Phoenix Security is excited to announce a series of new enhancements and features in our Application Security Posture Management (ASPM) and cloud security engines. This update is packed with crucial advancements in various areas of our platform, ensuring a more robust management of application security and vulnerabilities.
Key Updates in Application Security Posture Management (ASPM)
- New Weighted Asset Risk Formula: We’ve introduced a refined Asset Risk aggregation formula that better balances mathematical precision and intuitive risk assessment. You can adjust and even remove the vulnerabilities in the overall reporting metrics. The new weighted average risk formula allows users to tailor risk levels to their specific needs, enhancing our ASPM capabilities.
- Auto-approval of Risk Exceptions: To streamline the mitigation process, Phoenix now allows security specialists to auto-approve risk mitigation requests, reducing redundancy and speeding up response times to critical vulnerabilities.
What’s coming:
- Container Lineage and a more detailed view of which image runs where and which vulnerability can be skipped
- Threat Centric view of vulnerabilities with the first AI agent to provide a detailed analysis of the vulnerability and the threats affecting your system
- Cyber threat intelligence premium with more than 128000 Exploits to enhance the Exploitability and fixability metrics (available in preview for professionals and already included for enterprise customers)
- Exceptions workflows to write exceptions at scale
Summary of all the other updates
- ASPM
- Enhanced Impact and Risk Explorer
- Business Unit Insights within Dashboard
- Asset and Vulnerability Management:
- Link findings to existing GitHub and ServiceNow tickets for streamlined workflows.
- Multi-finding ticketing for Azure DevOps.
- Selection of Ticket Project for Linking Findings.
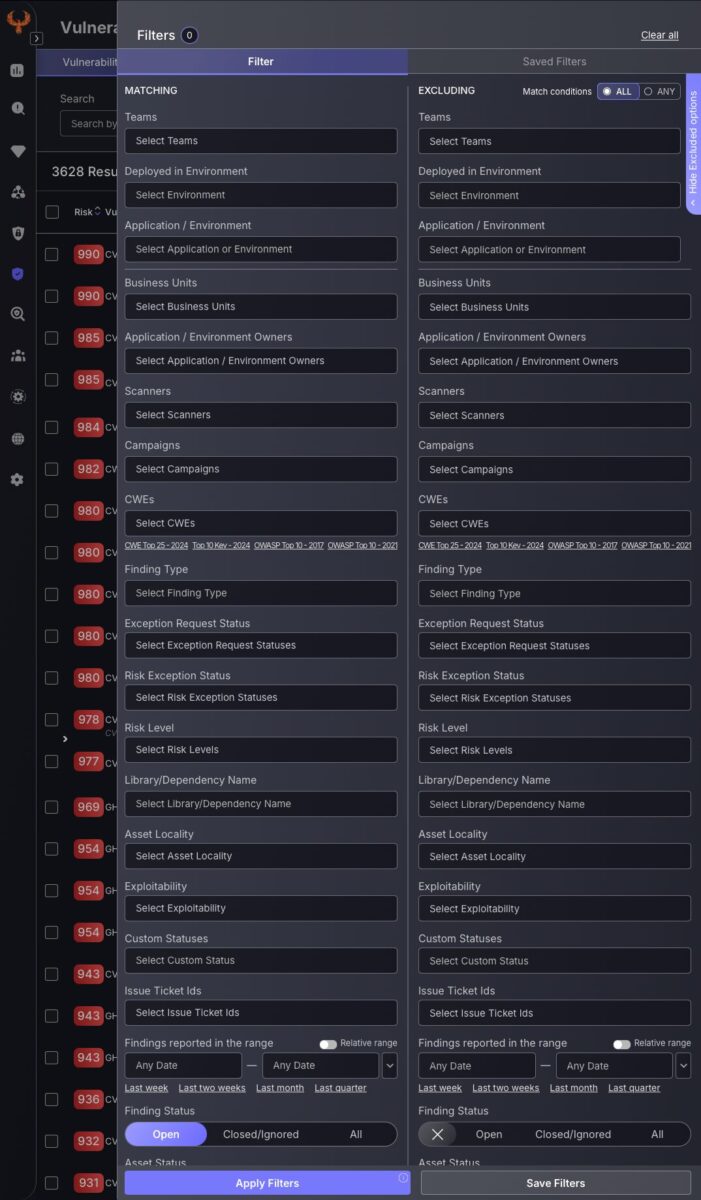
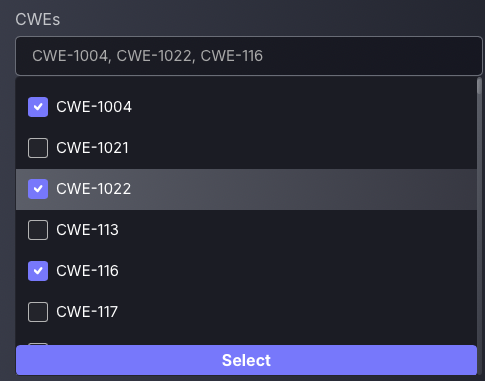
- Filter findings by business units, exclusion conditions, CWE codes, and ownership.
- Search assets by deployment environment.
- Integrations:
- Enhanced Lacework container management for improved scanner reports.
- REST API now supports asset tags for streamlined deployments.
- Other Components:
- Added CVE and CWE columns for better comparison.
- Improved custom status management for findings.

We are sure that you’ll find these quite interesting!
Application Security Posture Management
- Enhanced Impact and Risk Explorer: Navigate the complexities of organizational risk with our Impact and Risk Explorer side panel.
- Buisness Unit Insights within Dashboard: We’ve enhanced our risk explorer to segregate branches of vulnerabilities by business units to easily monitor organizational impact.
Asset and Vulnerability Management
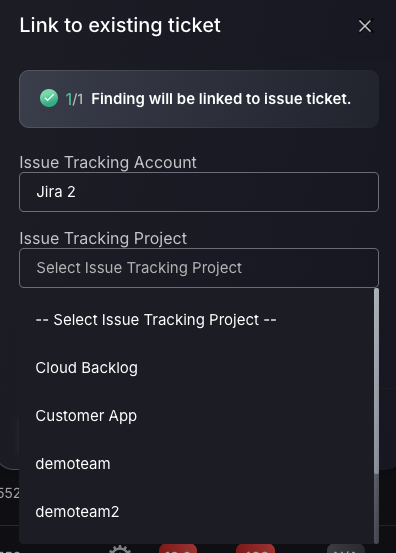
- Link Findings to Existing Tickets for GitHub and ServiceNow: Streamline remediation workflows by integrating with GitHub and ServiceNow. This extension allows users to link findings to existing tickets with complete flexibility.
- Multi-Finding Tickets for ADO: Simplify workflow management with the two-level ticketing configuration model, now available for Azure DevOps.
- Selection of Ticket Project for Linking Findings: Manually select any project to link findings to existing tickets, bypassing restrictions and enhancing flexibility in vulnerability management.
- Business Unit Filter: Categorize vulnerabilities by business units for more organized and targeted filtering of risks.
- Exclusion Filtering: Filter findings based on “Any” aswell as “All” conditions, enhancing triaging capabilities and reducing the complexity of vulnerability management.
- CWE-Based Filtering: Quickly locate findings associated with specific Common Weakness Enumeration (CWE) codes for more effective remediation.
- Owner-Based Filtering: Prioritize findings based on Application and Environment ownership or monitor other users’ findings for improved team management.
- Filter by “Deployed in Environment” for All Assets: Search for assets deployed in specific environments with this filter, available in the “All Assets” section.
Integrations
- Enhanced Lacework Container Management: Fetch running container information or container images depending on asset type selection through Lacework integration, enhancing scanner integration reports.
- REST API Enhanced to Use Asset Tags for Deployments: Deploy components using service asset tags, streamlining the deployment process.
Other Components
- Added CVE and CWE Columns to Findings and Vulnerabilities: Easily compare and target findings with specific CVEs and CWEs, enhancing contextual understanding.
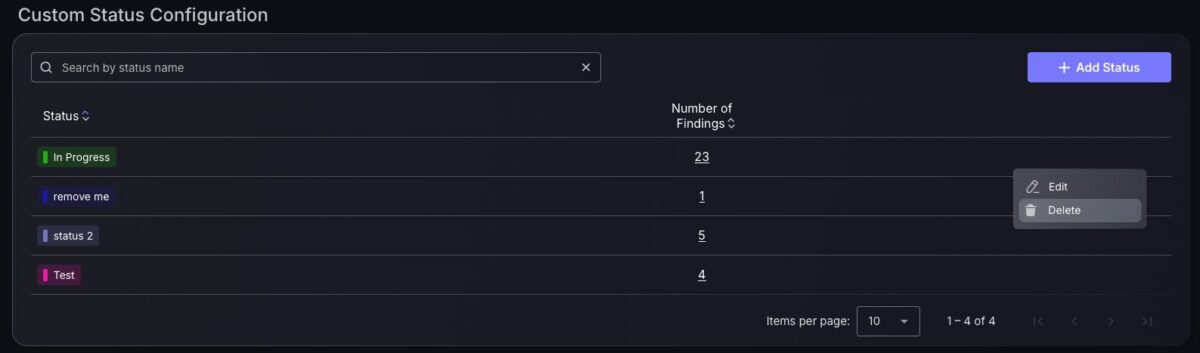
- Improved Finding’s Custom Status Management: Define custom status tags for next level customisation through the Custom Status Configuration panel.
Contents
ToggleGet in control of your Application Security posture and Vulnerability management
Revolutionizing Security Posture Management with Phoenix Security
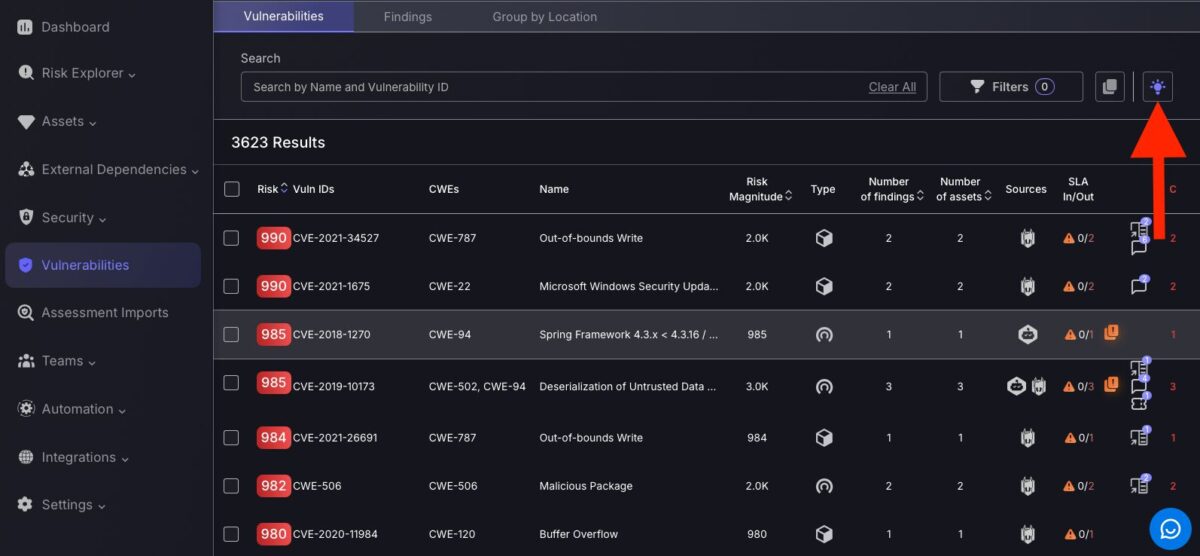
Quick access Insights Panel
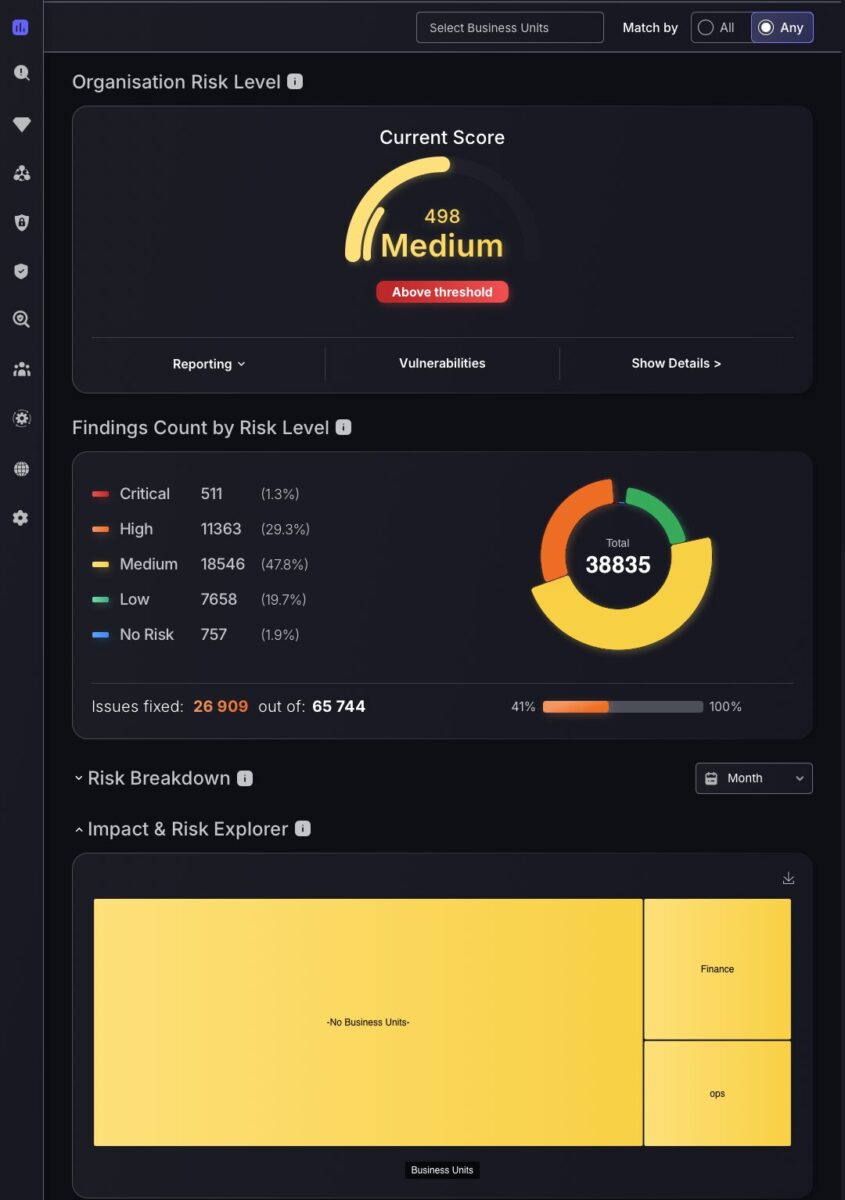
New Impact and Risk Explorer side panel: We’ve made assessing impact easier than ever before. The new Insight Intelligence panel allows you to reveal the blast radius of specific findings, vulnerabilities and assets. This is the side panel that opens on the Findings, Vulnerabilities and Assets pages when you click the new “bulb” icon on the top-right to open a series of heatmaps and an impact breakdown table.
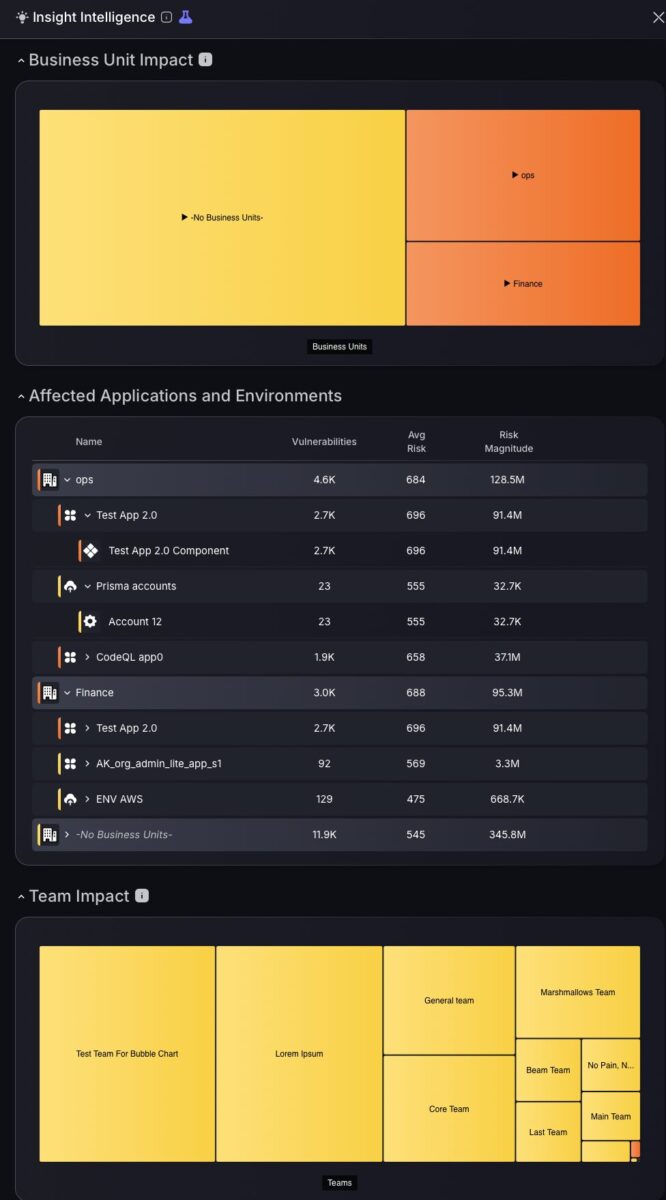
Explore areas affected using the business impact tab to visualise how vulnerabilities are distributed across different business units and empower yourself to take action faster. Peel back layers of vulnerability on the heatmap by clicking on different business units to reveal apps and environments affected; click further and pinpoint specific components affected using risk score metrics.
For a more comparative visualisation of applications and risk profiling, the Affected applications and environments table is the place to look. This expandable data table with nested groupings accommodates contextual risk exposure analysis using risk metrics columns such as: Vulnerabilities (scale), Average Risk score, Risk Magnitude score. For ease of navigation there are even shortcuts accessible by clicking the icons on the right of each application or environment entry. For example, by clicking on the diamond icon a shortcut will be executed to take you to the asset page with this business unit pre-filtered.
Assessing team impact is essential to maintain a stable security posture, which is why we have included a team impact heatmap to visualize team security posture and assess associated risk metrics.
Business Unit Insights Now Built Into Your Dashboard
Enhanced Impact and Risk Explorer: Prioritise what matters most using the enhanced Impact and Risk Explorer. We’ve enhanced our risk explorer to segregate branches of vulnerabilities by business units to easily monitor organizational impact. The size of each business unit is proportional to its impact/criticality to ensure business units are adequately visualized according to the scale of components affected. Not to worry about neglecting high-risk business units, as colour-coded segregation ensures no vulnerabilities are left unnoticed.
Stay informed, stay in control, and prioritize with precision.
Asset and Vulnerability Management
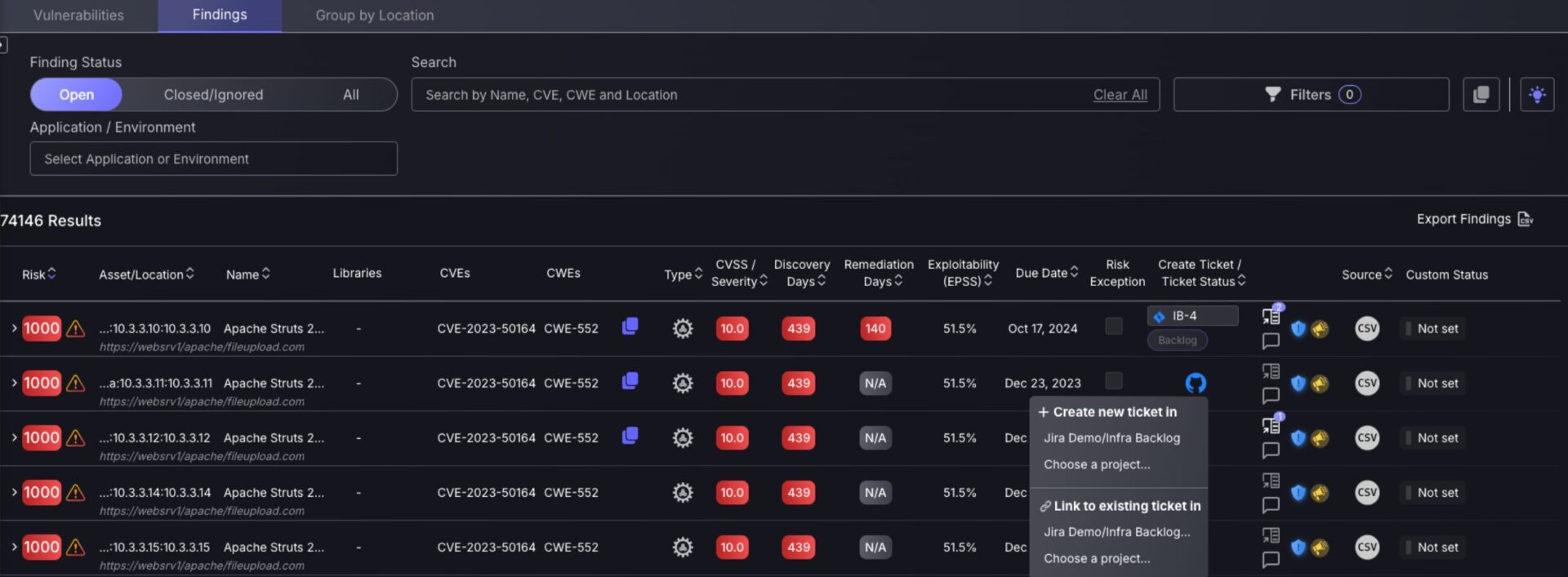
Link findings to existing tickets for GitHub and ServiceNow
We’re happy to announce new extensions to our ticketing integration capabilities. With the previous development of being able to link findings to existing tickets, Phoenix security has now expanded the collection of ticketing platforms for which this feature is available – you can now use GitHub and ServiceNow to streamline remediation workflows with complete flexibility.
Multi-finding tickets for ADO
The two-level ticketing configuration model offers flexible control by allowing you to associate entire applications and environments with a specific project while seamlessly enabling granular exceptions to be configured at the component level. Enabling multiple findings to be assigned to one ticket introduces a reduced workflow complexity by allowing users to customize ticketing groups in ways that are specific to their workflow methods. The introduction of multi-finding tickets for Azure DevOps elevates customization possibilities to an even greater extent.
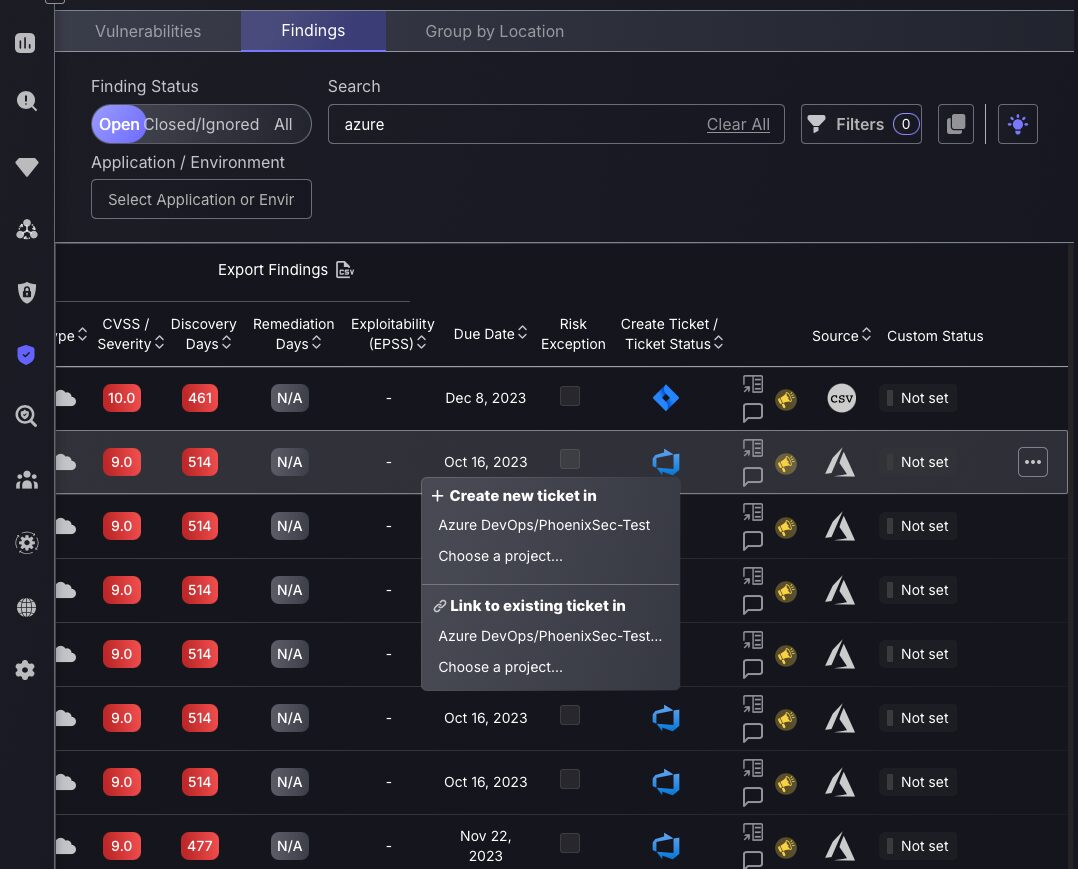
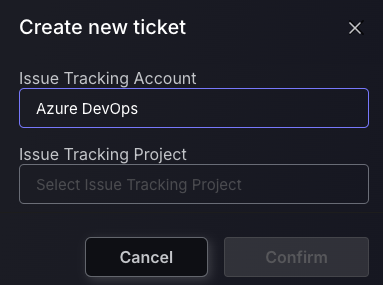
Allow selection of ticket project when linking findings to existing tickets
The Phoenix security ASPM platform is continuously being enhanced to optimise flexibility and reduce workload. The ticketing system just got even better with the flexibility to choose any project to link an existing ticket to. This mechanism ensures that in exceptional cases, where a finding needs to manually be assigned to an existing ticket that is not in the project associated with the Application or Component, that users can choose which integration and project to use to select the target ticket.
Users are no longer restricted to link findings to tickets in the project configured for the Application or Component! We have bypassed this process to make the workflow more flexible and Vulnerability management quicker than ever!
New Business Unit Filter
Phoenix Security has always offered a powerful set of filtering capabilities for findings. With the introduction of the all new Business Unit categorization we have integrated this as a filter category to allow organizational risk to be filtered with ease. Filtering capabilities at Phoenix are ever growing with the consistent introduction of new features and ways to categorise vulnerabilities. Filtering Vulnerabilities, assets and Findings by business unit allows you to search for findings in a conventional way that segregates findings in a more organizational business manner.
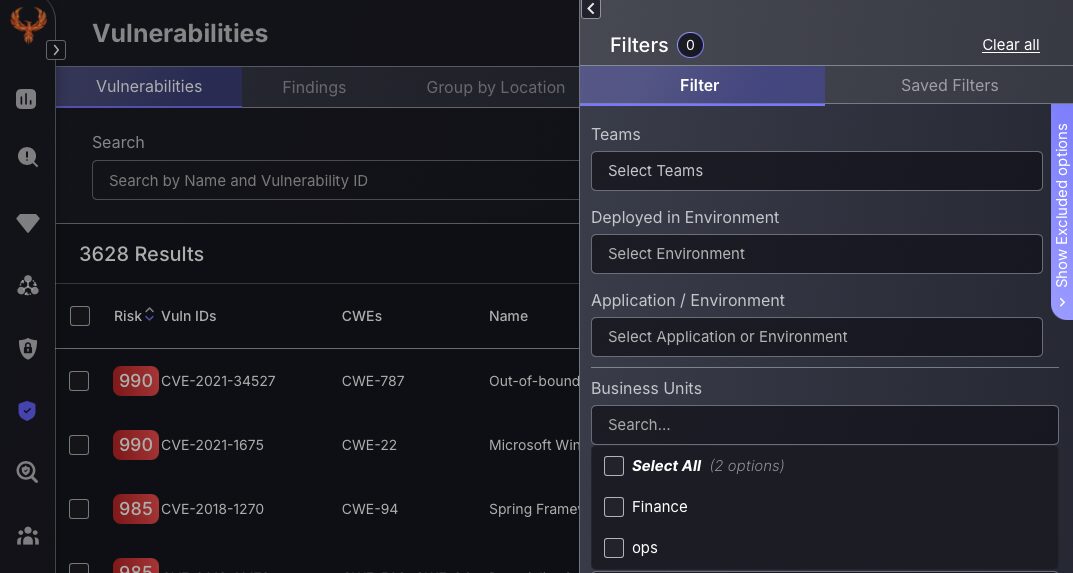
Exclusion Filtering just got better
At Phoenix Security, we never fail to introduce advanced features to enhance your triaging capabilities. The Excluded Options extension within the filter side panel provides extended functionality for filtering detailed findings and vulnerabilities. By pressing the blue tab on the right side of the screen, you will reveal an alternate filtering menu to exclude specific categories. This now includes the option to add exclusion filters that match findings that match Any condition, as well as All conditions. The “All” feature acts as an AND, excluding a finding only if all exclusion filters have been met; this was the previous behaviour. The “Any” feature, on the other hand, acts as an OR, excluding a finding if at least one of the conditions is matched.
New CWE-Based Filtering
As Phoenix Security is under continuous improvement of our vulnerability management capabilities, Phoenix now allows users to quickly search for findings that are linked to specific CWEs. This streamlines the process of locating specific findings with known vulnerabilities and remediations by using Common Weakness Enumeration codes, bridging the gap between different security team vulnerability classification standards by providing an abundance of filters to choose from.
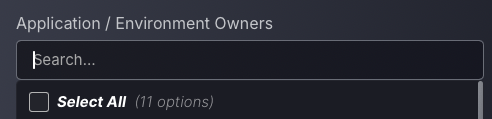
New Owner Based Filtering
With the all new Application and Environment Owner filter you can prioritise findings based on apps assigned to you or even monitor other user’s findings to keep on top of your team and prioritize what matters. You can select one or multiple users to customize your filtering, this feature is even available in the exclusion filtering section for advanced filter configuration.
Filter by “Deployed in Environment” for All Assets
Phoenix Security is dedicated to ensuring that everyday tasks are as efficient and straightforward as possible. To accomplish this goal, filtering capabilities are continuously being expanded and enhanced to consider every scenario where a specific vulnerability needs to be found, reducing the cognitive load of manually scanning for specific features. To make searching for assets deployed in a specific environment as straightforward as possible, we have included this as a filtering option in the “All Assets” section of the “Assets” panel.
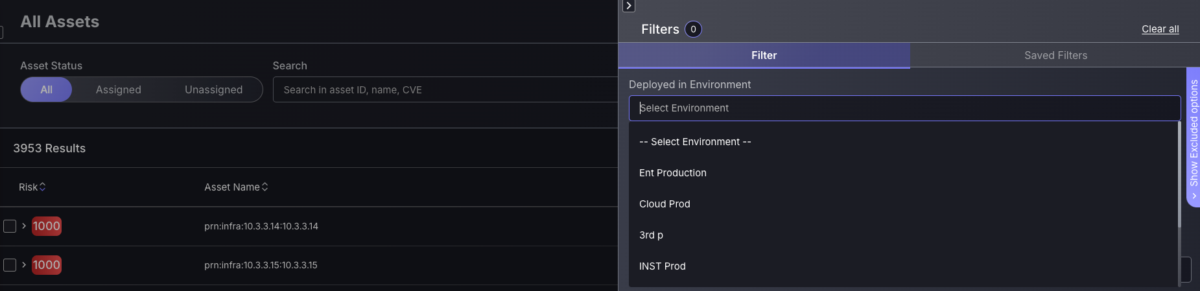
This filter is only available in the All Asset page, since it aims to select assets from the Components (software) and Services (containers, runtime) that are linked by deployment. The other asset screens are dedicated to specific types of assets, and they can’t display this combination of types.
Integrations
Enhanced Lacework Container Management
At Phoenix Security we have an expansive selection of compatible scanner integrations, allowing you to get the most out of our software no matter what your scanning preferences are. We are dedicated to ensuring that as scanners release new features, we keep in sync with these advancements and accommodate the latest improvements in our software. This is why we have included asset type selection into our Lacework integration configuration to enable the syncing of currently running container information depending on your asset type selection. Not only will this release allow you to fetch running container information but also container images to expand your capabilities by providing in-depth scanner integration reports.
REST API enhanced to use asset tags for Deployments
Component deployment has never been so easy. Phoenix Security has introduced a new feature in the REST API which allows you to select a Service to deploy to not just using the service’s own tags, but also allows you to use the service assets’ tags for selection. Tags are essential for teams to track and classify findings in their own ways and with this new feature it couldn’t be easier.
Others Enhancements
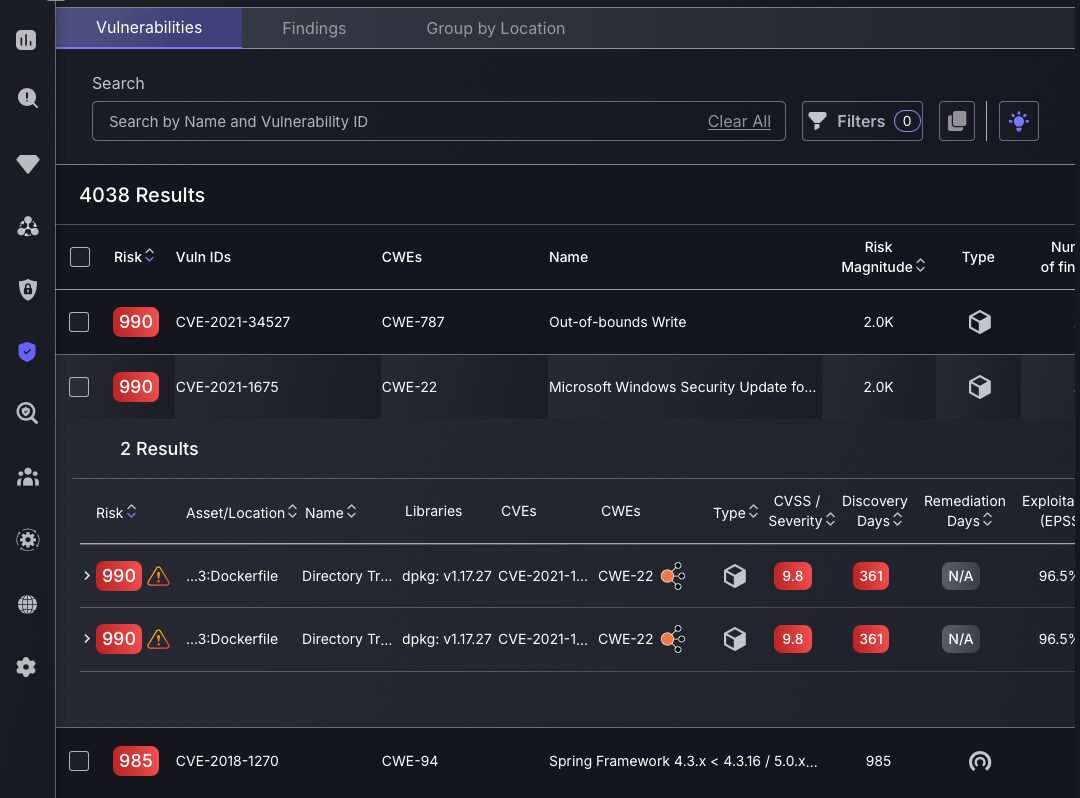
Added CVE and CWE columns to Findings and Vulns
Phoenix Security’s ASPM platform always prioritizes what is displayed based on years of experience in the industry and relevance to the given situation. That’s why we have added the CWE column to the vulnerability table to ease searching for specific vulnerabilities, not just by using the filtering option. Sometimes, filtering for specific CWEs can blind you from the complete picture, as similarities can easily be spotted using the table and used to contextualize the problem, whereas filtering can narrow down your options and make it harder to draw links.
To ensure CVEs are not overlooked, we have added this column to the findings sub-table within a vulnerability to allow for easy comparison and targeting of findings with specific CVEs. The CVE for a specific vulnerability can also be found within its vulnerability ID.
Improved findings Custom Status management
Custom status management offers more flexibility and alignment with your internal security processes by providing the option for users to define customized status tags for findings. Users can define status tags in the Custom Status Configuration panel within the Settings > Organisation section, and they can now safely delete previously defined tags. To ensure complete customization, even when a finding has been marked as a false positive or mitigated, users can set custom statuses in these circumstances — enabling precise organisation for closed tickets.