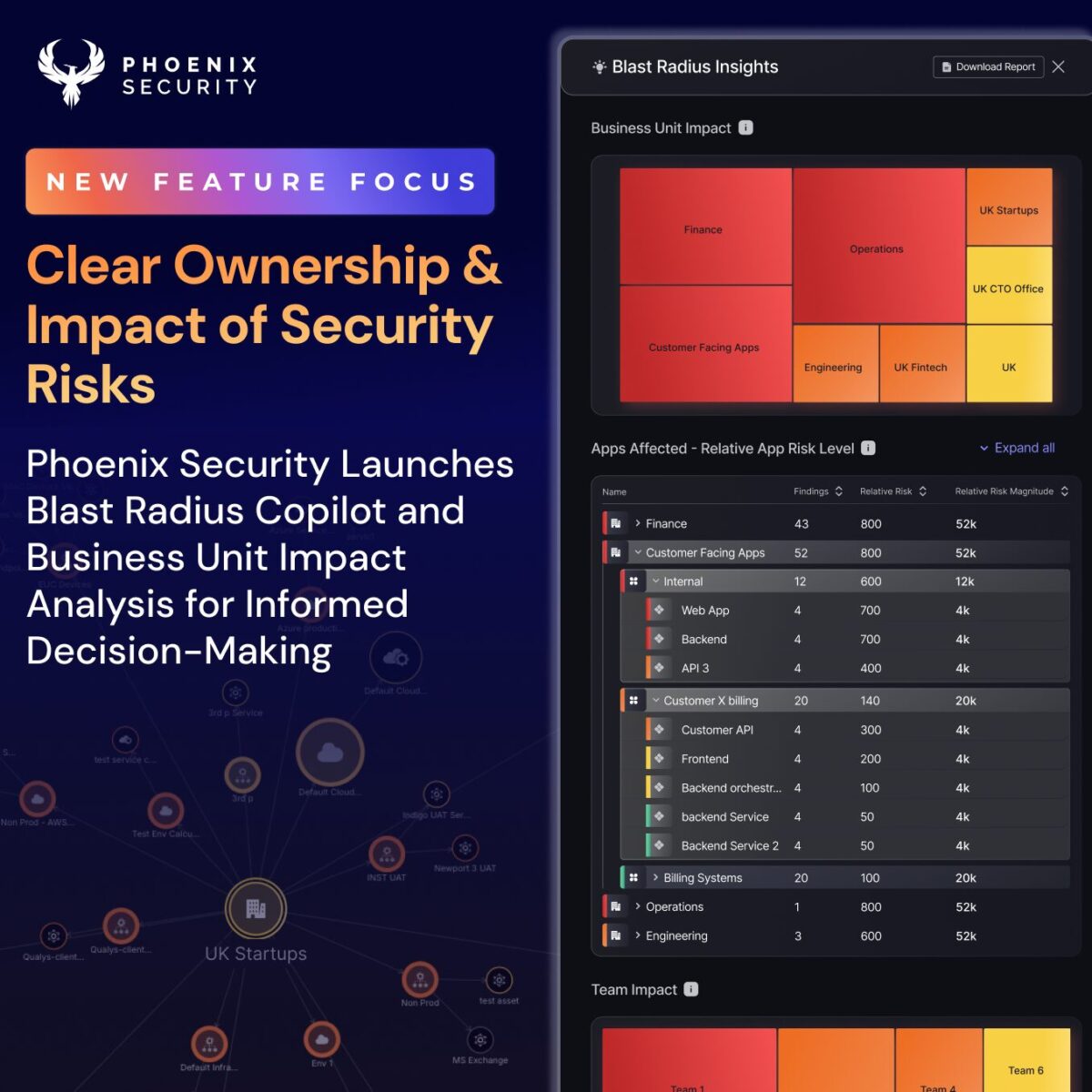
Executives often ask one simple question: “Who owns this risk, and how bad is it?” Phoenix Security delivers a clear answer. The newest release provides Blast Radius Analysis and Business Unit Impact Analysis, elevating ASPM, application security, and root cause investigations to a level that meets boardroom expectations.
Senior leaders frequently wonder how an unpatched library like Log4j can disrupt multiple lines of business or departments. Blast Radius Analysis reveals the extent of that threat. It maps exactly which business units, teams, and applications are affected. That approach offers transparency into the knock-on effects of vulnerabilities, which frequently slip past basic scans.
Key Features
- Blast Radius Analysis
- Assess the impact of vulnerabilities on entire business units.
- Identify which applications and teams are affected by specific vulnerabilities.
- To understand the extent of the risk, drill down into details for a particular vulnerability, such as Log4j.
- Business Unit Impact Analysis
- Analyze aggregated risk per team, business unit, and application owner.
- Understand the mean time to resolution and aggregated exposure for each business unit.
- Explore the applications under each business unit to identify those carrying the most risk.
- Campaign Creation
- Create targeted campaigns based on identified vulnerabilities.
- Address root causes of vulnerabilities with upcoming features focused on root cause analysis.
Business Unit Impact Analysis takes a broader perspective. Stakeholders gain aggregated data on risk, mean time to resolution, and overall exposure. This feature helps executives prioritize resources where they matter most, fulfilling compliance obligations. Application security owners can also inspect shared platforms—those universal resources that often mask where a flaw originates.
Root cause analysis stands as a crucial element. Remediation efforts don’t stop at patching one file; they dive into patterns, repeated issues, and the fundamental reasons why certain flaws emerge again and again. This focus on underlying causes aligns with modern vulnerability management philosophies, ensuring that security teams move from firefighting mode toward longer-term prevention.
Executives value tools that optimize cross-team collaboration. Phoenix Security provides a single platform where each vulnerability is correlated with its rightful owner, leaving minimal room for confusion. By doing so, organizations cut through the noise, target the biggest threats, and demonstrate a rigorous approach to compliance.
Use Cases
- Identifying Vulnerability Impact: Quickly determine which business units and applications are affected by a vulnerability, allowing for prompt remediation.
- Risk Assessment: Evaluate the aggregated risk across business units, helping to prioritize security efforts based on the most critical vulnerabilities.
- Operational Insights: Understand the operational dynamics of shared platforms and how multiple applications interact with vulnerabilities.
There’s always a joke about security teams being the corporate messengers of doom. With this release, that image shifts. Multiple dashboards allow different teams to see how their actions impact the bigger picture. One flawed library doesn’t derail the entire operation when ownership is clear, data is actionable, and the path to resolution is direct.
A resilient security posture calls for accountability, rapid response, and strategic vision. Phoenix Security’s latest offering delivers precisely that. Whether the task involves satisfying regulators, meeting internal deadlines, or preventing an incident from gaining headlines, these new analyses streamline the process. Executive champions and application security owners alike will find the clarity they need—no guesswork, no blame game, and fewer late-night emergencies.
Welcome to vulnerability management that resonates with the boardroom and the engineering floor. Phoenix Security’s Blast Radius Analysis and Business Unit Impact Analysis form the backbone of this update, offering a roadmap for precise root cause analysis, robust ASPM implementation, and measurable progress in cybersecurity programs. Enjoy a more straightforward path to compliance, cut down on repeated patch cycles, and keep potential threats fully in check.
Conclusion
The new features from Phoenix Security empower organizations to manage vulnerabilities at scale, ensuring that security teams can effectively prioritize and address risks across their business units. For more information or to schedule a demo, please refer to the links provided in the comments or the hyperlink above.
Minimize the vulnerability risk and act on the vulnerabilities that matter most, combining ASPM, EPSS, and reachability analysis.

Organizations often face an overwhelming volume of security alerts, including false positives and duplicate vulnerabilities, which can distract from real threats. Traditional tools may overwhelm engineers with lengthy, misaligned lists that fail to reflect business objectives or the risk tolerance of product owners.
Phoenix Security offers a transformative solution through its Actionable Application Security Posture Management (ASPM), powered by AI-based Contextual Quantitative analysis. This innovative approach correlates runtime data, combines it with EPSS and other threat intelligence, and applies the right risk to code and cloud, delivering a prioritized list of vulnerabilities.
Why do people talk about Phoenix Security ASPM?

• Automated Triage: Phoenix streamlines the triage process using a customizable 4D risk formula, ensuring critical vulnerabilities are addressed promptly by the right teams.
• Actionable Threat Intelligence: Phoenix provides real-time insights into vulnerabilities’ exploitability, leveraging EPS and combining runtime threat intelligence with application security data for precise risk mitigation.

• Contextual Deduplication with reachability analysis: Utilizing canary token-based traceability for network reachability and static and dynamic runtime reachability, Phoenix accurately deduplicates and tracks vulnerabilities within application code and deployment environments, allowing teams to concentrate on genuine threats.
By leveraging Phoenix Security, you not only unravel the potential threats but also take a significant stride in vulnerability management, ensuring your application security remains current and focuses on the key vulnerabilities.