Overview
Phoenix Security ASPM now integrates full runtime risk telemetry and agentless cloud visibility through its latest expansion, powered by Orca Security. To support scalable DevSecOps this release enhances automation by combining deep code-level security with real-time insights across AWS, Azure, GCP, and Kubernetes — all within a single Application Security Posture Management (ASPM) platform.
Security and engineering teams can now detect, assign, and resolve vulnerabilities across code, infrastructure, and cloud workloads using a single streamlined workflow. The integration connects misconfigurations, secrets, identity risks, and code flaws with runtime exposure and business impact — all mapped in real time.
Release Date: 8 July 2025
Orca Runtime Risk Intelligence for DevSecOps Efficiency
Orca Security uses SideScanning™ to inspect workloads, containers, and cloud storage without requiring agents. Phoenix Security now pulls this data directly into its ASPM engine, where runtime signals are matched to ownership, context, and severity scoring.
To improve prioritization, the platform evaluates every finding based on deployment exposure and infrastructure reach. Whether a misconfigured storage bucket or an exposed credential in a running pod, the issue is ranked according to real-world risk.
Orca-Powered Workflow for Unified Vulnerability Management
1. Agentless Cloud Inventory and Risk Correlation
Orca continuously scans AWS, Azure, GCP, and Kubernetes environments. Phoenix Security ingests these findings and links them to code repositories, infrastructure components, and application assets. Teams no longer waste time triaging disconnected data across silos.
2. Prioritization Based on Runtime Exposure
Issues identified through SAST, SCA, or secrets scanning are enhanced with live environment telemetry. A dormant vulnerability in an unused image stays quiet. The same issue inside an exposed production container gets immediate priority.
3. Streamlined Cloud Misconfiguration Remediation
Excessive permissions, public-facing services, and open ports are now tied directly to their source in the codebase or infrastructure-as-code configuration. Phoenix assigns the issue to the asset owner, logs the remediation path, and tracks its progress in a single backlog.
4. End-to-End DevSecOps Coverage
From the first commit to deployment, all static and dynamic security issues now flow through one DevSecOps pipeline. Exception handling, SLA enforcement, and remediation tracking follow consistent policies across both application and cloud environments.
ASPM Optimization for Code-to-Cloud Security
The addition of Orca strengthens Phoenix Security’s ASPM platform across key DevSecOps domains:
- Orca-Driven Code-to-Cloud Security Visibility
Vulnerabilities are no longer viewed in isolation. They’re contextualized across the full stack with Phoenix Security and Orca, with live cloud data layered into prioritization logic. - Orca Data and Intelligent Deduplication, Assignment, and contextual prioritization by Phoenix Security
Developers see one issue per root cause. Security teams avoid alert fatigue. Owners are automatically identified by repository, branch, or cloud service role. - Full-Stack Security Graph Enriched by Orca vulnerabilities
Runtime risk, misconfigurations, SAST findings, secrets, and cloud permissions now feed into the same contextual risk engine, enabling a comprehensive, real-time view of the full-stack posture.
Now Available

Orca Security’s cloud runtime scanning and risk intelligence is live for all Phoenix Security ASPM customers on current version. The integration activates in minutes and supports hybrid and multi-cloud environments without agent overhead.
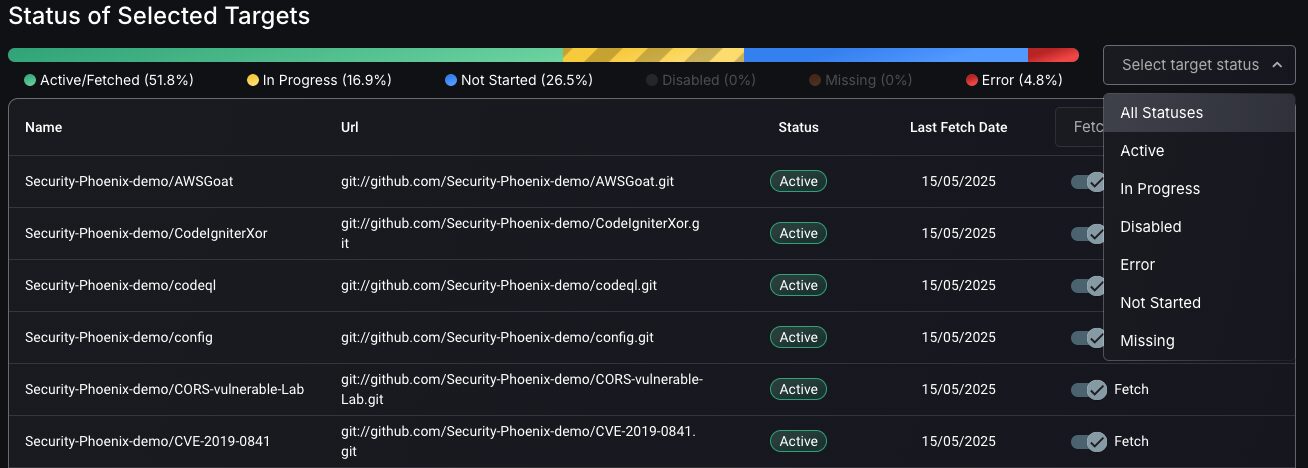
Phoenix allows users to track the status of targets through status management features e.g. In Progress, Disabled, etc.
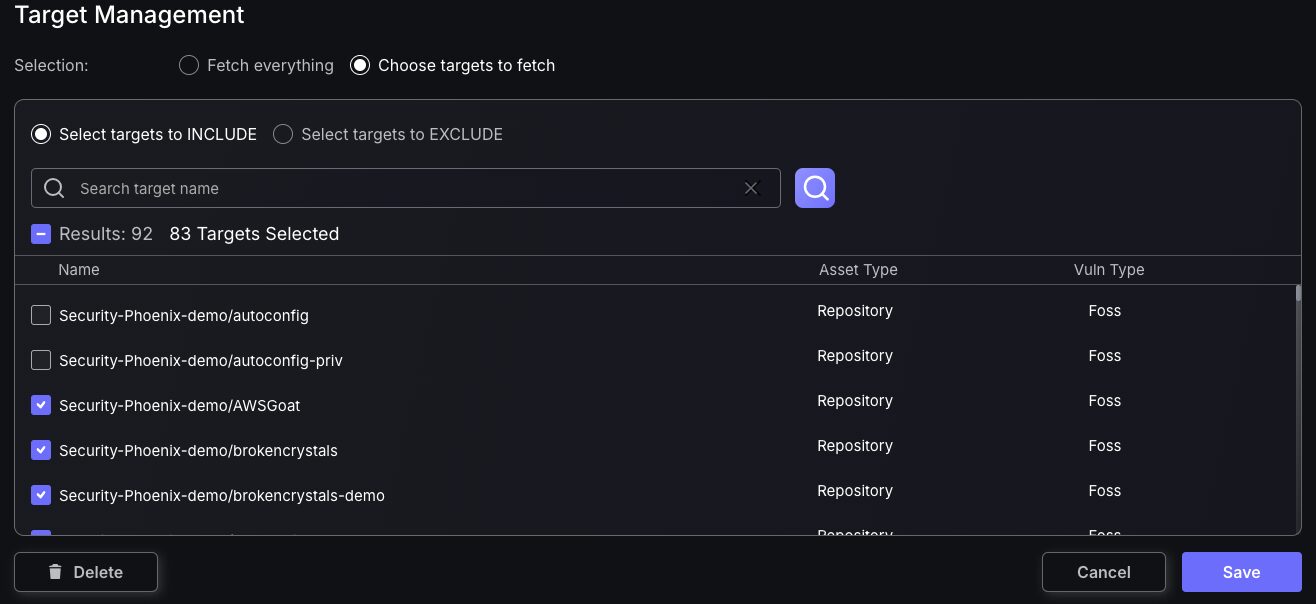
Target management feature enables users to customise assets being fed into Phoenix software by selecting targets to be fetch.
One platform. One risk model. Total visibility across code and cloud
Start mapping your application security posture across cloud and runtime environments — all from a single platform.
Visit the Phoenix Security Knowledge Base (Coming Soon) or contact your solutions engineer for rollout support.
Support
Need help? Contact our support team at support@phoenix.security.