LONDON, UK & CHARLOTTE, NC – April 2025 – Phoenix Security, the leader in Application Security Posture Management (ASPM), is raising the bar with the launch of its intelligent, human-aligned AI Agents. These AI Agents for ASPM and Vulnerability Management are designed to work alongside security teams – not replace them. They already show results: 98% less noise, 96–99% fewer criticals, and 430K+ engineering hours reclaimed for customers like ClearBank, Bazaarvoice, and others in retail and banking.
This isn’t about dumping AI on top of vulnerability data. It’s about precision, context and acceleration—turning raw findings into targeted and actionable steps. These steps fit directly into the way teams already operate. With AI Agents for ASPM and Vulnerability Management, this vision becomes a reality.
“Anyone can point an LLM at a CVE feed, have a side panel that creates a pretty diagram. We built AI agents that think like seasoned analysts—connecting vulnerabilities, ingesting context, delivering fixes developers can use immediately,” said Francesco Cipollone, CEO & Co-Founder of Phoenix Security.
Contents
ToggleThree Agents. One Mission: Multiply Analyst Impact
Phoenix’s AI-powered trio—The Researcher, The Analyzer, and The Remediator—work in concert to take security teams from detection to resolution. They do so with speed and surgical accuracy.
- The Researcher (available now) continuously monitors real-time threat intelligence, both public and private. It maps methodologies of attacks, such as MITRE&ATTACK, correlating vulnerabilities to active methodologies, ransomware campaigns, known threat actors, and attack methodologies. Proprietary models, developed in partnership with Google, deliver exploitation prediction on ransomware and likelihood of exploitation compensating EPSS metrics. It goes beyond CVE summaries, tracing root causes, and filtering the noise so teams can focus on true business-critical risks.
- The Analyzer models attack paths within the actual code-to-cloud environment, revealing which vulnerabilities are impacting the major risk categories. It delivers threat modelling and attack scenarios. All this is rooted in real data and real-time context, not just in theory.
- The Remediator transforms that intelligence into environment-specific actions, leveraging the researcher and the analyzer. It produces executable fixes, delivering remediation plans, and grouping vulnerabilities in plans considering impact. Additionally, it minimizes the noise by removing false positives. The remediation also works alongside you, producing compensating controls considerations based on the deployment context.
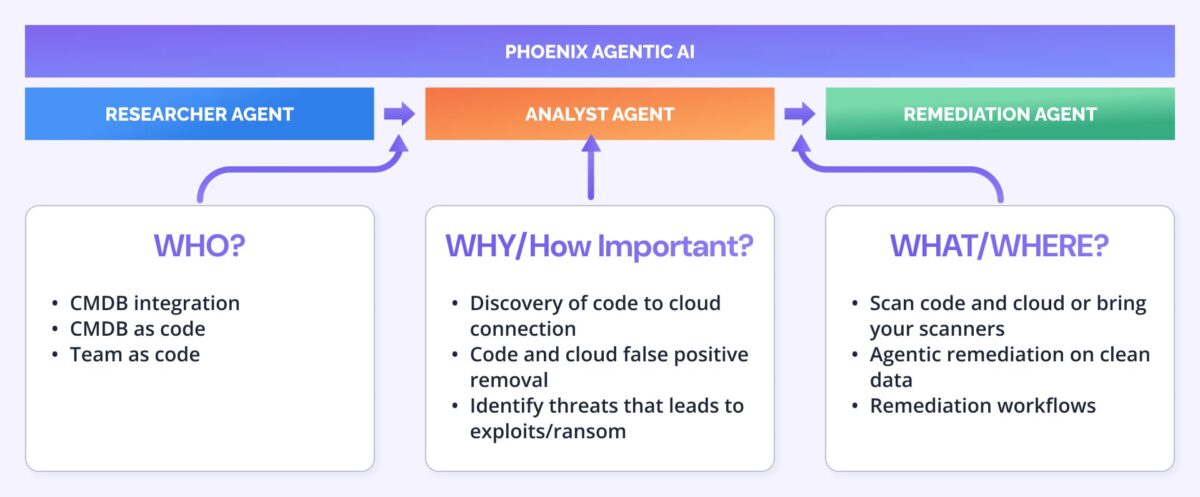
Application exposure management with agentic contextual remediation is crucial for effective ASPM and Vulnerability Management.
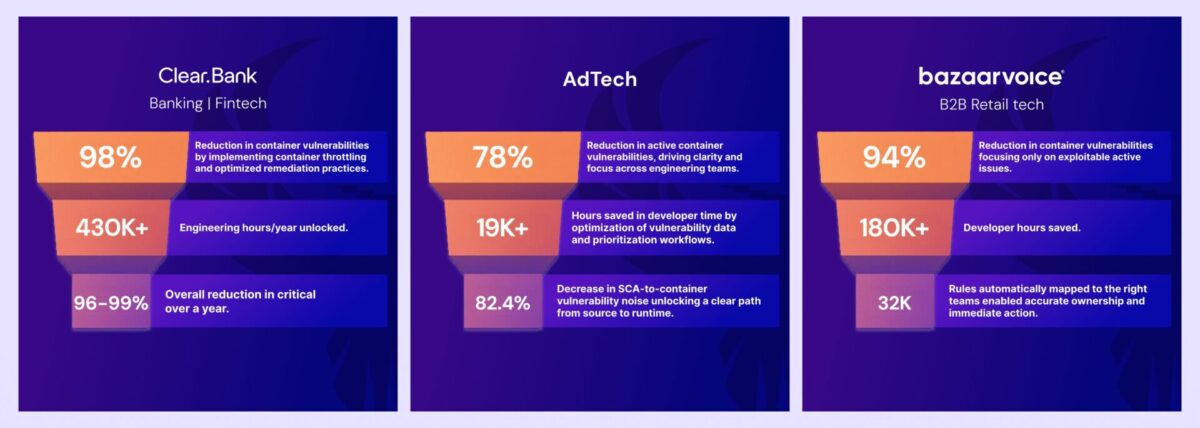
Proven Results Across Industries
- ClearBank cut container noise by 98%, eliminated up to 99% of criticals, and saved $2.6M in analyst time annually—equivalent to four hours per security engineer, every week.
- Bazaarvoice eradicated all critical vulnerabilities in two weeks and reduced high-risk findings by 40%, creating immediate alignment between security and engineering.
- Ad-Tech giant achieved a 78% reduction in container vulnerabilities. It also unified code and cloud visibility with AI Agents for ASPM and Vulnerability Management.
The Phoenix Difference: Threat-Centric, Context-Driven, Human-Aligned
While others push generic AI assistants, Phoenix Security’s agents enrich vulnerabilities with threat actor mapping, ransomware risk prediction and contextual remediation intelligence. The approach blends automation with analyst oversight, ensuring decisions are grounded in operational reality.
This agentic architecture, already proven to accelerate remediation 10x faster, allows CISOs and AppSec leaders to keep control while scaling their team’s capability. The use of AI Agents for ASPM and Vulnerability Management ensures that instead of chasing thousands of alerts, teams get a surgical set of prioritised actions per team. These actions are fully enriched with ownership, risk context and actionable fixes.
Phoenix Security’s AI Agents are already available to customers, with the Researcher live today. The Analyzer and Remediator will be rolling out in 2025. The result is faster remediation, measurable risk reduction and teams spending more time solving problems than sifting through noise.
Get on top of your code and container vulnerabilities with Phoenix Security Actionable ASPM

Organizations often face an overwhelming volume of security alerts, including false positives and duplicate vulnerabilities, which can distract from real threats. Traditional tools may overwhelm engineers with lengthy, misaligned lists that fail to reflect business objectives or the risk tolerance of product owners.
Phoenix Security offers a transformative solution through its Actionable Application Security Posture Management (ASPM), powered by AI-based Contextual Quantitative analysis. This innovative approach correlates runtime data with code analysis to deliver a single, prioritized list of vulnerabilities. This list is tailored to the specific needs of engineering teams and aligns with executive goals, reducing noise and focusing efforts on the most critical issues. Why do people talk about Phoenix

• Automated Triage: Phoenix streamlines the triage process using a customizable 4D risk formula, ensuring critical vulnerabilities are addressed promptly by the right teams.
• Contextual Deduplication: Utilizing canary token-based traceability, Phoenix accurately deduplicates and tracks vulnerabilities within application code and deployment environments, allowing teams to concentrate on genuine threats.
• Actionable Threat Intelligence: Phoenix provides real-time insights into vulnerabilities’ exploitability, combining runtime threat intelligence with application security data for precise risk mitigation.

By leveraging Phoenix Security, you not only unravel the potential threats but also take a significant stride in vulnerability management, ensuring your application security remains up to date and focuses on the key vulnerabilities.
















