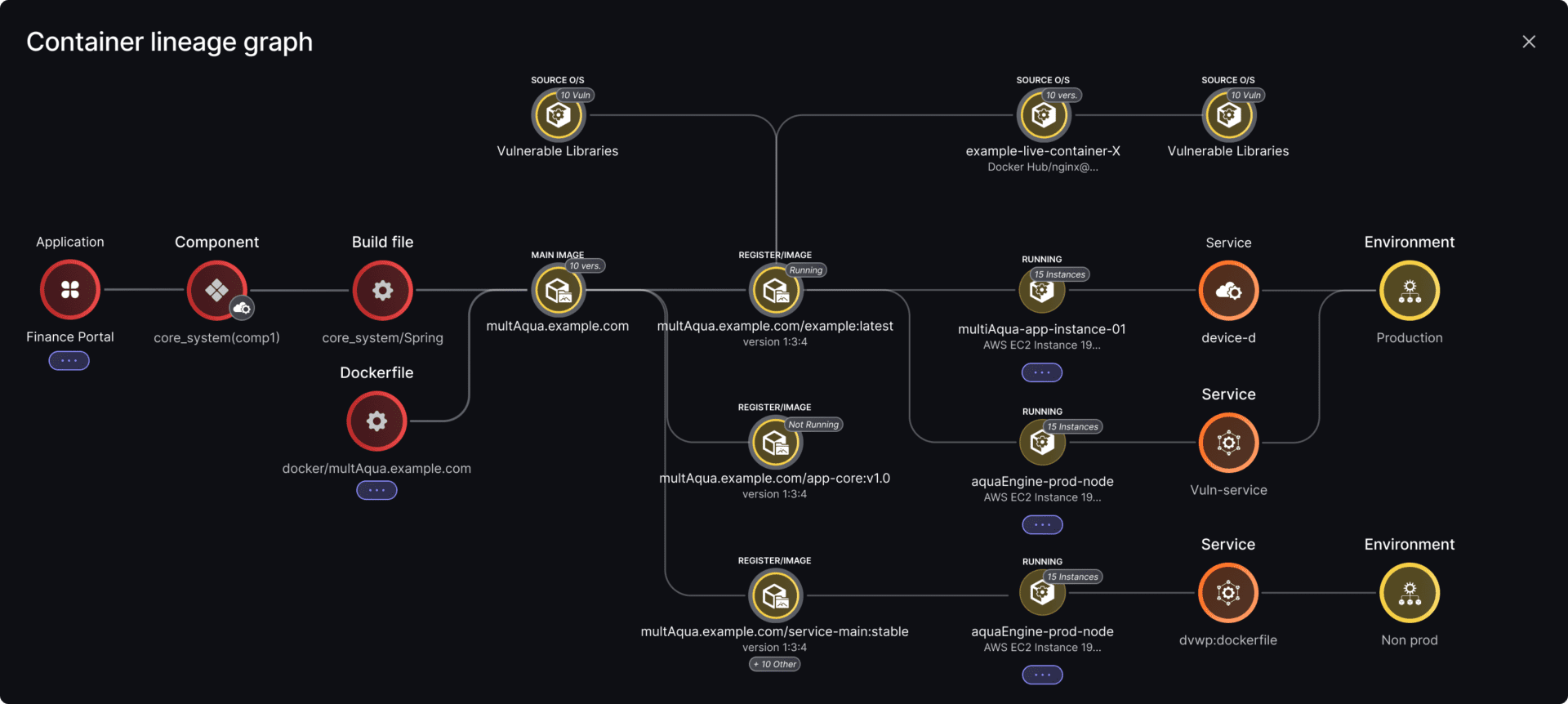
Let’s get this out of the way: CVSS-based prioritization is broken. A critical vulnerability in a dark corner of the infrastructure no one uses is not your biggest risk. A medium-severity flaw sitting in an internet-facing, business-critical container with active exploitability is. A library being deployed in a container sitting in a registry is not dangerous if that container is not loaded. A library with remote code execution or other common exploited technique, deployed in a container, exposed to the web is way more dangerous. That’s the concept of code to cloud lineage.
RBVM made a valiant attempt to sort signal from noise. But it focused on ranking and mostly on Virtual machines, AMI, and similar. The world has moved on a long time ago, and the attack surface spans from code, cloud, misconfiguration, and identity. RBVM told you what looked dangerous. It didn’t help you understand if it was exploitable, reachable, or even relevant. And it left the “now what?” question unanswered.
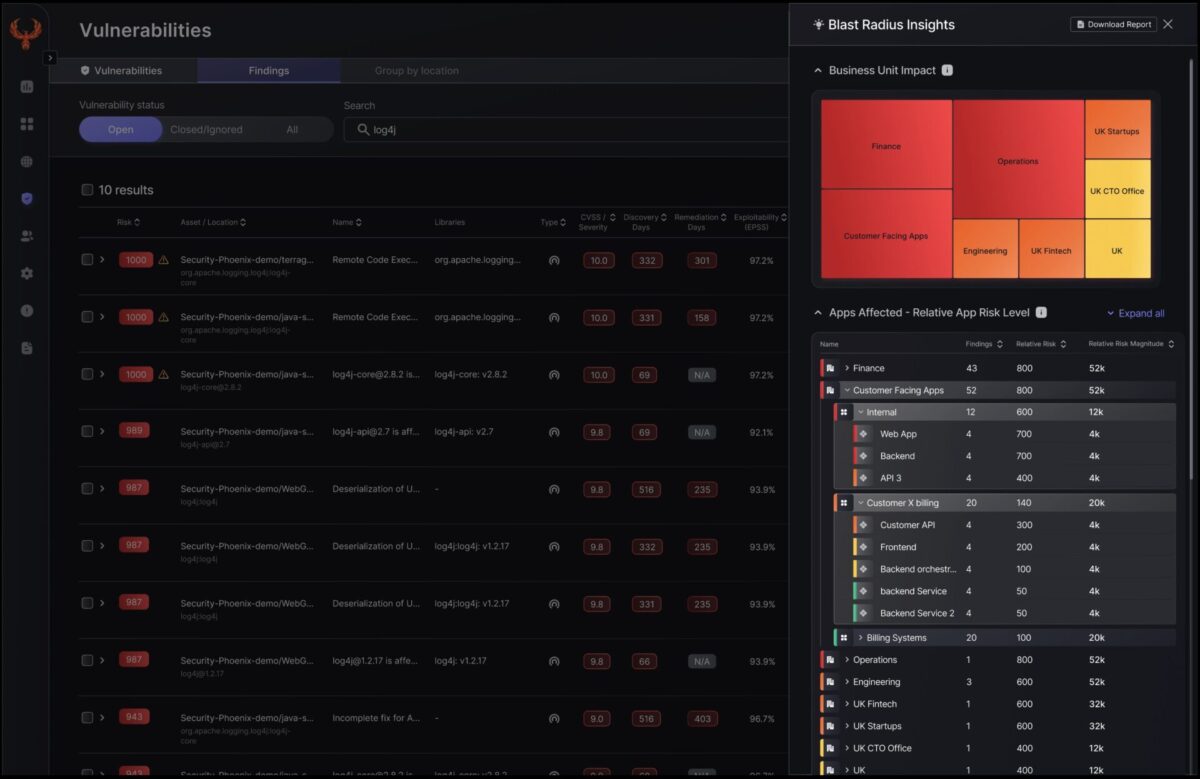
That’s where exposure management steps in. But exposure can’t be explained at the board level. A CISO needs to be able to translate all these complex topics into: what are the risks I’d like to reduce, which business unit and team is more affected by it? And most importantly, which team needs more help and attention? That’s where blast radius analysis and quantification of the cyber risk exposure come in.
Exposure Management Is Not Just Asset Inventory
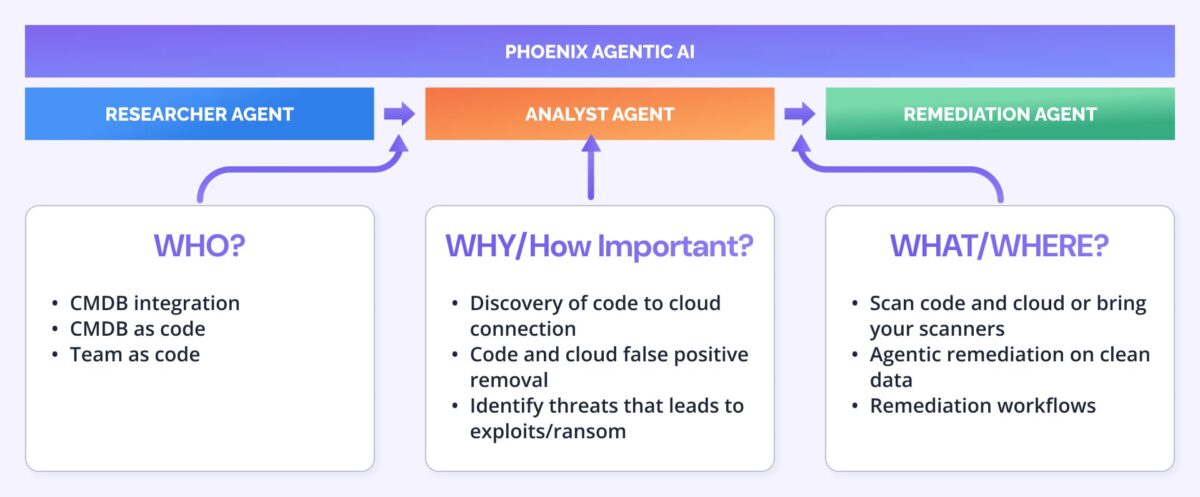
Exposure management is often misused to describe asset visibility tools. That’s not it. Knowing what you have is foundational, but exposure management goes further.
It answers:
- Who owns what? (And yes, that includes GitHub repos, Kubernetes clusters, and SaaS misconfigurations.)
- What and where are the exploitable elements across code, containers, infra, and cloud?
- Why do they matter? Correlated threat intel, runtime visibility, reachability, business impact.
- How should we fix it?
Only by answering all four does a security program evolve from reactive scanning to proactive risk reduction.
YAML-Based Remediation: DevSecOps in Developer Terms
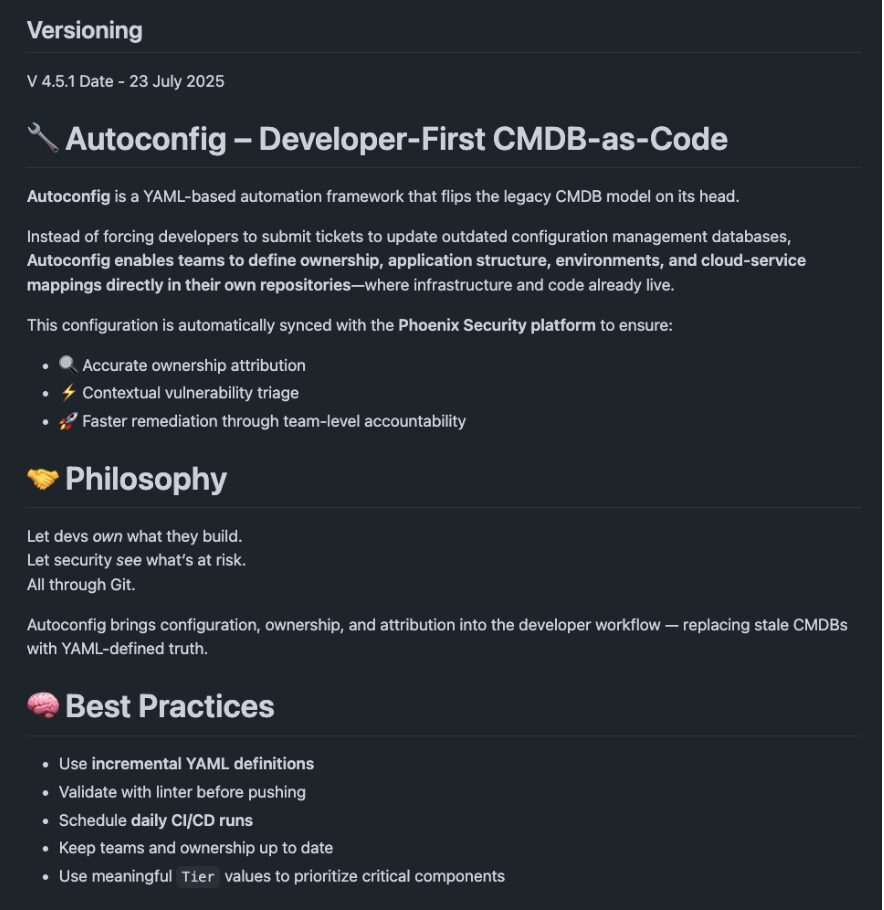
Ownership shouldn’t live in an outdated CMDB that no developer touches. It should live where developers already work—inside the repository, in the CI/CD, in YAML.
Phoenix Security enables YAML-based remediation metadata that brings security ownership into developer territory:
- Teams define their application ownership directly in version-controlled YAML.
- Asset metadata, ownership, and remediation priority are declared as code.
- CI/CD workflows validate the structure and sync with Phoenix APIs.
The result: frictionless attribution and remediation planning without forcing developers to log into yet another system. YAML becomes the new interface for modern DevSecOps ownership.
Don’t force developers into an outdated CMDB. Bring asset intelligence into their flow with Phoenix Security’s YAML CMDB and Backstage integration.
This is what real DevSecOps looks like: asset-driven security, defined by developers, automated by pipelines, backed by context.
The Evolution: From ASOC to Exposure-Aware Application Security Exposure and CTEM
First, ASOCs created centralized places to collect alerts. Then came RBVM to try and make sense of them. Today, the modern iteration is Continuous Threat Exposure Management (CTEM)—a Gartner-backed concept aligning exposure awareness with remediation workflows and threat-informed decisions.
CTEM isn’t a technology, It’s a methodology that continuously:
- Assesses exposure
- Validates exploitability
- Prioritizes based on real business and operational context
- Drives action, not just visibility
With ASPM, and UVM (unified vulnerability management) we’ve evolved into application application-aware attack surface powered by context-aware remediation
Remediation-aware exposure management is the execution engine for CTEM. It’s how context turns into response.
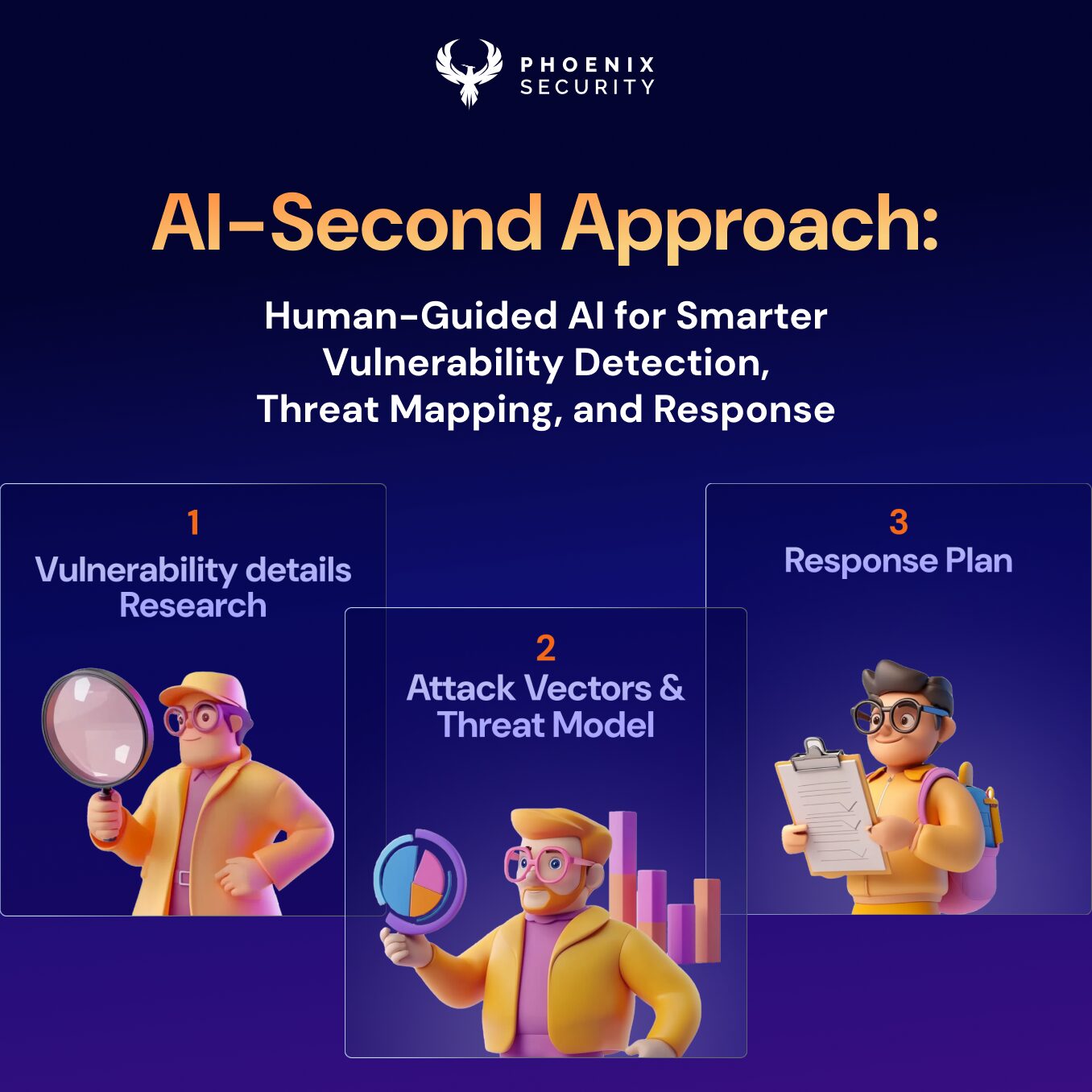
Why AI-First Isn’t Enough—You Need Agentic Remediation backed by a solid data model

Some vendors are racing to inject AI into everything. AI-first vulnerability management. AI-first prioritization. It sounds impressive. Until you realize it’s often smoke and mirrors, expensive, and riddled with hallucination.
If you can’t ask the question to AI properly, an LLM model or an agent will just give a more confused, tough, credible answer.
AI that doesn’t know what to do next is just a smarter version of the same noise.
True transformation happens with agentic remediation AI—AI that can suggest or even orchestrate remediation plans, with context. We’re not talking about generic “patch it” advice. We’re talking about AI correlating:
- Reachable code paths
- Exploitable configurations
- Ownership and operational constraints
- Mitigation alternatives when patching isn’t an option
This isn’t theoretical. At Phoenix Security, it’s already in motion. Our platform fuses AI-powered threat intelligence with contextual correlation across application security, cloud posture, runtime, and container behavior.
The future is exposure management fueled by AI agents that empower context-based remediation, moving away from AI-enhanced vulnerability description into contextually aware remediation plans.
The output? A remediation plan that makes sense to developers. Not just risk scores and CVEs.
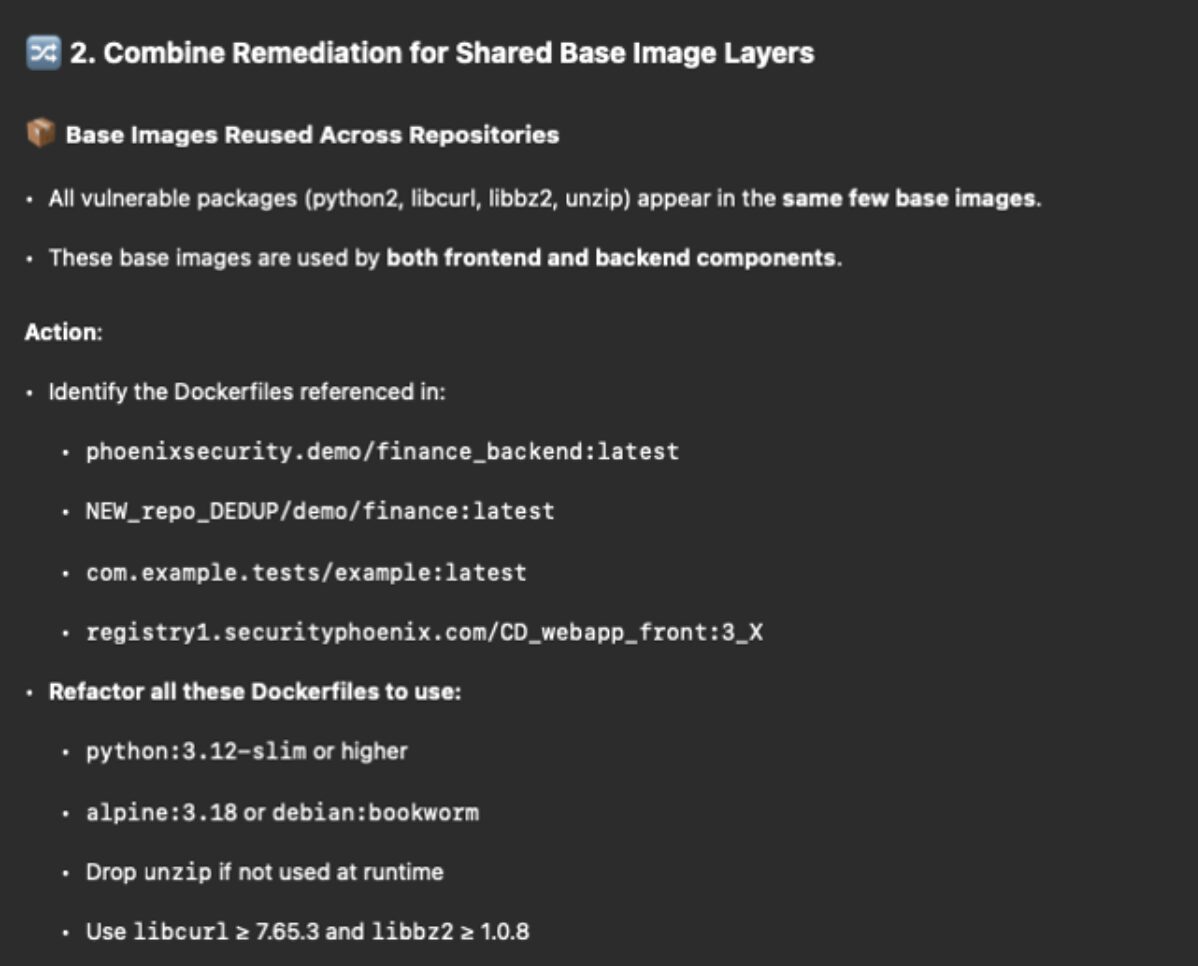
An example of output in a containerized environment with libraries needing upgrade, which library would you consider when upgrading? The answer is the library with low-hanging fruit and more critical vulnerabilities; choose libraries that are reachable from code to cloud.
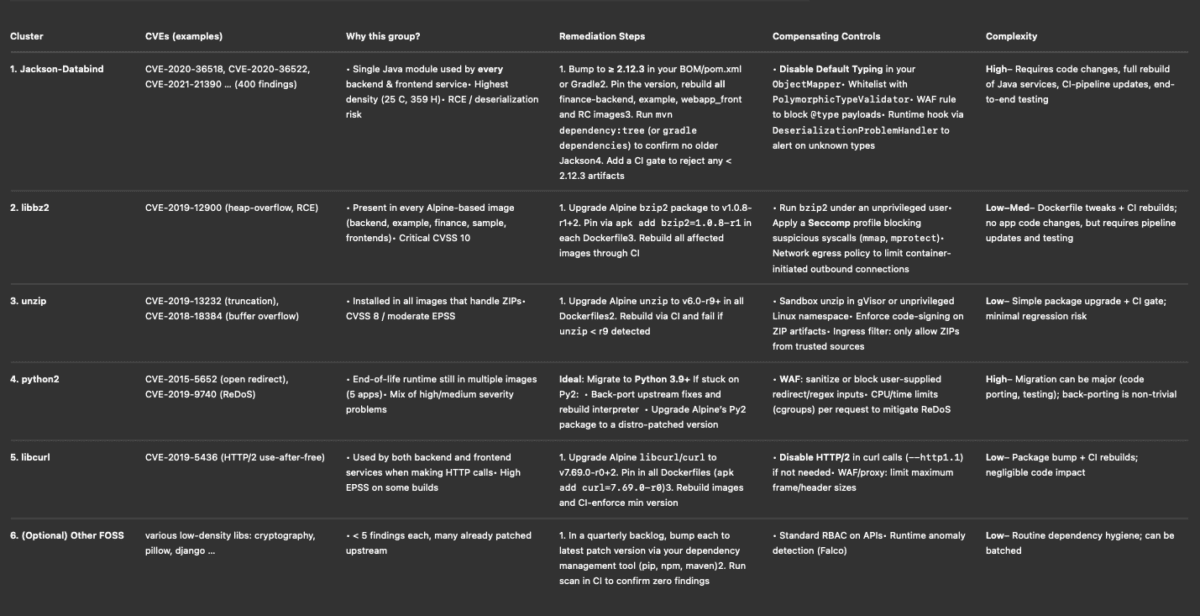
Remediation Is a Workflow, Not an Alert
A remediation-aware exposure program doesn’t stop at identifying what to fix. It owns the fixed path.
That means:
- Auto-ticketing with rich context (ownership, asset, exploitability, affected environments)
- SLA and SLO tracking over time, broken down by severity
- MTTR per severity group, mapped to team and component
- Tracking what was fixed, what escaped, and what’s resurfacing
Security isn’t measured in the number of criticals found. It’s measured in time-to-remediate what matters. And what gets remediated depends entirely on exposure context.
Metrics That Matter
Let’s get surgical with metrics. Volume-based KPIs are vanity. Real programs are looking at:
- SLA/SLO non-compliance by severity
Track how often you’re failing your fix targets. By severity, per team, per environment. - MTTR from the moment the team was informed
Not when the scanner found it. When the team was made aware. That delta shows where communication, not technology, breaks down. - Escape rate
Vulnerabilities that make it into production. Because security late in the SDLC is too late. - Risk reduction over time
Number of resolved exploitable + reachable risks. Not CVEs. Risks.
These aren’t theoretical. They’re emerging from conversations with leading practitioners like Matt Boddy, James Bethoty, Chris Romeo, Katie Norton, and others who are tired of chasing ghosts in dashboards.
AI Without Context Is a Liability
Context-free AI sounds innovative. It’s not. It’s dangerous.
Imagine an AI suggesting patching a library that’s never executed, in a container that spins up once a month for a batch job. Or flagging a critical CVE in a test environment with no external exposure.
Now imagine security teams chasing that. Wasting time. Burning out developers. Missing the real attack paths.
Context-aware, remediation-first AI changes the game:
- Graph-based correlation of vulnerabilities, code, infra, and users
- Threat intel embedded in remediation recommendations
- Lineage-aware decisions—knowing whether a vulnerability impacts a dev branch, a staging system, or prod
It’s the difference between a static scanner and a surgical recommendation engine.
Real Remediation. Not Just Noise Reduction.
Exposure management is not the destination—remediation is. The difference lies in remediation that is prioritized by exploitability, reachability, and business impact, mapped to real ownership, and connected across code-to-cloud security. This is where ASPM application security vulnerability management evolves beyond dashboards, delivering measurable outcomes: faster MTTR, reduced escape rates, and remediation workflows developers adopt naturally.
Legacy platforms chased criticals. Phoenix Security’s ASPM platform drives context-aware remediation—bringing together attribution, exposure, and threat intelligence into a single flow. We don’t aim to solve everything. We focus on mastering exposure management for application security and vulnerability management—because that’s where risk is reduced, trust is earned, and business moves faster.