
Sysdig has taken another step forward in strengthening container security through its latest integration with Phoenix Security, providing advanced Application Security Posture Management (ASPM) for modern cloud-native environments. This integration brings together Sysdig’s powerful runtime security with Phoenix Security’s contextual reachability analysis, allowing teams to map vulnerabilities from code to running containers with precision.
Version: 3.35.0
Release Date: 24 September 2024
Knowledge Base: Sysdig Integration with Phoenix Security
Overview
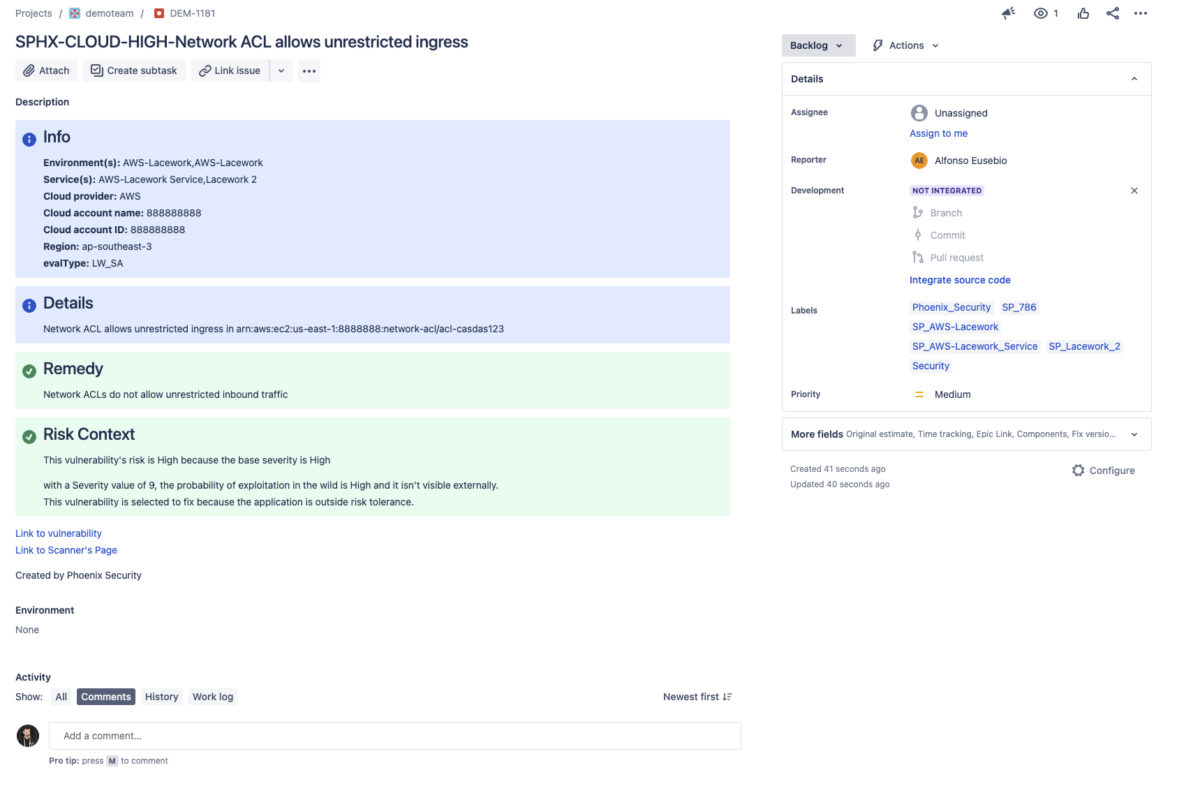
With the integration, Sysdig users can now leverage contextual deduplication across both code and runtime environments. Focusing on the actual in-use libraries and their potential impact reduces noise from duplicated alerts, enabling faster and more informed decision-making. Phoenix also provides advanced reachability analysis, allowing security teams to map vulnerable containers directly to their respective applications and prioritizing critical risks with full visibility across their environment.
Why this feature?
By integrating Sysdig with Phoenix Security, organizations can supercharge their container security by identifying reachable vulnerabilities in runtime environments while minimizing false positives. The power of contextual deduplication in this integration goes beyond traditional scanning, offering insights into actual exploitable vulnerabilities, not just theoretical ones.
Key Features
Contextual Deduplication from Code to Running Container:
• Minimize alert fatigue with Sysdig’s runtime security by eliminating duplicate alerts across codebases and running environments.
• Use Phoenix to focus on vulnerabilities tied to in-use libraries, reducing the noise from non-actionable alerts.
• Prioritize vulnerabilities that directly impact container runtime with contextual data that links to the relevant application.

Runtime Reachability Analysis:
• Map vulnerabilities to specific running containers and applications, providing clear visibility into which components are exposed.
• Phoenix Security enhances Sysdig’s reachability analysis, offering deeper insights into which parts of your application are truly at risk.
• Efficiently manage vulnerabilities and secure containers across your cloud environment with actionable intelligence.

Enhanced Application Security Posture Management (ASPM):
• Gain comprehensive ASPM by combining Sysdig’s security monitoring with Phoenix Security’s contextual capabilities.
• Aggregate and prioritize security vulnerabilities across your cloud-native applications, providing a holistic view of security risks.
• Reduce time-to-remediation by identifying critical vulnerabilities and linking them to actual runtime conditions.
Cross-Platform Container Security:
• Ensure security across AWS, Azure, and Google Cloud Platform (GCP) by integrating Sysdig with Phoenix for consistent container security posture management.
• Real-time monitoring and reachability insights across your containerized environments, regardless of where they are deployed.
Why Choose Sysdig with Phoenix Security?
Sysdig offers state-of-the-art container security, enhanced by Phoenix Security’s ability to contextualize vulnerabilities and reachability. With features like contextual deduplication and runtime reachability analysis, organizations can focus on what matters most: safeguarding applications from real, exploitable threats, rather than theoretical issues.
The intuitive interface of Sysdig, combined with Phoenix’s advanced security capabilities, delivers robust protection for your cloud-native infrastructure, ensuring you stay ahead in securing your containers from development to production.
Running Containers:
• Real-time monitoring and vulnerability assessment of running containers in GCP, AWS, and Azure.
• Ensure your containers in Google Cloud are as secure as a bank vault.
Cloud Misconfiguration:
• Detect and prioritize misconfigurations in Google Cloud Security Center, AWS, and Azure that could expose your infrastructure to security risks.
• Get actionable insights to secure your entire cloud environment.

Key Features
- Prioritized Vulnerabilities Across Container Images:
- Automatically rank vulnerabilities in your container images based on severity and impact.
- Make informed decisions on which issues to tackle first.
- Automatic tracking of application exposure
- Tickets tracking with aggregation of results
- Running Containers:
- Real-time monitoring and vulnerability assessment of running containers.
- Ensure your containers are as secure as a bank vault.
- Contextual Deduplication:
- Phoenix dynamically deduplicates containers from code to cloud
- Cloud Misconfiguration:
- Identify and prioritize cloud misconfigurations that could pose security risks.
- Get actionable insights to secure your cloud infrastructure.
- 280+ Integrations Supported:
- GCP becomes one of the 280+ integrations supported by Phoenix Security.
- Benefit from the contextual aggregation of data from code to cloud.
Additional Resources
For a comprehensive guide on leveraging this integration, check out our Lacework Integration with Phoenix Security
Support
Need help? Contact our support team at support@phoenix.security.















