Security promises are only as strong as the evidence behind them. Phoenix Security has completed its SOC 2 Type 2 audit and successfully received the corresponding SOC 2 Type 2 report, reinforcing our long-standing commitments to data privacy and ISO 27001 standards. Type 2 is the rigorous one: it evaluates control design and operating effectiveness over time, not just at a single point. That distinction shows our controls don’t just exist—they consistently work. Our journey was accelerated by the automation delivered by Vanta and a successful audit from Advantage Partners, cutting our audit effort and time by 50%
Contents
ToggleSOC2 Type 2: The signal our customers asked for
Our customers run modern software at scale and expect verifiable assurances. SOC 2 Type 2 sits alongside ISO 27001 as proof that Phoenix Security’s people, processes, and platform protect data with discipline—while our product helps your teams cut noise and fix what matters.
- ClearBank – cut container vulnerability noise by 98%, reduced weekly criticals by 96–99%, and saved millions of dollars in analyst time by focusing on real, exploitable risk, not duplicates.
- Bazaarvoice – achieved a 94% reduction in container vulnerabilities and reclaimed $6.3M in developer time by integrating Phoenix Security into developer workflows.
- Integral Ad Science (IAS) reduced 78% of active container vulnerabilities and decreased SCA-to-container noise by 82.4% through code-to-cloud correlation and contextual deduplication.
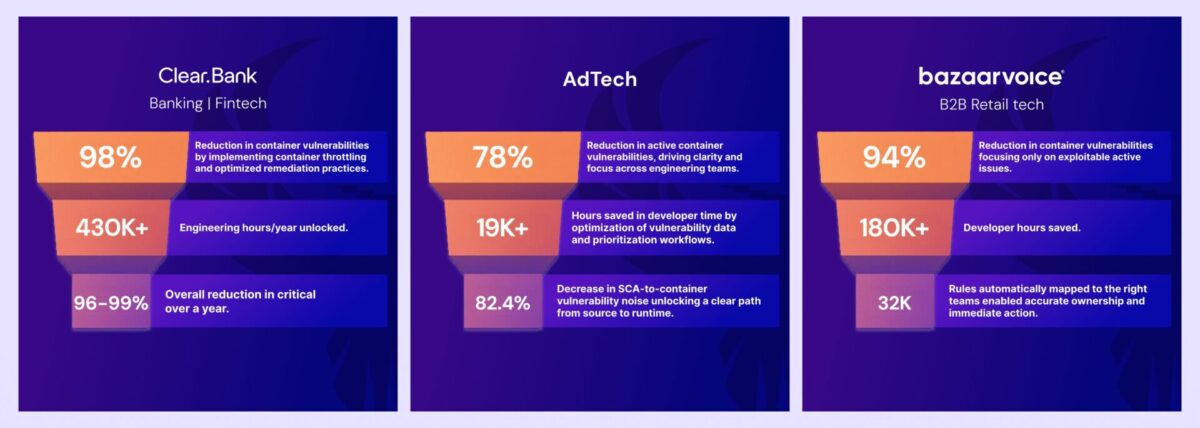
These aren’t vanity metrics; they reflect day-to-day operational wins our platform enables across regulated and high-velocity environments.
SOC2 Type 2 vs. Type 1, in plain language
- Type 1: “Are the controls designed properly right now?”
- Type 2: “Are the controls designed properly—and do they keep working over an extended period?”
Type 2 is the higher bar our customers expect for ASPM and vulnerability management vendors that handle sensitive telemetry and workflow data.
Innovation that backs the certificate
Phoenix Security’s Actionable ASPM goes beyond dashboards to deliver precise, team-owned actions. Recent innovations include:
- Reachability Analysis (static + runtime) and Contextual Deduplication — strip out non-reachable findings in code and non-exploitable issues in containers; customers see up to 91% noise reduction when combined with container version control.
- One Backlog — a single, prioritized backlog per team with dynamic attribution across code and cloud, accelerating remediation and collaboration.
- AI-guided Remediation Campaigns — trend monitoring, team routing, and bulk actioning for systemic classes of risk (think Log4j-style campaigns), aligned to CISA/NCSC guidance.
- 4D Risk Formula — real-time weighting of business context, vulnerability, dangerousness, probability of exploitation, and deployment context to rank what truly matters.
Phoenix was built compliant to work alongside your teams
Phoenix AI Agents are designed to augment your workflow—not replace it:
- Researcher: enriches findings with active threat intelligence and exploitability.
- Analyzer: models attack paths and highlights reachable risks across code-to-cloud.
- Remediator: generates fix guidance, compensating controls, and smart routing into developer tools.
This approach is why teams like ClearBank, Bazaarvoice, and IAS compress time-to-remediate without inflating cognitive load.
SOC2 Type 2 is a recognition from the market
Independent reviews and analyst programs have highlighted Phoenix Security for features, ease-of-use, and customer success—another signal that product and practice align.
Accessing the report
The SOC 2 Type 2 report is available to customers and qualified prospects under NDA in the TPRM Trust Portal and Phoenix Security Trust Portal
How Phoenix Security Can Help

Organizations often face an overwhelming volume of security alerts, including false positives and duplicate vulnerabilities, which can distract from real threats. Traditional tools may overwhelm engineers with lengthy, misaligned lists that fail to reflect business objectives or the risk tolerance of product owners.

Phoenix Security offers a transformative solution through its Actionable Application Security Posture Management (ASPM), powered by AI-based Contextual Quantitative analysis and an innovative Threat Centric approach. This innovative approach correlates runtime data with code analysis and leverages the threats that are more likely to lead to zero day attacks and ransomware to deliver a single, prioritized list of vulnerabilities. This list is tailored to the specific needs of engineering teams and aligns with executive goals, reducing noise and focusing efforts on the most critical issues. Why do people talk about Phoenix

• Automated Triage: Phoenix streamlines the triage process using a customizable 4D risk formula, ensuring critical vulnerabilities are addressed promptly by the right teams.
• Contextual Deduplication: Utilizing canary token-based traceability, Phoenix accurately deduplicates and tracks vulnerabilities within application code and deployment environments, allowing teams to concentrate on genuine threats.
• Actionable Threat Intelligence: Phoenix provides real-time insights into vulnerability’ exploitability, combining runtime threat intelligence with application security data for precise risk mitigation.

By leveraging Phoenix Security, you not only unravel the potential threats but also take a significant stride in vulnerability management, ensuring your application security remains up to date and focuses on the key vulnerabilities.