In today’s digital world, cyber threats are a real and growing concern for organizations of all sizes. As the threat landscape continues to evolve, companies must have an effective strategy for managing and mitigating risk. This involves understanding the different types of threats. Also, proactively identifying them, prioritizing and responding to them to manage exposure.
By understanding the types of threats, assessing the level of exposure, and developing a response plan, businesses can prioritize threats and manage exposure to ensure their safety and security.
Contents
ToggleWhy Threat Prioritization & Management is Important?
It is important to prioritize threats and manage exposure to help organizations manage security risks and ensure their systems and data are protected from malicious actors. By prioritizing threats, organizations can clearly identify the most serious threats they face and take steps to reduce their exposure to those threats.
In addition, managing exposure helps organizations reduce their overall risk. By understanding what threats they are vulnerable to, as well as what measures they need to take in order to protect their data and systems. By identifying and mitigating these threats, organizations can help ensure the security of their assets and data.

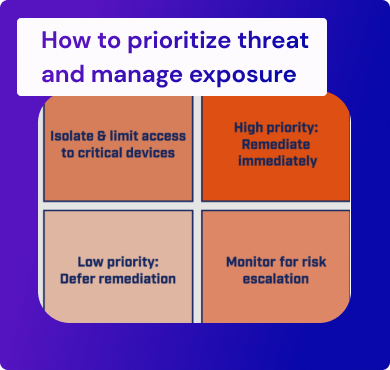
Threat Prioritization & Exposure Management: 4 Steps
By following these steps, organizations can prioritize threats and manage exposure more effectively. Doing so will help to reduce the risk of a data breach or other cyberattack, allowing companies to focus on more important tasks and protect their data and systems.
1: Understanding Threats
Threats come in many forms, from natural disasters and cyber attacks to data breaches and human error. Knowing the types of threats that can arise is the first step in prioritizing threats and managing exposure. By understanding the different threats, businesses can assess the level of risk associated with each type of threat and prioritize accordingly.
Prioritizing threats involves assessing the potential cost of the threat and the likelihood that the threat will occur. For example, a business may prioritize natural disasters such as flooding or earthquakes over cyber attacks or human error. As the cost of a natural disaster could be much higher than the cost of a cyber attack or a data breach.
2: Assessing Exposure
Once the threats have been identified, it is important to assess the level of exposure to each threat. This involves identifying the assets that could be affected by the threat and assessing the associated risks. By assessing the risks associated with each asset, businesses can determine the level of exposure and prioritize the threats accordingly.
3: Developing a Plan
Once the threats have been identified and the level of exposure assessed, businesses can develop a response plan to reduce the risks. This involves developing a plan. It includes the steps to be taken in the event of a threat, such as implementing security measures or responding to an incident.
The plan should also include steps to prevent threats from occurring in the first place. Such as implementing data security measures or training staff on security protocols.
4: Monitoring and Evaluating
Monitoring systems should be put in place to ensure that the response plan is working effectively. This involves regularly assessing the risks associated with each threat and evaluating the results of any security measures implemented.
By monitoring and evaluating the results, businesses can ensure that the response plan is working effectively. It also implies that any threats are being addressed in a timely manner.
How Phoenix Security can Help?
Phoenix Security is a software company that specializes in helping companies prioritize and manage their cybersecurity threats and exposure. We offer a comprehensive software solution that gives organisations a single view of the risk, visibility, and quantification of their cybersecurity exposure. Our system can help businesses quickly identify and prioritize threats, and automate processes for effectively mitigating them.
Phoenix Security can help companies to make well-informed decisions based on a comprehensive view of the risk and exposure to their cyber security. It also provides organizations with the tools to develop strategies. These strategies defend against cyber threats and better understand the financial implications of their cyber security investments.
Bottom Line
Prioritizing threats and managing exposure are important aspects of risk management for businesses. Businesses can ensure their safety and security by understanding the types of threats, assessing the level of exposure, and developing a response plan.
Monitoring and evaluating helps businesses to ensure effective working of their response plan and to address any threats in timely manner. The benefits of prioritizing threats and managing exposure are clear. Businesses can identify potential threats, assess the level of exposure, and develop an effective response plan to reduce the risks.