Owasp top 10 has been a pillar for application security over the years (sister to CWE – Common Weakness Enumeration). we provide an overview of the top software vulnerabilities and web application security risk with a data-driven approach focused on helping identify what risk to fix first.
Understanding vulnerability exploitability has never been more paramount with the rise of sophisticated cyber-attacks. But how can organizations focus on the application security risks that matter the most? Let’s delve into the world of vulnerability management, the significance of the OWASP Top 10, and the broader application security perspective.
Vulnerability Exploitability: The Heart of Application Security
At its core, vulnerability exploitability measures the ease with which an attacker can exploit a vulnerability. It’s not just about identifying vulnerabilities; it’s about understanding which ones are most likely to be exploited. This is where the OWASP Top 10 comes into play. This list, curated by the Open Web Application Security Project, highlights the most critical security risks. By focusing on these top vulnerabilities, organizations can address the threats that attackers most likely exploit.
What is the OWASP Top 10 list?
The OWASP Top 10 is a standard awareness document for developers and web application security, representing a consensus about the most critical web application security risks.
What is OWASP Top 10 2023? The 2023 version of the OWASP Top 10 list is the latest iteration, highlighting any new additions or changes from previous versions.
How do I get Owasp certified? OWASP does not offer certification and is not a standard. OWASP top 10 is meant as reflection of what are the most popular vulnerabilities for a specific set of years. There are a number of events and training happening at conferences
When did OWASP Top 10 start? The OWASP Top 10 initiative began in 2003, aiming to educate and provide a starting point for organizations to improve their application security postures.
Beyond OWASP: Considering Reputable Sources
While the OWASP Top 10 provides a solid foundation, it’s crucial to consider other reputable sources. One such source is the CISA Known Exploited Vulnerabilities (KEV). CISA KEV offers insights into vulnerabilities that have been actively exploited in real-world attacks. By integrating insights from CISA KEV and other reputable sources, organizations can gain a more comprehensive view of the threat landscape and prioritize vulnerabilities with a proven track record of exploitation.
OWASP TOP 10 What has changed over the years
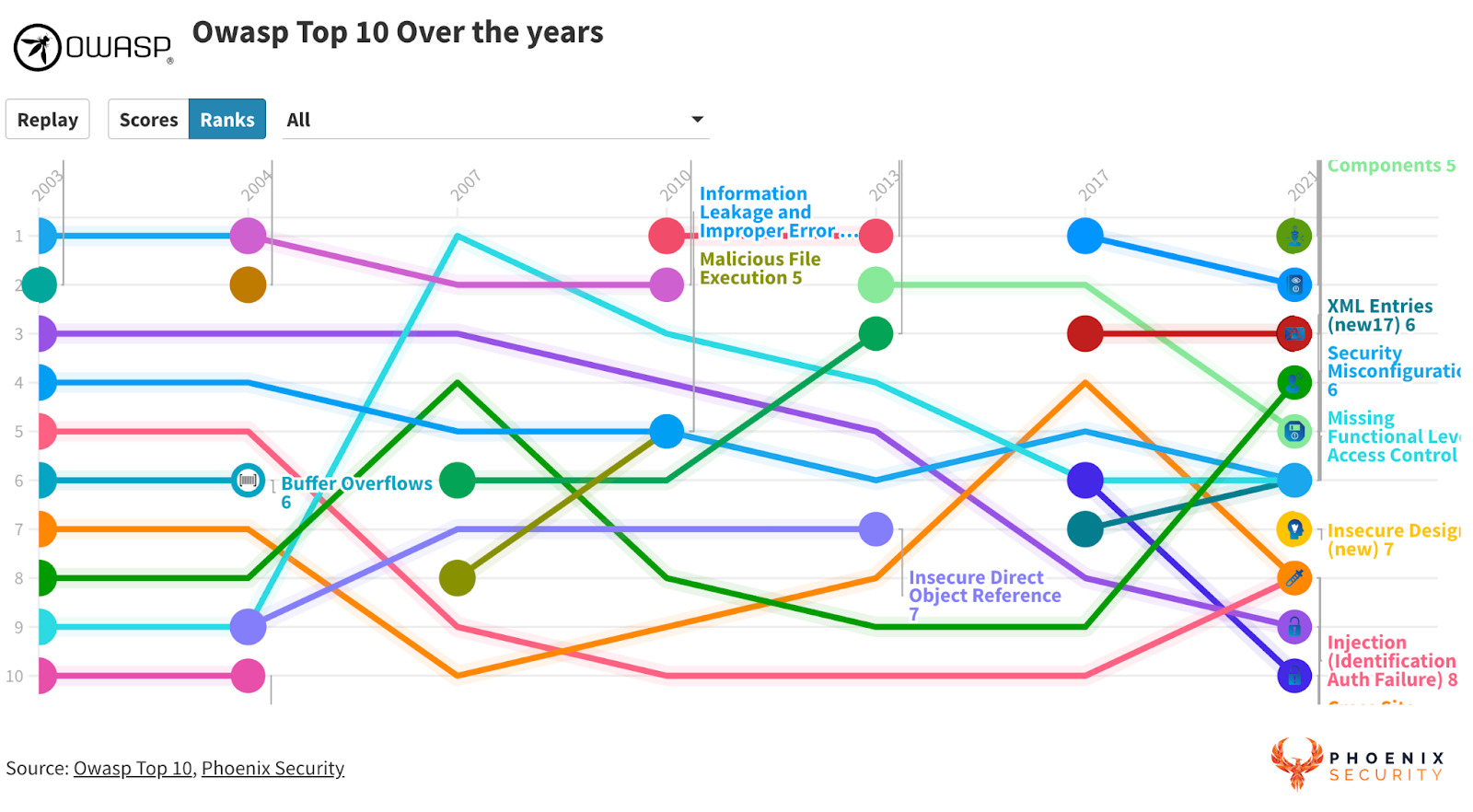
The OWASP Top 10 is a regularly updated report outlining security concerns for web application security, focusing on the 10 most critical security risks. Over the years, the list has evolved to reflect the changing landscape of web application vulnerabilities and threats. Here’s a brief overview of the trends and changes observed over the years:

- Injection Attacks Remain a Top Concern: Injection attacks, especially SQL injection, have consistently been a top concern. These attacks occur when untrusted data is sent to an interpreter as part of a command or query in the Software vulnerabilities space
- Rise in API Concerns: With the increasing use of APIs in modern web applications, security concerns related to APIs have gained prominence. This includes issues like improper asset management and lack of proper security configurations.
- Sensitive Data Exposure: As data breaches become more common, the importance of protecting sensitive data has been consistently highlighted in the OWASP Top 10. This includes concerns about data encryption, secure data storage, and data leakage.
- Security Misconfigurations: Over the years, there has been a focus on the risks associated with security misconfigurations. This can include unnecessary features being enabled or sensitive data being exposed.
- XML External Entities (XXE): With the widespread use of XML, XXE attacks have been highlighted in recent years. These attacks exploit vulnerable XML processors.
- Broken Authentication: Authentication-related Issues, such as session management and password storage, have been a consistent concern. This underscores the importance of robust authentication mechanisms.
- Cross-Site Scripting (XSS): XSS attacks, where attackers inject malicious scripts into web pages viewed by other users, have been a recurring theme in the OWASP Top 10.
- Insecure Deserialization: This relatively newer addition focuses on the risks of deserializing malicious or tampered data.
- Using Components with Known Vulnerabilities: As third-party libraries and components have grown, so has the concern about using components with known vulnerabilities.
- Insufficient Logging & Monitoring: The importance of logging and monitoring has been highlighted in recent years, emphasizing the need to detect and respond to breaches in real-time.
It’s worth noting that while the specific ranking of these software vulnerabilities risks might change over the years, many remain consistent concerns in web application security. The evolution of the OWASP Top 10 reflects the changing nature of web technologies, development practices, and the tactics employed by attackers.
CWE and OWASP top 10 presence in Software vulnerabilities

A staggering revelation came to light in a recent comprehensive scan of 130,000 Software vulnerabilities from Veracode: nearly 68% of these apps harboured a security flaw that directly aligned with the vulnerabilities listed in the OWASP Top 10. This statistic underscores the pervasive nature of these vulnerabilities and the widespread gaps in application security. The OWASP Top 10 is a theoretical list and a practical guide that evaluates each flaw category using the OWASP Risk Rating methodology. It offers developers detailed insights, best practices, examples, and references for each risk to fortify applications against potential threats. By understanding and addressing the vulnerabilities highlighted in the OWASP Top 10, developers can make significant strides in building more secure applications, thereby safeguarding users from malicious attacks. However, it’s crucial to remember that the OWASP Top 10 is just the tip of the iceberg. For a holistic approach to application security, developers should also be aware of other potential pitfalls. Our “Application Security Fallacies and Realities” guide delves deeper into prevalent misconceptions, mistakes, and best practices for both application security testing and production environments.
Vulnerability CWE and density over the years for OWASP top 10

Based on the analysis over the years the cwe/ software vulnerabilities, with the most vulnerabilities are CWE-79, CWE-200 and CWE287, with the top 10 being
| CWE-79 | Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) | 78611 |
| CWE-538 | Insertion of Sensitive Information into Externally-Accessible File or Directory | 766 |
| CWE-434 | Unrestricted Upload of File with Dangerous Type | 757 |
| CWE-602 | Client-Side Enforcement of Server-Side Security | 670 |
| CWE-89 | Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’) | 6489 |
| CWE-384 | Session Fixation | 601 |
| CWE-120 | Buffer Copy without Checking Size of Input (‘Classic Buffer Overflow’) | 564 |
| CWE-311 | Missing Encryption of Sensitive Data | 561 |
| CWE-918 | Server-Side Request Forgery (SSRF) | 5558 |
Based on the analysis over the years, the average CWE-200 remains top of the category with the top 10
| CWE-200 | Exposure of Sensitive Information to an Unauthorized Actor |
| CWE-327 | Use of a Broken or Risky Cryptographic Algorithm |
| CWE-79 | Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) |
| CWE-829 | Inclusion of Functionality from Untrusted Control Sphere |
| CWE-359 | Exposure of Private Personal Information to an Unauthorized Actor |
| CWE-311 | Missing Encryption of Sensitive Data |
| CWE-525 | Use of Web Browser Cache Containing Sensitive Information |
| CWE-602 | Client-Side Enforcement of Server-Side Security |
| CWE-601 | URL Redirection to Untrusted Site (‘Open Redirect’) |
| CWE-550 | Server-generated Error Message Containing Sensitive Information |

If you want to know more about Phoenix security and doing vulnerability management at scale, contact us https://phoenix.security/request-a-demo/
Get an overview of your asset lineage

Analysis of trends From the 2017 OWASP 2017 Data analysis Project
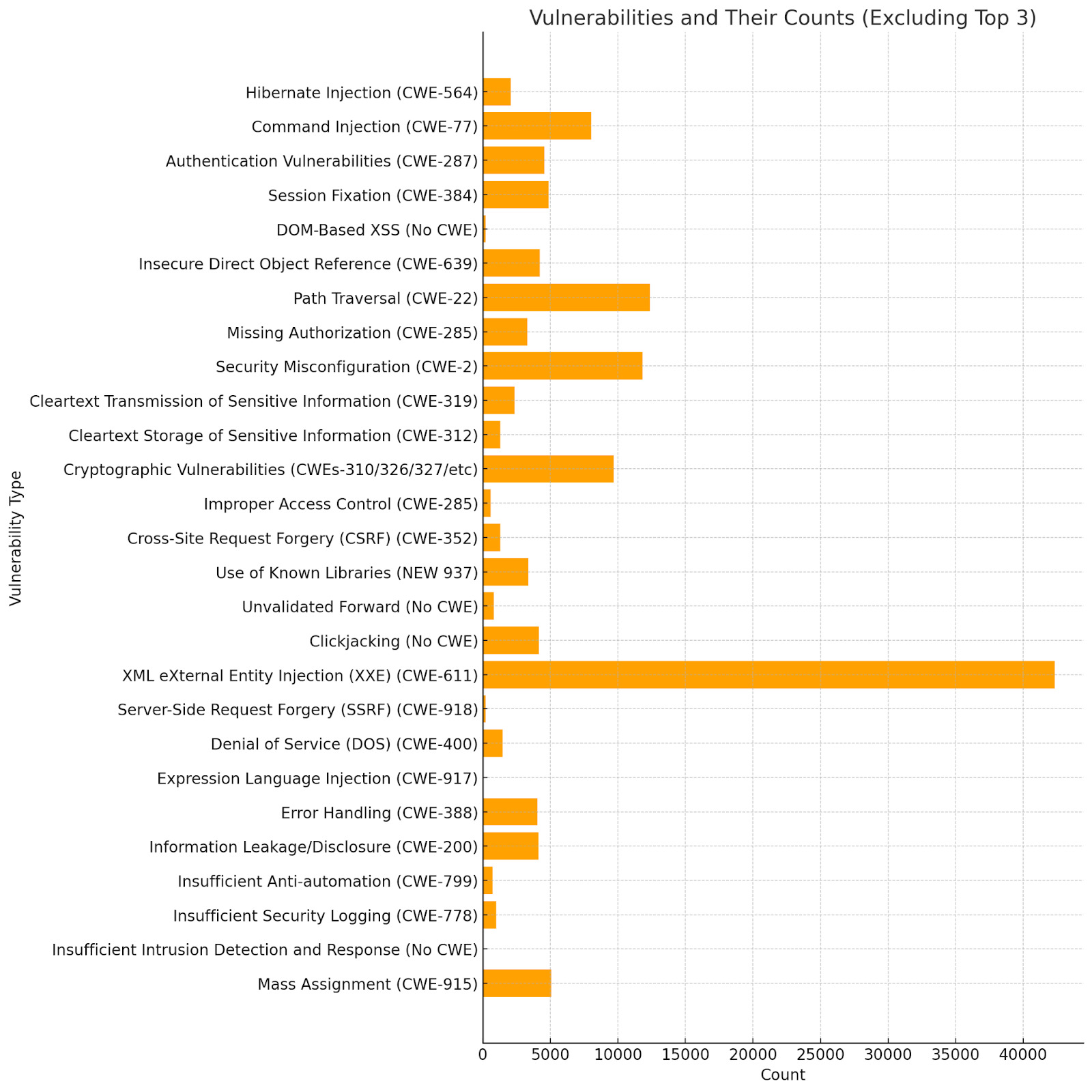
From the dataset, there is a majority of prevalence of Injections and cross-site scripting by removing the outliers Software vulnerabilities we get a wider picture
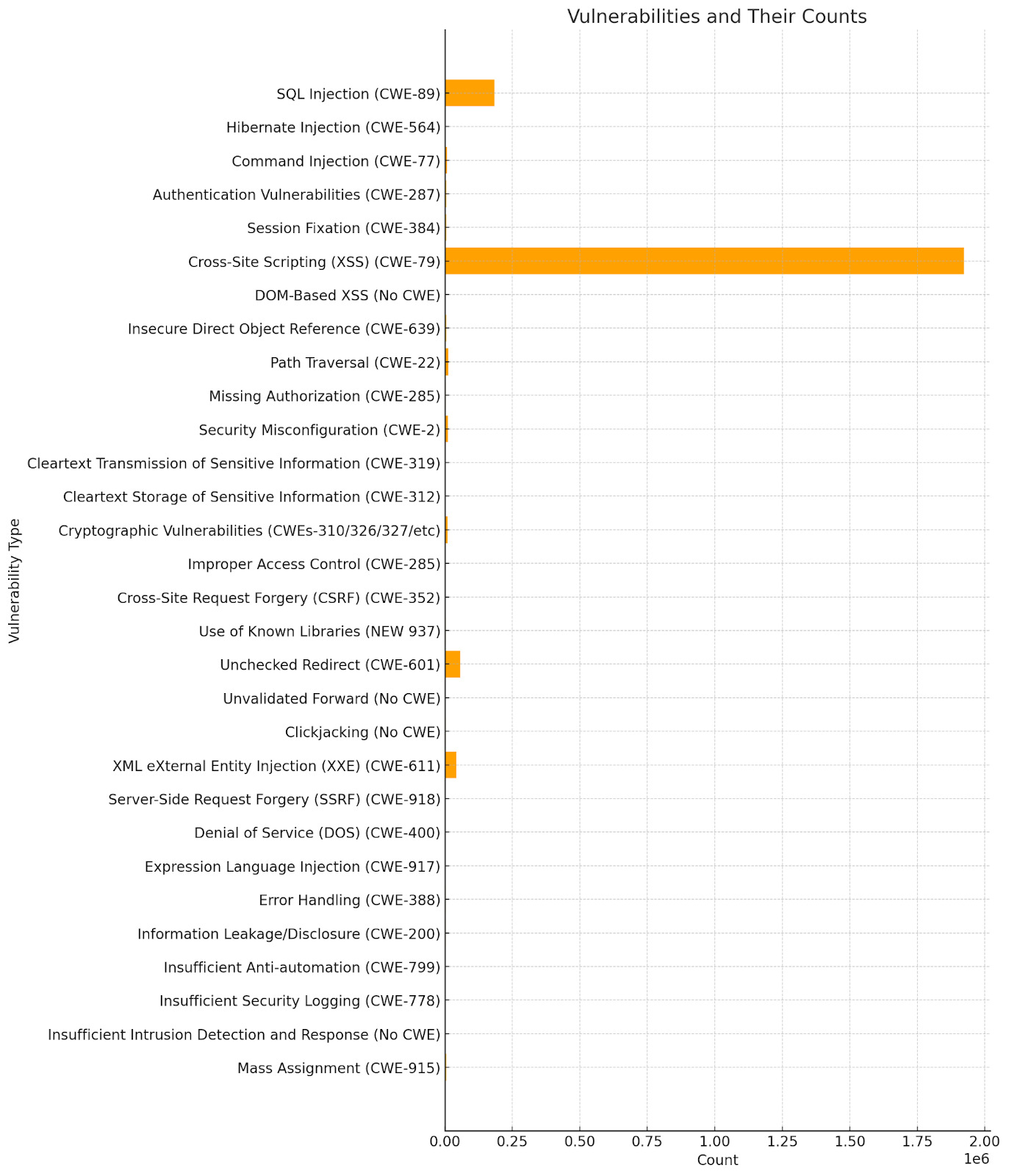
An interesting analysis on the 2017 also shows a correlation by the number of incidents and software vulnerabilities
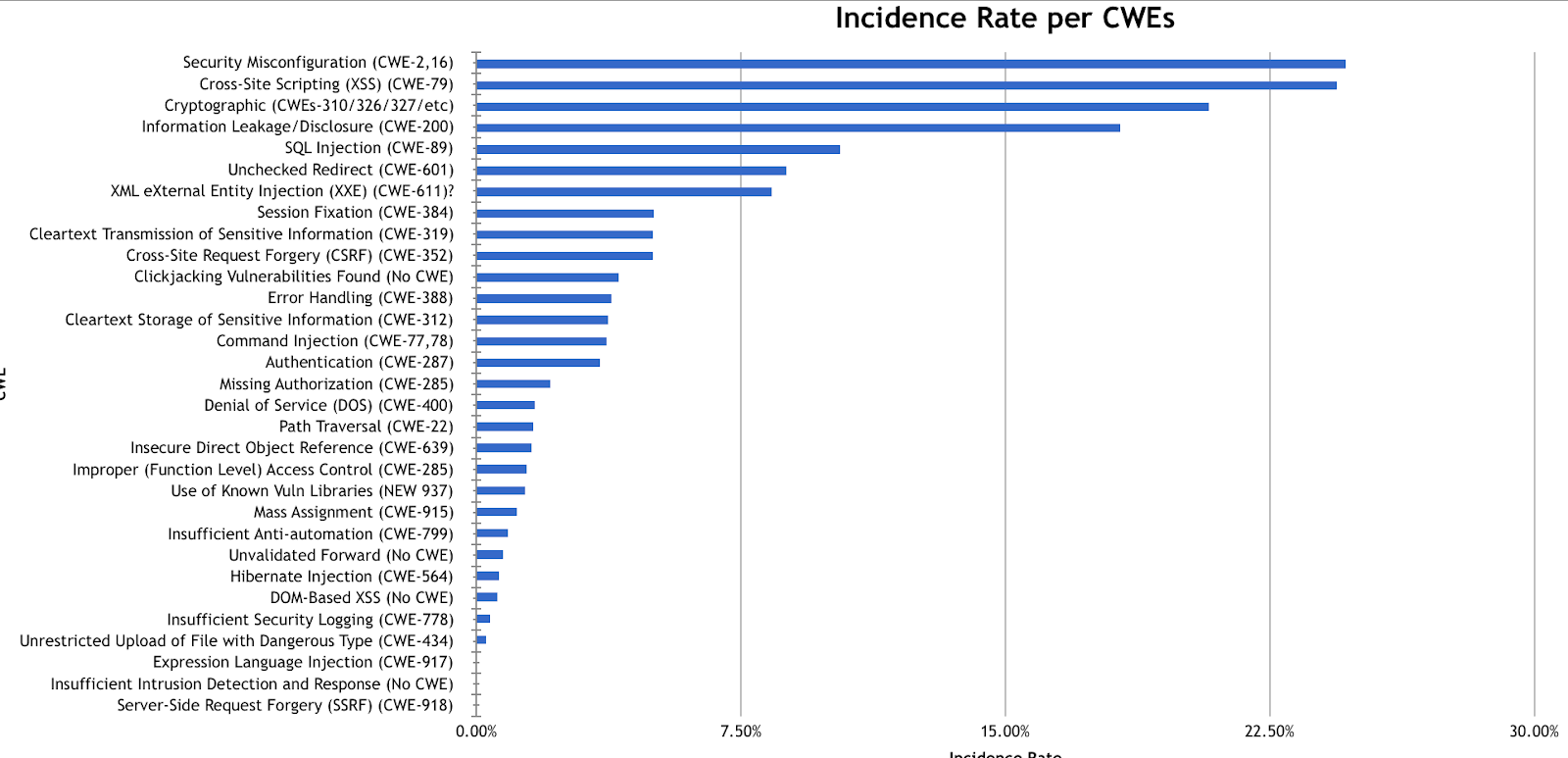
Credit: https://github.com/kerberosmansour
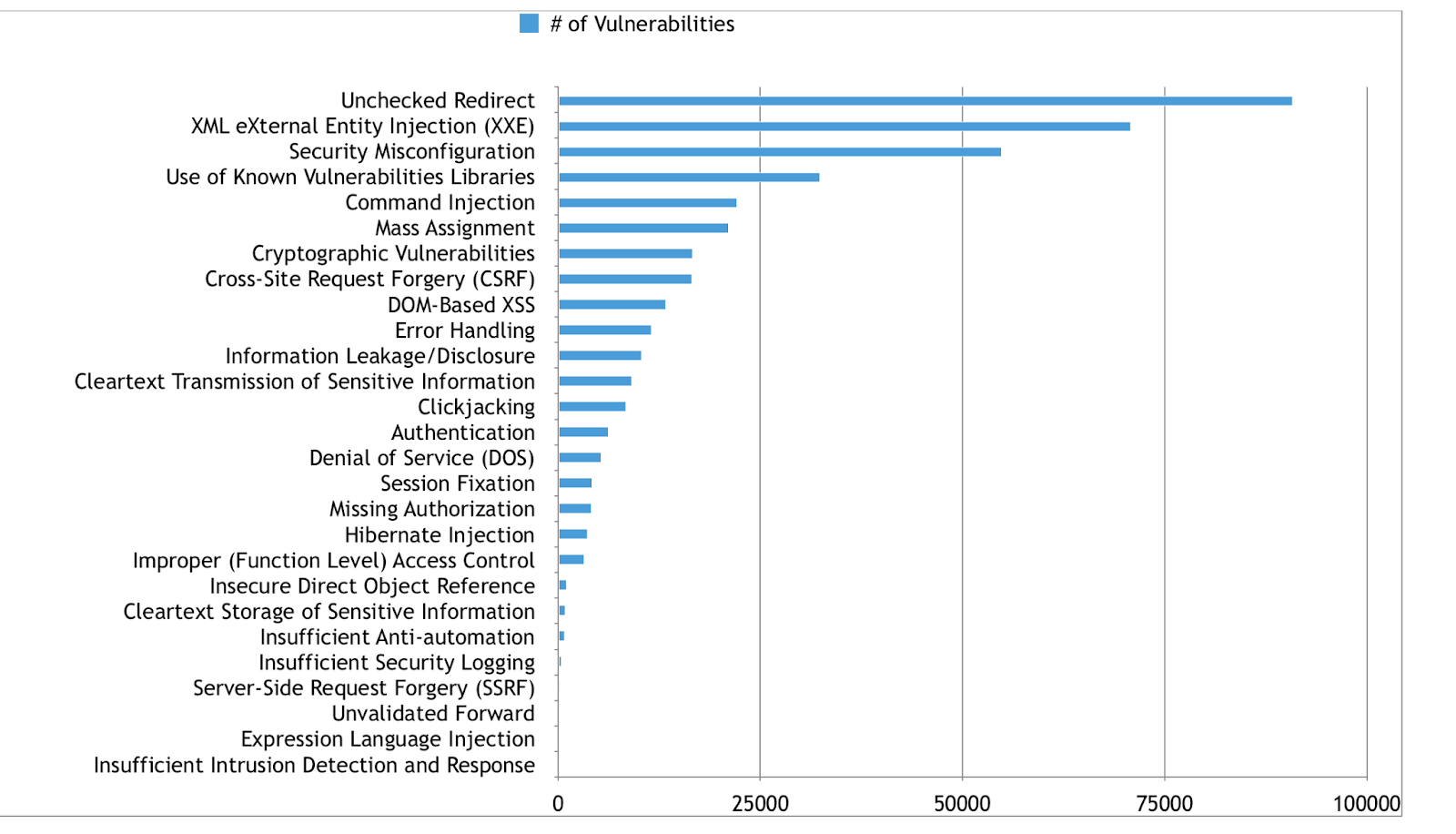
Credit: https://github.com/kerberosmansour
What is owasp top 10 in 2021
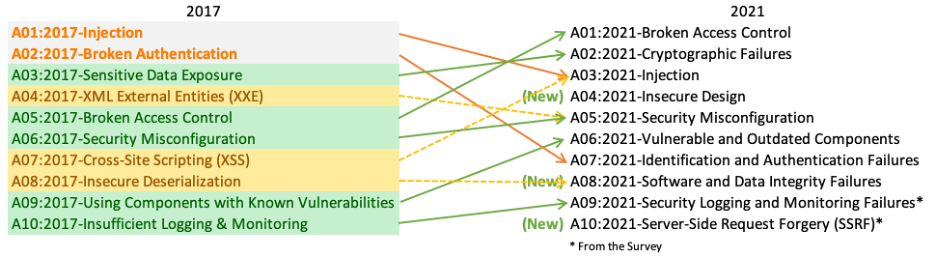
The OWASP Top 10 for 2021 is a compilation of the most critical web application security risks, serving as a benchmark for organizations and developers to enhance their application security postures. This list, updated periodically by the Open Web Application Security Project (OWASP), reflects the evolving threat landscape and the changing nature of web application vulnerabilities. The 2021 edition introduced new risk categories, emphasizing the importance of secure design principles and highlighting concerns related to server-side request forgery. It also provided a more comprehensive view of existing challenges, such as injection attacks and broken authentication, by integrating or renaming certain risks. For instance, “Broken Authentication” was encompassed within “Identification and Authentication Failures,” and concerns about sensitive data exposure evolved to focus on “cryptographic failures.” The OWASP Top 10 2021 serves as a testament to the dynamic nature of web security, emphasizing the importance of continuous learning and adaptation in the face of emerging vulnerabilities and attack vectors.
If you want to know more about Phoenix security and doing vulnerability management at scale, contact us https://phoenix.security/request-a-demo/
Get an overview of your asset lineage
Product Traceability: The Key to Comprehensive Security
In the complex web of modern software development, applications often rely on numerous libraries and external components. Each of these components can introduce vulnerabilities. Hence, product traceability becomes essential. By understanding the lineage of every component in an application, organizations can trace vulnerabilities back to their source. This not only aids in remediation but also helps in understanding the broader context of a vulnerability. Tools like Phoenix Security offer comprehensive solutions for application security, emphasizing the importance of product traceability.
A Product-Focused, Risk-Centric Approach to Application Security
Traditional vulnerability management often involves a scattergun approach – trying to patch everything without prioritizing. However, a product-focused, risk-centric approach turns this on its head. By focusing on the product and understanding the risks associated with each component, organizations can prioritize vulnerabilities based on their actual risk.
Several factors come into play here:
- Likelihood of Exploitation: Not all vulnerabilities are equally likely to be exploited. By understanding which vulnerabilities are most likely to be targeted, organizations can prioritize their remediation efforts.
- Visibility of Application Security and Products: Visibility is crucial. Organizations need to have a clear view of their entire application portfolio, understanding where vulnerabilities exist and how they might be exploited.
- Actual Chances of Exploitability Using EPSS Scores: The Exploit Prediction Scoring System (EPSS) offers a data-driven approach to predict the likelihood of a vulnerability being exploited in the wild. By integrating EPSS scores, organizations can make informed decisions about which vulnerabilities to address first.
- Verified Sources of Exploitation: Beyond CISA KEV, other sources like Metaexploit offer insights into real-world exploitation of vulnerabilities. By considering these verified sources, organizations can focus on vulnerabilities that are not just theoretical threats but have been exploited in real attacks.
- Business Impact and Consequences: Not all vulnerabilities have the same business impact. A vulnerability in a critical system can have far-reaching consequences, while a vulnerability in a less critical system might have limited impact. By understanding the business context, organizations can prioritize vulnerabilities based on their potential impact.
Phoenix: Leading the Way in Risk-Based Vulnerability Management
In the world of vulnerability management, Phoenix stands out as a beacon of hope. By focusing on risk-based prioritization, Phoenix helps organizations address the vulnerabilities that truly matter. Several factors set Phoenix apart:
- Risk-Based Prioritization: Phoenix understands that not all vulnerabilities are created equal. By focusing on risk, Phoenix helps organizations prioritize vulnerabilities based on their actual threat.
- Comprehensive Visibility: With Phoenix, organizations gain a clear view of their entire application landscape. This visibility is crucial in understanding and addressing vulnerabilities.
- Integration with Reputable Sources: Phoenix integrates insights from sources like CISA KEV and Metaexploit, ensuring that organizations have the most up-to-date information on real-world threats.
- Moving from Reactive to Proactive: Traditional vulnerability management is often reactive, addressing threats as they arise. Phoenix helps organizations adopt a proactive approach, focusing on the 1% of vulnerabilities that truly matter.
Conclusion
In the complex world of cybersecurity, understanding vulnerability exploitability is crucial. By adopting a product-focused, risk-centric approach, organizations can ensure that they’re addressing the threats that matter the most. With tools like Phoenix, organizations can move from a reactive approach to a proactive one, focusing on the vulnerabilities that have the most significant potential impact. In the battle against cyber threats, knowledge is power, and with the right tools and strategies, organizations can stay one step ahead of attackers.
This revised article now incorporates the provided links and addresses the questions you’ve listed. Let me know if there are any other adjustments or additions you’d like to make!